
Table of Contents (Start)
- Topics
- Introducing SevOne
- Login
- Startup Wizard
- Dashboard
- Global Search - Advanced Search
- Report Manager
- Report Attachment Wizard
- Report Properties
- Report Interactions
- Instant Graphs
- TopN Reports
- Alerts
- Alert Archives
- Alert Summary
- Instant Status
- Status Map Manager
- Edit Maps
- View Maps
- FlowFalcon Reports
- NBAR Reports
- Logged Traps
- Unknown Traps
- Trap Event Editor
- Trap Destinations
- Trap Destination Associations
- Policy Browser
- Create and Edit Policies
- Threshold Browser
- Create and Edit Thresholds
- Probe Manager
- Discovery Manager
- Device Manager
- New Device
- Edit Device
- Object Manager
- High Frequency Poller
- Device Summary
- Device Mover
- Device Groups
- Object Groups
- Object Summary
- Object Rules
- VMware Browser
- Calculation Plugin
- Cisco ACI Plugin
- Database Manager
- Deferred Data Plugin
- DNS Plugin
- HTTP Plugin
- ICMP Plugin
- IP SLA Plugin
- JMX Plugin
- NAM
- NBAR Plugin
- Portshaker Plugin
- Process Plugin
- Proxy Ping Plugin
- SNMP Plugin
- VMware Plugin
- Web Status Plugin
- WMI Plugin
- xStats Plugin
- Indicator Type Maps
- Device Types
- Object Types
- Object Subtype Manager
- Calculation Editor
- xStats Source Manager
- User Role Manager
- User Manager
- Session Manager
- Authentication Settings
- Preferences
- Cluster Manager
- Maintenance Windows
- Processes and Logs
- Metadata Schema
- Baseline Manager
- FlowFalcon View Editor
- Map Flow Objects
- FlowFalcon Views
- Flow Rules
- Flow Interface Manager
- MPLS Flow Mapping
- Network Segment Manager
- Flow Protocols and Services
- xStats Log Viewer
- SNMP Walk
- SNMP OID Browser
- MIB Manager
- Work Hours
- Administrative Messages
- Enable Flow Technologies
- Enable JMX
- Enable NBAR
- Enable SNMP
- Enable Web Status
- Enable WMI
- IP SLA
- SNMP
- SevOne Data Bus
- Quality of Service
- Perl Regular Expressions
- Trap Revisions
- Integrate SevOne NMS With Other Applications
- Email Tips and Tricks
- SevOne NMS PHP Statistics
- SevOne NMS Usage Statistics
- Glossary and Concepts
- Map Flow Devices
- Trap v3 Receiver
- Guides
- SevOne Implementation Guide
- SevOne Best Practices Guide - Cluster, Peer, and HSA
- SevOne Installation Guide - Virtual Appliance
- SevOne NMS Installation Guide
- SevOne SAML Single Sign-On Setup Guide
- Access Control Quick Start Guide - SevOne NMS 5.7
- Data Miner Quick Start Guide - SevOne NMS 5.7
- Flow Quick Start Guide - SevOne NMS 5.7
- Group Aggregated Indicators Quick Start Guide - SevOne NMS 5.7
- IP SLA Quick Start Guide - SevOne NMS 5.7
- JMX Quick Start Guide - SevOne NMS 5.7
- LDAP Quick Start Guide - SevOne NMS 5.7
- Metadata Quick Start Guide - SevOne NMS 5.7
- RESTful API Quick Start Guide - SevOne NMS 5.7
- Self-monitoring Quick Start Guide - SevOne NMS 5.7
- SevOne NMS Admin Notifications Quick Start Guide - SevOne NMS 5.7
- SNMP Quick Start Guide - SevOne NMS 5.7
- Synthetic Indicator Types Quick Start Guide - SevOne NMS 5.7
- Topology Quick Start Guide - SevOne NMS 5.7
- VMware Quick Start Guide - SevOne NMS 5.7
- Web Status Quick Start Guide - SevOne NMS 5.7
- WMI Quick Start Guide - SevOne NMS 5.7
- xStats Quick Start Guide - SevOne NMS 5.7
Access Control Quick Start Guide - SevOne NMS 5.7
SevOne Documentation
All SevOne NMS user documentation is available online from the SevOne Support customer portal.
Copyright © 2005-2020 SevOne Inc. All rights reserved worldwide.
All right, title, and interest in and to the software and documentation are and shall remain the exclusive property of SevOne and its respective licensors. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of SevOne.
In no event shall SevOne, its suppliers, nor its licensors be liable for any damages, whether arising in tort, contract, or any other legal theory even if SevOne has been advised of the possibility of such damages, and SevOne disclaims all warranties, conditions, or other terms, express or implied, statutory or otherwise, on software and documentation furnished hereunder including without limitation the warranties of design, merchantability, or fitness for a particular purpose, and noninfringement.
All SevOne marks identified or used on the SevOne website, as updated by SevOne from time to time, may be, or are, registered with the U.S. Patent and Trademark Office and may be registered or pending registration in other countries. All other trademarks or registered trademarks contained and/or mentioned herein are used for identification purposes only and may be trademarks or registered trademarks of their respective companies.
User Roles in SevOne NMS
User roles offer an efficient and consistent approach to managing user permissions. Rather than assign permissions to users, you can assign users to the appropriate user roles, which grant the users the permissions that they need. In addition to granting users permissions, user roles also limit users' access as needed.
User roles are hierarchical. Each child user role has one parent user role. The parent role will have all the same permissions as its child and possibly more. But the child role will never have more permissions than its parent. The child role receives all of its permissions from its parent. Depending on your specific needs, you may want to remove one or more permissions from the child. However, you can't add permissions to the child role. This ensures that users assigned to a specific role aren't granted any permissions beyond the ones intended for that role.
Consider a scenario where permissions are user-based rather than role-based. Let's say our networking team requires a set of twenty specific permissions. That means that every time a new person is added to the team, we have to grant those twenty permissions to the user. Not only is that time-consuming, but it also leaves room for error. If we forget a permission, the team member may not be able to do their job. If we accidentally add a permission that's not part of the usual set, we might be granting our new team member access that they shouldn't have–thus creating a security risk. In SevOne NMS versions 5.3.x and higher, all permissions are granted to users through user roles, eliminating the need to configure permissions for individual users.
About User Roles and Permissions
User roles give you the ability to define the following:
-
Page permissions and user permissions
-
Devices and device groups access
-
Users and user roles access
Page permissions are associated to one or more pages in SevOne NMS. They give users access to view their associated pages. For example, if you enable the Threshold Configuration page permission for a user role, users assigned to that role will be able to view the Policy Browser and Threshold Browser pages in SevOne NMS. Most page permissions have associated user permissions. This means that when you enable a page permission, its associated user permissions are automatically enabled as well.
User permissions give users abilities that apply to pages in SevOne NMS. Going back to page permissions, if we enable the page permission User Management for a user role, users assigned to that role will have access to the User Manager page. The User Management page permission has one corresponding user permission: Can create users. So, when you enable User Management, you automatically grant the user permission Can create users to any users assigned to the current user role. If you need to grant additional user permissions to the role, you can do so manually.
Devices and device groups access is used to enable or disable the following user actions:
-
View device groups/device types
-
Edit device groups/device types
-
View devices
-
Edit devices
Similarly, users and user roles access grants or blocks the following abilities:
-
View user roles
-
Edit user roles
-
View users
-
Edit users
Prerequisites
User roles are available in SevOne NMS 5.3.x and above.
Configuration Steps
In this section, we'll look at the following topics:
-
User roles
-
Page permissions and user permissions
-
Device and device group/device type access
-
Assigning users to user roles
Manage User Roles
User roles are hierarchical and act as containers for permissions. By assigning users to user roles, you can determine what users can see and do in SevOne NMS. Perform the following steps to create or edit a user role.
-
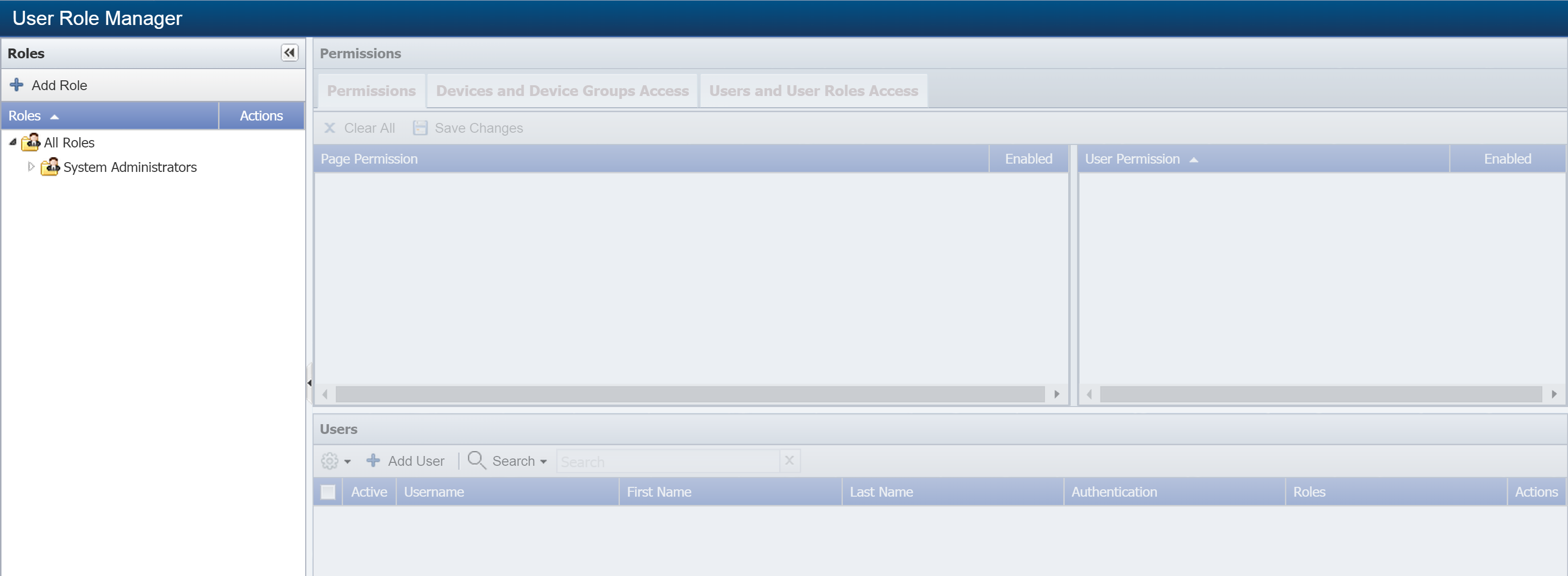
From the navigation bar, click Administration and select Access Configuration, then User Role Manager.
-
On the left side of the page, under Roles, click Add Role to display the Add Role pop-up.
To edit an existing user role, select the role from the role hierarchy and click
 to display the Edit Role pop-up. From here, you can edit the user role name and description.
to display the Edit Role pop-up. From here, you can edit the user role name and description. 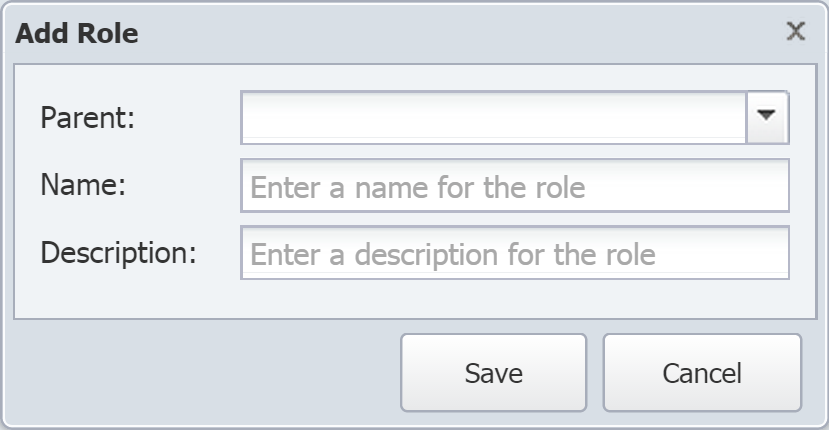
-
Click the Parent drop-down to view the role hierarchy. Then select the parent role to add your new role to. Once you click Save, you won't be able to edit the Parent field.
-
In the Name field, enter the name of the new role.
-
In the Description field, enter a description of the role.
-
Click Save.
Manage Permissions
The Permissions section contains three tabs, which allow you to define the following for each user role:
-
Page permissions
-
User permissions
-
Devices and device groups/device types access
-
Users and user roles access
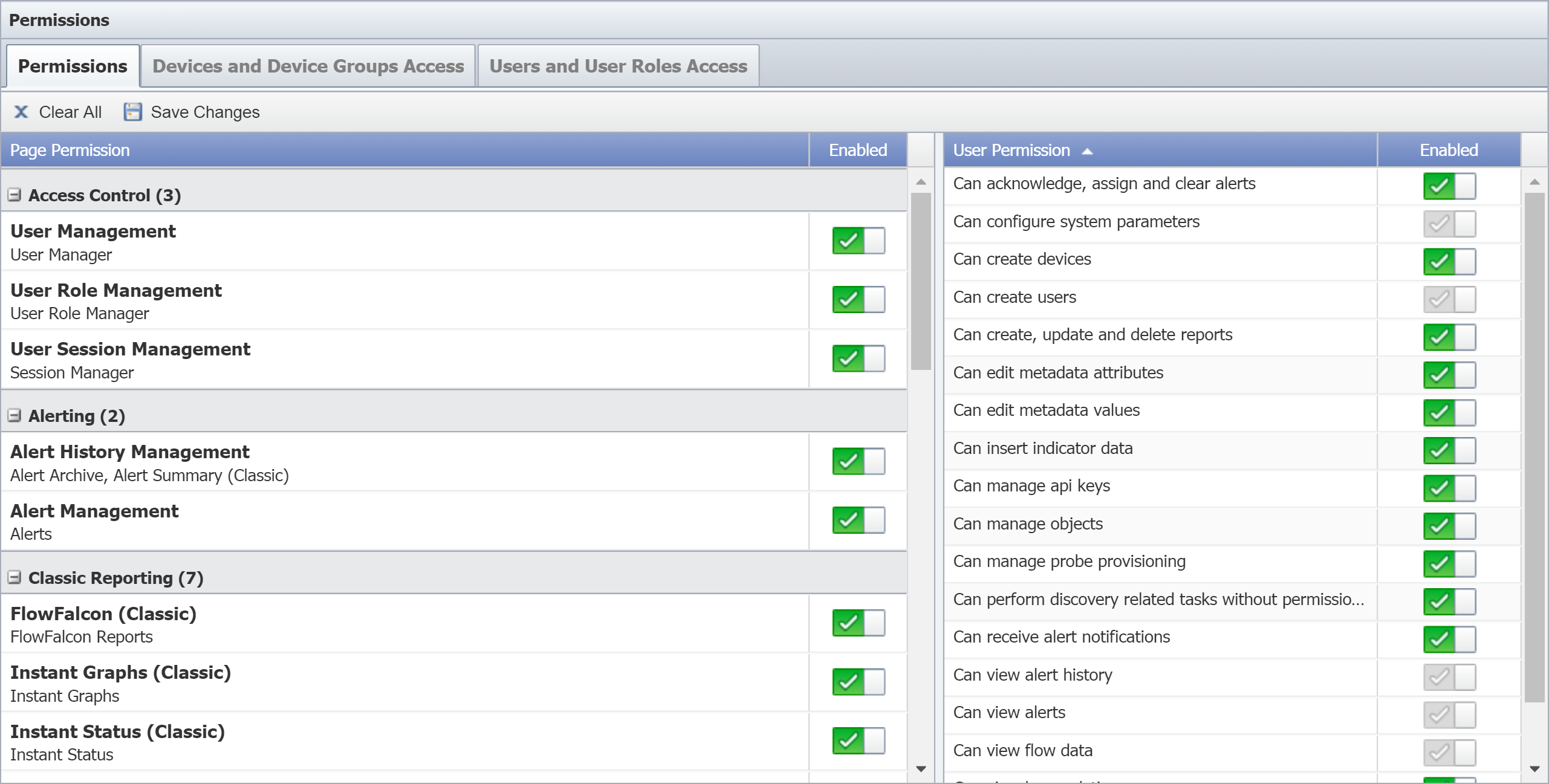
Page Permissions
The Page Permission section, which is on the left side of the Permissions tab, lets you grant users access to view applicable pages as long as those users are assigned to the relevant user role.
Enabling a page permission grants users access to the pages indicated by page permission. Under System Administration, for example, you'll find several page permissions. If you enable the page permission called Cluster Configuration, you're granting access to the following pages in SevOne NMS: Authentication Settings, Baseline Manager, Cluster Manager, Device Mover, and Work Hours.
Page permissions have corresponding minimum user permissions, which become enabled when you enable the page permission. For Cluster Configuration, the corresponding user permission is Can configure system parameters. This means that if you enable the Cluster Configuration page permission for a user role, then the user permission Can configure system parameters is also enabled for any users assigned to the applicable user role. You can enable additional user permissions beyond what's included with a page permission. However, you can't disable any of the corresponding user permissions for a page permission if the page permission is enabled.
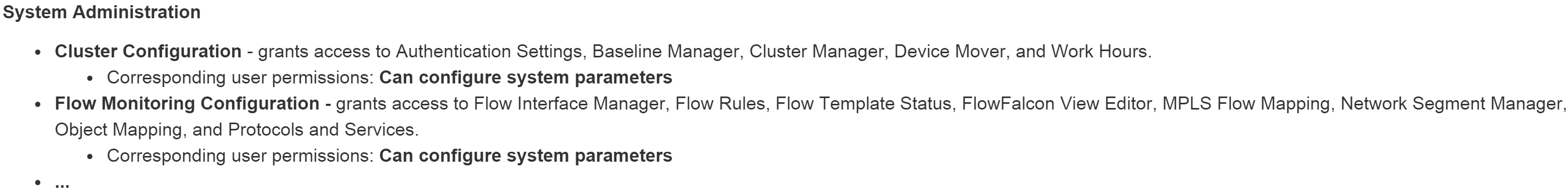
The page permissions are listed below. The following screenshot shows two of the page permissions in the System Administration category. Each page permission includes the pages that it grants access to and its corresponding user permissions.
When you disable all page permissions, an enabled user still has permission to access to the following pages:
-
About
-
Dashboard
-
My Preferences
Perform the following steps to enable page permissions for a user role.
-
On the left side of the page, in the Roles hierarchy, select the user role that you would like to enable page permissions for.
-
Select the Permissions tab if it's not already selected.
-
Under Page Permission on the left side of the tab, enable each applicable page permission to grant users belonging to the user role access to the pages listed.
-
Once you've finished enabling permissions, click Save Changes at the top of the tab.
If you disable a page permission, the corresponding user permissions for it will remain enabled. If you want to disable the corresponding user permissions, too, you'll need to do so manually.
Access Control
-
User Management - grants access to the User Manager.
-
Corresponding user permission: Can create users
-
-
User Role Management - grants access to the User Role Manager.
-
Corresponding user permission: Can create users
-
-
User Session Management - grants access to the Session Manager.
-
Corresponding user permissions: None
-
Alerting
-
Alert History Management - grants access to Alert Archive and Alert Summary.
-
Corresponding user permissions: Can view alert history, Can view alerts, Can view reports
-
-
Alert Management - grants access to Alerts.
-
Corresponding user permissions: Can view alerts, Can view reports
-
Classic Reporting
-
FlowFalcon (Classic) - grants access to FlowFalcon Reports.
-
Corresponding user permissions: Can view flow data, Can view reports
-
-
Instant Graphs (Classic) - grants access to Instant Graphs.
-
Corresponding user permission: Can view reports
-
-
Instant Status (Classic) - grants access to Instant Status.
-
Corresponding user permissions: Can view alerts, Can view reports
-
-
NBAR Reporting (Classic) - grants access to NBAR Reports.
-
Corresponding user permission: Can view reports
-
-
Status Maps (Classic) - grants access to Status Map Manager.
-
Corresponding user permissions: Can view alerts, Can view reports
-
-
TopN (Classic) - grants access to TopN Reports.
-
Corresponding user permission: Can view reports
-
Device Management
-
Device Manager - grants access to Device Manager and SNMP Walk.
-
Corresponding user permissions: None. You can enable the Can create devices user permission to grant users the ability to add devices. The Devices and Device Groups Access tab lets you limit which devices users can see.
-
-
Discovery Management - grants access to Discovery Manager.
-
Corresponding user permissions: None. You can enable the Can create devices user permission to grant users the ability to manage devices. The Devices and Device Groups Access tab lets you limit which devices users can see.
-
-
Probe Provisioning - grants access to Probe Manager and the Proxy Ping configuration on the Edit Device page.
-
Corresponding user permissions: None.
-
-
VMware Browser - grants access to VMware Browser.
-
Corresponding user permissions: None. You can specify limits from the Devices and Device Groups Access tab.
-
Metadata
-
Metadata Attributes - grants access to Metadata Schema.
For this page permission, no user permissions are automatically enabled. You'll need to manually enable the user permission Can edit metadata attributes in order to grant users permission to edit the metadata attributes.
-
Metadata Values - grants access to view metadata values from the following pages: Device Types, Device Groups, Device Manager, Edit Device, Object Groups, and Object Manager .
For this page permission, no user permissions are automatically enabled. You'll need to manually enable the user permission Can edit metadata values in order to grant users permission to edit the metadata values.
Other
-
Device Group Manager - grants access to Device Groups.
-
Corresponding user permissions: None. You can specify limits from the Devices and Device Groups Access tab.
-
-
Object Manager - grants access to Object Manager.
-
Corresponding user permissions: None. You can specify limits from the Devices and Device Groups Access tab.
-
-
Report Manager - grants access to Report Attachment Wizard and Report Manager.
-
Corresponding user permissions: Can view reports
-
System Administration
-
Cluster Configuration - grants access to Authentication Settings, Baseline Manager, Cluster Manager, Device Mover, and Work Hours.
-
Corresponding user permissions: Can configure system parameters
-
-
Flow Monitoring Configuration - grants access to Flow Interface Manager, Flow Rules, FlowFalcon View Editor, MPLS Flow Mapping, Network Segment Manager, Object Mapping, and Protocols and Services.
-
Corresponding user permissions: Can configure system parameters
-
-
Maintenance Window Configuration - grants access to Maintenance Window Manager.
-
Corresponding user permissions: None
-
-
Object Group Manager - grants access to Object Groups.
-
Corresponding user permissions: Can configure system parameters
-
-
Polling Configuration - grants access to Calculation Editor, Device Types, MIB Manager, Object Rules, Object Subtype Manager, Object Types, and SNMP OID Browser.
-
Corresponding user permissions: Can configure system parameters
-
-
Threshold Configuration - grants access to Policy Browser and Threshold Browser.
-
Corresponding user permissions: None
-
-
Trap Configuration - grants access to Logged Traps, Trap Destinations, Trap Destination Associations, Trap Event Editor, and Unknown Traps.
-
Corresponding user permissions: Can configure system parameters
-
-
xStats Configuration - grants access to xStats Log Viewer and xStats Source Manager.
-
Corresponding user permissions: Can configure system parameters
-
User Permissions
The User Permission section appears on the right side of the Permissions tab. Here you can grant additional permissions to users for a particular user role–beyond the user permissions that are granted when page permissions are enabled.
User permissions are governed by the Page Permission settings, and the user is further limited by their Devices and Device Groups Access and their Users and User Roles Access settings.
Perform the following steps to enable user permissions for a user role.
-
On the left side of the page, in the Roles hierarchy, select the user role that you would like to enable user permissions for.
-
Select the Permissions tab if it's not already selected.
-
Under User Permission on the right side of the tab, enable each user permission that you would like to grant to users belonging to the user role.
-
Once you've finished enabling permissions, click Save Changes at the top of the tab.
The following is a list of user permissions and a description of what each does when it's enabled.
-
Can acknowledge, assign and clear alerts - grants users permission to acknowledge, assign, and clear alerts. You'll also need to enable appropriate Devices and Device Groups permissions and the page permission for Alert Management.
-
Can configure system parameters - grants users permission to perform system administration tasks. You'll also need to enable appropriate Devices and Device Groups permissions and appropriate page permissions.
-
Can create devices - grants users permission to create, edit and delete device data. You'll also need to enable appropriate Devices and Device Groups permissions and the page permission for Device Manager.
-
Can create users - grants users permission to create, edit, and delete user data. You'll also need to enable appropriate Users and User Roles permissions and the page permission for User Management and/or User Role Management.
-
Can create, update and delete reports - grants users permission to create and save report data. You'll also need to enable appropriate Devices and Device Groups permissions and the page permission for Instant Graphs, Device Manager, NBAR Reports, Report Manager, and/or Status Map Manager. Users assigned to the role can create disposable reports from these pages and can detach individual reports to a comprehensive report that they can save to the Report Manager.
-
Can edit metadata attributes - grants users permission to edit the metadata attributes on the Metadata Schema page.
-
Can edit metadata values - grants users permission to edit the values for the metadata attributes that are specific to a device type, device group, device, object group, or object.
-
Can insert indicator data - grants users permission to insert indicator data. This is used with the API.
-
Can manage api keys - grants users permission to manage API keys. This is used with the API .
-
Can manage objects - grants users permission to manage objects.
-
Can manage probe provisioning - grants users permission to provision probes via the Probe Manager. You'll also need to enable appropriate Devices and Device Groups permissions and the page permission for Probe Provisioning.
-
Can perform discovery related tasks without permission checks - grants user permission to perform discovery tasks without the need for permission checks. This is used with the API.
-
Can receive alert notifications - grants users permission to receive e-mail notifications from applicable traps, policies, and thresholds. This permission doesn't grant access to any workflows in SevOne NMS.
-
Can view alert history - grants users permission to view archived alerts. You'll also need to enable appropriate Devices and Device Groups permissions and the page permission for Alert History Management.
-
Can view alerts - grants users permission to view alerts. You'll also need to enable appropriate Devices and Device Groups permissions and the page permission for Alert Management.
-
Can view flow data - grants users permission to view flow data in FlowFalcon reports. You'll also need to enable appropriate Devices and Device Groups permissions and the page permission for FlowFalcon Reports.
-
Can view log analytics - grants users permission to view log analytic data collected by a Performance Log Appliance (PLA).
-
Can view reports - grants users permission to view report data. You'll also need to enable appropriate Devices and Device Groups permissions and the page permission for Instant Graphs, Device Manager, NBAR Reports, Report Manager, and/or Status Map Manager. Users assigned to the role can create disposable reports from these pages and can detach individual reports to a comprehensive report but they cannot save reports to the Report Manager.
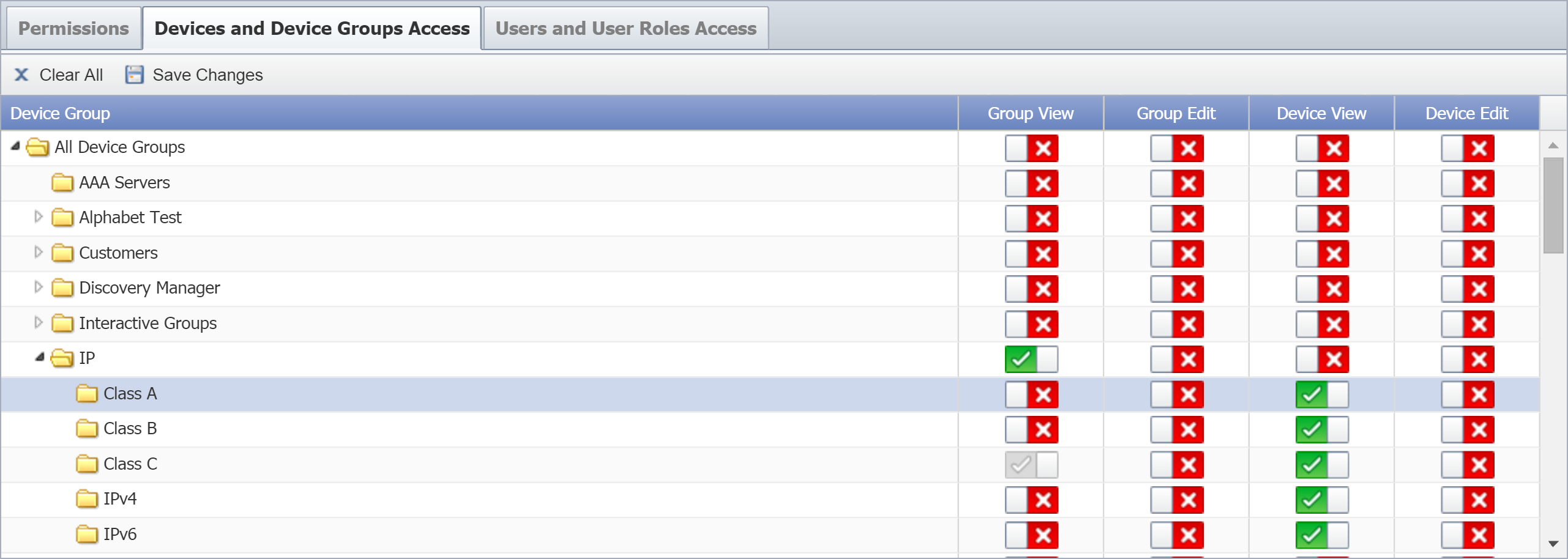
Devices and Device Groups Access
Perform the following actions to enable Devices and Device Groups permissions.
When you enable the Devices and Device Groups permissions for higher level user roles, the same Devices and Device Groups permissions become available for the subordinate user roles. Conversely, when you disable the Devices and Device Groups permissions, the corresponding Devices and Device Groups permissions are no longer available for the subordinate user roles.
-
Select the Devices and Device Groups Access tab.
-
Under Device Group, click
 next to All Device Groups or All Device Types to expand the section.
next to All Device Groups or All Device Types to expand the section. -
Select the device group or device type that you would like to apply access settings to.
-
On the right, enable (or disable) one or more of the following permissions:
-
Group View - grants users permission to view the name of the device group/device type. Users won't be able to see the devices that are members of the device group/device type or any corresponding device data until you enable the Device View permission.
-
Group Edit - grants users permission to edit the name of the device group/device type. Enable Device View to grant permission to edit the list of devices that are members of the device group/device type.
Enabling Group Edit automatically enables Group View.
-
Device View - grants users permission to see the devices that are members of the device group/device type and applicable corresponding device data. If you disable the Group View permission, users can see the devices that are members of the device group/device type but can't see the name of the device group/device type.
-
Device Edit - grants users permission to edit the configuration of the devices that are members of the device group/device type.
Enabling Device Edit automatically enables Device View.
-
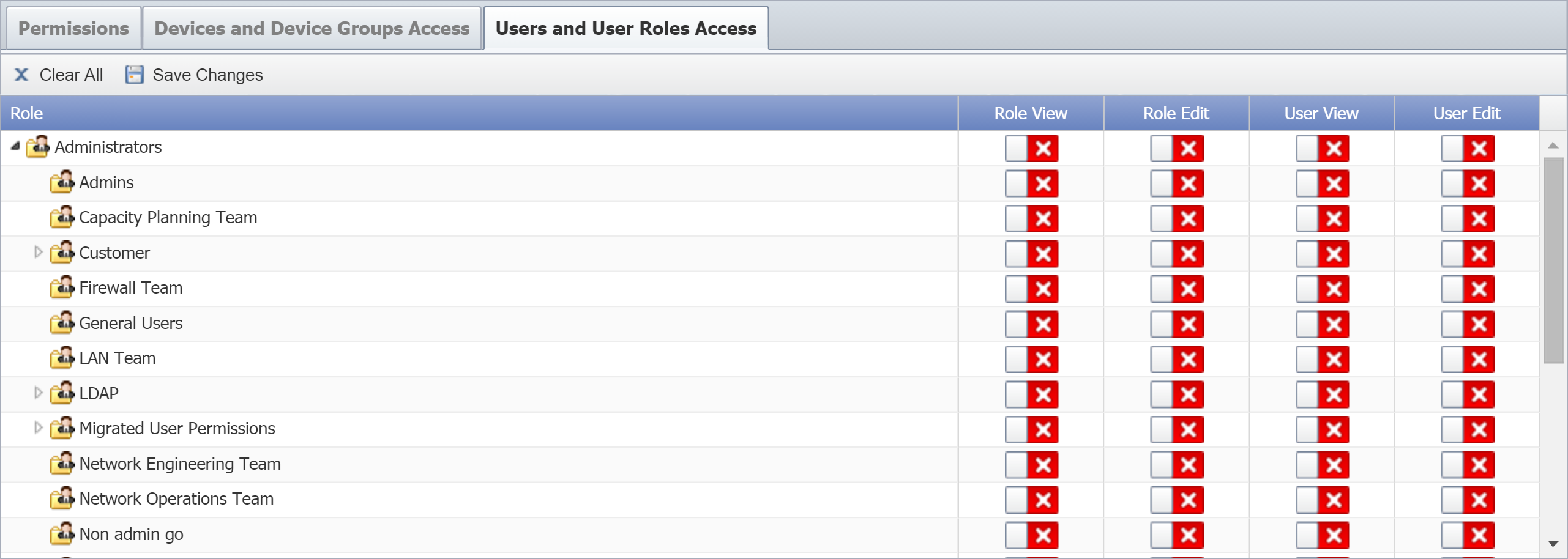
Users and User Roles Access
Perform the following actions to enable Users and User Roles permissions.
When you enable the Users and User Roles permissions for higher level user roles, the same Users and User Roles permissions become available for the subordinate user roles. Conversely, when you disable the Users and User Roles permissions, the corresponding Users and User Roles permissions are no longer available for the subordinate user roles.
-
Select the Users and User Roles Access tab.
-
Under Role, click
 next to Administrators to expand the section.
next to Administrators to expand the section. -
Select the role that you would like to apply access settings to.
-
On the right, enable (or disable) one or more of the following permissions:
-
Role View - grants users permission to view the name of the user role. Users assigned to the role can't see users assigned to the user role until you enable applicable User View permissions .
-
Role Edit - grants users permission to edit the user role name. Enable applicable User View permissions to grant users assigned to the role permission to manage the user assignments for the role.
Enabling Role Edit automatically enables Role View.
-
User View - grants users permission to view the users in the role.
-
User Edit - grants users permission to edit the user information, credentials, and role assignments for the users who are assigned to the user role.
Enabling User Edit automatically enables User View.
-
Assigning Users to User Roles
There are two pages where you can assign users to user roles:
-
User Role Manager
-
Create new users and assign them to user roles.
-
Assign existing users to user roles. When doing this from the User Role Manager, you'll need to locate a role that the user is already assigned to.
-
-
User Manager
-
Create new users and assign them to user roles.
-
Assign existing users to user roles. When doing this from the User Manager, you can choose from a single list of users, without having to first find a role that the user is assigned to.
-
Assign Users to User Roles - User Role Manager
The Users section on the lower half of the page allows you to add new users and assign them to user roles. You can also edit information for users already assigned to user roles. In addition to changing the roles that they're assigned to, you can change basic user information, such as name, e-mail address, etc.
You can assign an existing user in SevOne NMS to additional user roles as long as that user is already assigned to at least one user role. Existing users who aren't already assigned to a user role won't show up in the User Role Manager. To assign existing SevOne NMS users to user roles when they're not already assigned to a user role, use the User Manager.
Assign Users to User Roles
Perform the following steps to assign a new user to a user role.
-
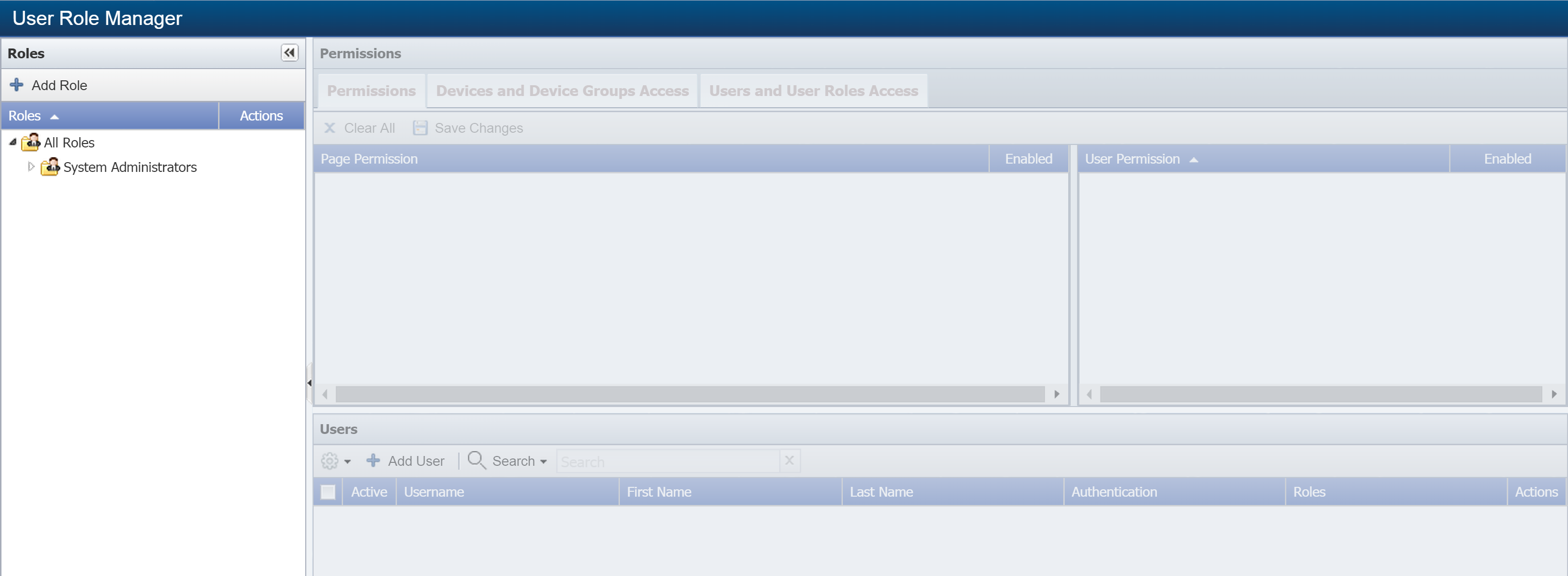
If you're not already on the User Role Manager page, go there now (Administration -> Access Configuration -> User Role Manager).
-
On the left side of the page, in the Roles hierarchy, select a role that you would like to assign a user to.
The role you select here will automatically be checked as a user role to assign the user to. You can uncheck it if you decide to assign the user to a different user role instead.
-
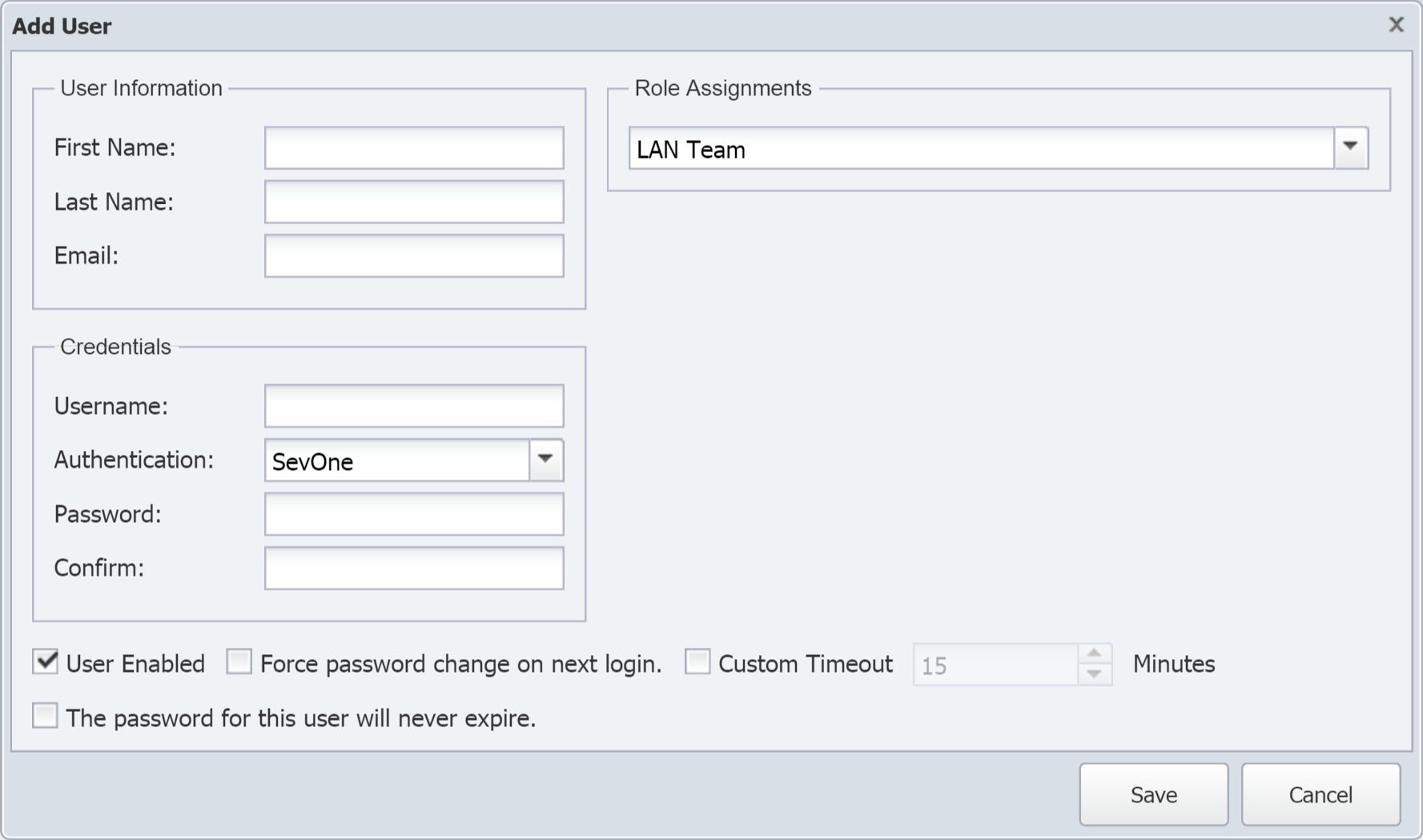
On the lower half of the page, under Users, click Add User to display the Add User pop-up.
-
Under User Information, perform the following actions.
-
In the First Name field, enter the user's first name. This name will appear wherever a user name appears.
-
In the Last Name field, enter the user's last name. This name will also appear wherever a user name appears.
-
In the Email field, enter the user's email address .
-
-
Under Credentials, perform the following actions.
-
In the Username field, enter a user name for the user.
-
Click the Authentication drop-down and select the authentication method that will be used at logon. Select SevOne unless your company uses LDAP, RADIUS, or TACACS to authenticate users.
-
In the Password field, enter a password for the user.
The Password field and the Confirm field are unavailable for users authenticating with LDAP, RADIUS, or TACACS. Password management for these protocols is handled through the corresponding authentication servers.
-
In the Confirm field, re-enter the password.
-
-
Under Role Assignments, click the drop-down and select the user roles that you would like to assign the user to. You can assign users to multiple roles, and role permissions are cumulative. Clear the check boxes for any user roles that you don't want the user assigned to.
-
At the bottom of the pop-up, select the User Enabled check box to enable the user to log on to and use SevOne NMS. To block access to the user without having to delete the account, leave this check box clear.
-
Select the Force password change on next login check box to require the user to change the password when they log on for the first time.
-
Select the Custom Timeout check box to enable the user to stay logged on during periods of inactivity for a specified amount of time. In the Custom Timeout field, specify the number of minutes that the user can stay logged on.
This setting overrides the Inactivity Timeout setting specified on the Cluster Manager > Cluster Settings tab > Security subtab. To have the user log off after the amount of time specified in the Cluster Manager, leave the check box here clear. The user needs to log off and log back on in order for this setting to take effect.
-
Select the The password for this user will never expire check box to override the Maximum Password Age setting specified on the Cluster Manager > Cluster Settings tab > Security subtab.
-
Click Save.
Your new user will also appear on the User Manager page, which we'll look at shortly.
Manage Existing Users
In order to manage an existing user from the User Role Manager page, you'll first need to select the role they belong to (on the left side of the page, in the Roles hierarchy). Then locate the user in the Users section on the lower half of the page.
To enable, disable, or delete an existing user, select the check box next to the user. Then click ![]() and select Enable, Disable, or Delete.
and select Enable, Disable, or Delete.
To assign the user to additional roles, select the check box for that user. Then click ![]() to display the Edit User pop-up. Click the Role Assignments drop-down and select the user role(s) that you would like to assign the user to.
to display the Edit User pop-up. Click the Role Assignments drop-down and select the user role(s) that you would like to assign the user to.
Assign Users to User Roles - User Manager
If you need to assign an existing user to a user role, and that user isn't already assigned to any user roles, this is where you'll do it. The User Manager page contains all SevOne NMS users. You can also create new users here, just like you did above.
Perform the following steps to assign an existing SevOne NMS user to a user role.
-
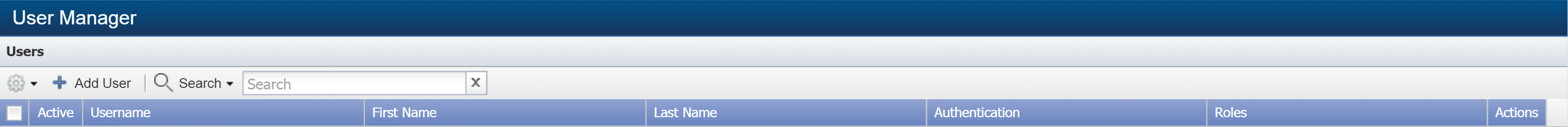
From the navigation bar, click Administration and select Access Configuration, then User Manager.
-
Under Users, select the check box for the user that you want to assign to a role.
-
Click
 to display the Edit User pop-up.
to display the Edit User pop-up. 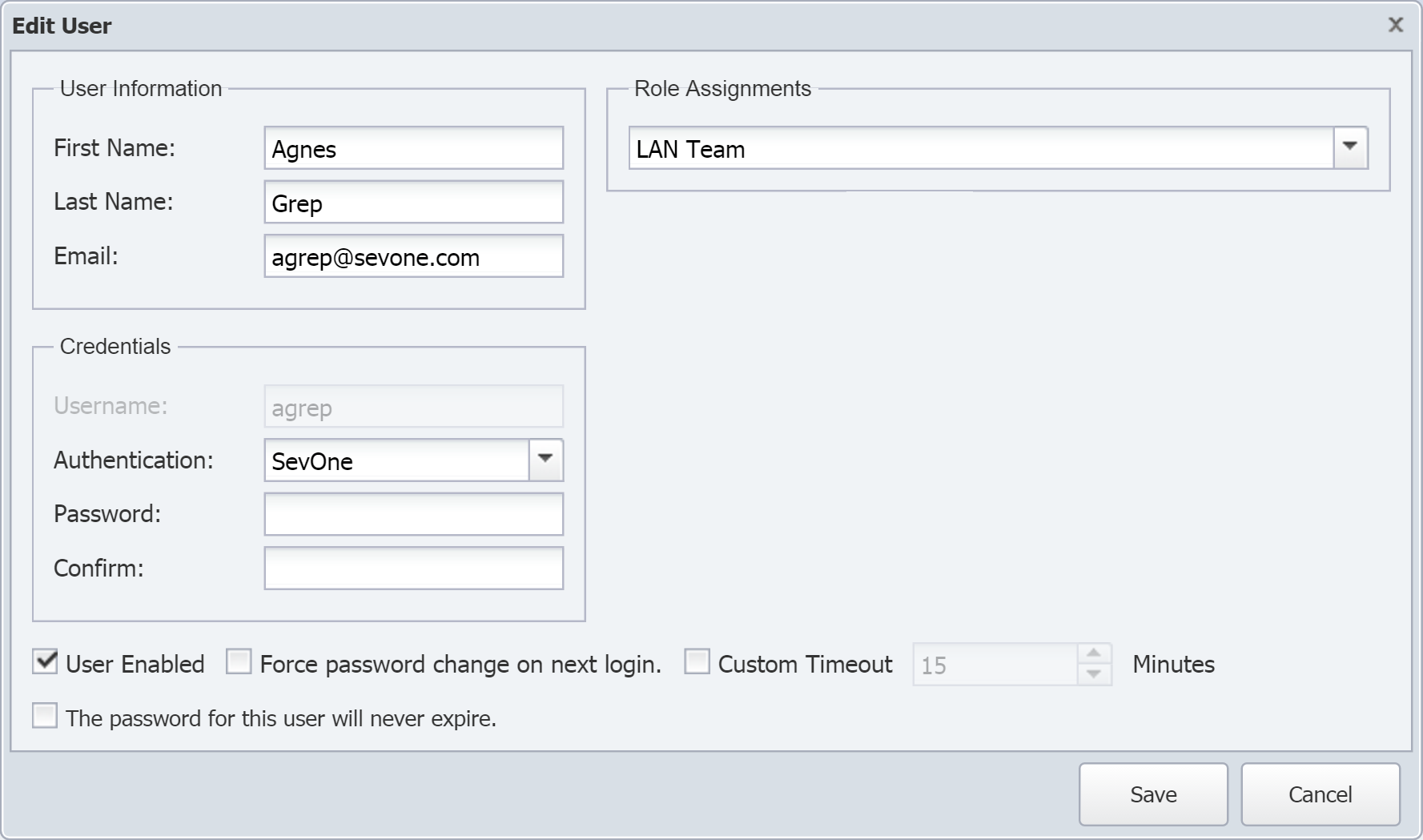
-
On the right side of the pop-up, click the Role Assignments drop-down and select the check box for each role that you want to assign the user to.
-
Click Save. If you go the the User Role Manager page, the user should now appear listed in the Users section for the user roles that they are assigned to.
Troubleshooting
I disabled a page permission but users assigned to the user role still have the user permissions associated with it.
A bit earlier, we mentioned that you'll need to manually disable corresponding user permissions for a page permission when you disable that page permission. Otherwise, the corresponding user permissions remain enabled even after you've disabled the page permission.
Terms
|
Lightweight Directory Access Protocol (LDAP) |
An application protocol to query and modify directory services that run over TCP/IP to enable maintenance of centralized user directories that distributed applications authenticate to. |
|
Remote Authentication Dial-In User Service (RADIUS) |
A network protocol that provides centralized access, authorization, and accounting management for people or computers to connect and use a network service. |
|
Terminal Access Controller Access Control System (TACACS) |
A remote authentication protocol that communicates with an authentication server commonly used in UNIX networks. |