
Table of Contents (Start)
- Topics
- Introducing SevOne
- Login
- Startup Wizard
- Dashboard
- Global Search - Advanced Search
- Report Manager
- Report Attachment Wizard
- Report Properties
- Report Interactions
- Instant Graphs
- TopN Reports
- Alerts
- Alert Archives
- Alert Summary
- Instant Status
- Status Map Manager
- Edit Maps
- View Maps
- FlowFalcon Reports
- NBAR Reports
- Logged Traps
- Unknown Traps
- Trap Event Editor
- Trap Destinations
- Trap Destination Associations
- Policy Browser
- Create and Edit Policies
- Threshold Browser
- Create and Edit Thresholds
- Probe Manager
- Discovery Manager
- Device Manager
- New Device
- Edit Device
- Object Manager
- High Frequency Poller
- Device Summary
- Device Mover
- Device Groups
- Object Groups
- Object Summary
- Object Rules
- VMware Browser
- Calculation Plugin
- Cisco ACI Plugin
- Database Manager
- Deferred Data Plugin
- DNS Plugin
- HTTP Plugin
- ICMP Plugin
- IP SLA Plugin
- JMX Plugin
- NAM
- NBAR Plugin
- Portshaker Plugin
- Process Plugin
- Proxy Ping Plugin
- SNMP Plugin
- VMware Plugin
- Web Status Plugin
- WMI Plugin
- xStats Plugin
- Indicator Type Maps
- Device Types
- Object Types
- Object Subtype Manager
- Calculation Editor
- xStats Source Manager
- User Role Manager
- User Manager
- Session Manager
- Authentication Settings
- Preferences
- Cluster Manager
- Maintenance Windows
- Processes and Logs
- Metadata Schema
- Baseline Manager
- FlowFalcon View Editor
- Map Flow Objects
- FlowFalcon Views
- Flow Rules
- Flow Interface Manager
- MPLS Flow Mapping
- Network Segment Manager
- Flow Protocols and Services
- xStats Log Viewer
- SNMP Walk
- SNMP OID Browser
- MIB Manager
- Work Hours
- Administrative Messages
- Enable Flow Technologies
- Enable JMX
- Enable NBAR
- Enable SNMP
- Enable Web Status
- Enable WMI
- IP SLA
- SNMP
- SevOne Data Bus
- Quality of Service
- Perl Regular Expressions
- Trap Revisions
- Integrate SevOne NMS With Other Applications
- Email Tips and Tricks
- SevOne NMS PHP Statistics
- SevOne NMS Usage Statistics
- Glossary and Concepts
- Map Flow Devices
- Trap v3 Receiver
- Guides
- SevOne Implementation Guide
- SevOne Best Practices Guide - Cluster, Peer, and HSA
- SevOne Installation Guide - Virtual Appliance
- SevOne NMS Installation Guide
- SevOne SAML Single Sign-On Setup Guide
- Access Control Quick Start Guide - SevOne NMS 5.7
- Data Miner Quick Start Guide - SevOne NMS 5.7
- Flow Quick Start Guide - SevOne NMS 5.7
- Group Aggregated Indicators Quick Start Guide - SevOne NMS 5.7
- IP SLA Quick Start Guide - SevOne NMS 5.7
- JMX Quick Start Guide - SevOne NMS 5.7
- LDAP Quick Start Guide - SevOne NMS 5.7
- Metadata Quick Start Guide - SevOne NMS 5.7
- RESTful API Quick Start Guide - SevOne NMS 5.7
- Self-monitoring Quick Start Guide - SevOne NMS 5.7
- SevOne NMS Admin Notifications Quick Start Guide - SevOne NMS 5.7
- SNMP Quick Start Guide - SevOne NMS 5.7
- Synthetic Indicator Types Quick Start Guide - SevOne NMS 5.7
- Topology Quick Start Guide - SevOne NMS 5.7
- VMware Quick Start Guide - SevOne NMS 5.7
- Web Status Quick Start Guide - SevOne NMS 5.7
- WMI Quick Start Guide - SevOne NMS 5.7
- xStats Quick Start Guide - SevOne NMS 5.7
WMI Quick Start Guide - SevOne NMS 5.7
SevOne Documentation
All SevOne user documentation is available online from the SevOne Support customer portal.
Copyright © 2005-2020 SevOne Inc. All rights reserved worldwide.
All right, title, and interest in and to the software and documentation are and shall remain the exclusive property of SevOne and its respective licensors. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of SevOne.
In no event shall SevOne, its suppliers, nor its licensors be liable for any damages, whether arising in tort, contract, or any other legal theory even if SevOne has been advised of the possibility of such damages, and SevOne disclaims all warranties, conditions, or other terms, express or implied, statutory or otherwise, on software and documentation furnished hereunder including without limitation the warranties of design, merchantability, or fitness for a particular purpose, and noninfringement.
All SevOne marks identified or used on the SevOne website, as updated by SevOne from time to time, may be, or are, registered with the U.S. Patent and Trademark Office and may be registered or pending registration in other countries. All other trademarks or registered trademarks contained and/or mentioned herein are used for identification purposes only and may be trademarks or registered trademarks of their respective companies.
About WMI
Windows Management Instrumentation, or WMI, is based on the Common Information Model (CIM). Back in the 1990s, the Distributed Management Task Force (DMTF) set to work on an industry-wide standard for managing objects across networks. The catch? It would have to accommodate all kinds of devices, fr o m networking equipment to servers and individual computers. They came up w ith the Common Information Model (CIM).
The CIM is a hierarchical, object-oriented schema made up of three main class levels:
-
The Core level is technology-neutral and includes general classes that apply to all areas of management, such as Component, Collection, and Statistical Information, for example.
-
The Common level is vendor-neutral and extends from the Core level. Common classes include things like networks, systems, devices, databases, and users.
-
The Extension level is vendor-specific. Extension classes extend from common classes–although they can also extend from core classes. Win32_BaseService and Win32_ComputerSystem are examples of Windows extension classes.
WMI incorporates components of the CIM, such as systems, devices, and applications, for example. It also has the extensibility of the CIM. The newest generation of WMI is actually known as Windows Management Infrastructure (rather than Instrumentation), or MI for short, starting with Windows 8 and Server 2012. The term WMI is still in wide use, though.
How WMI Works
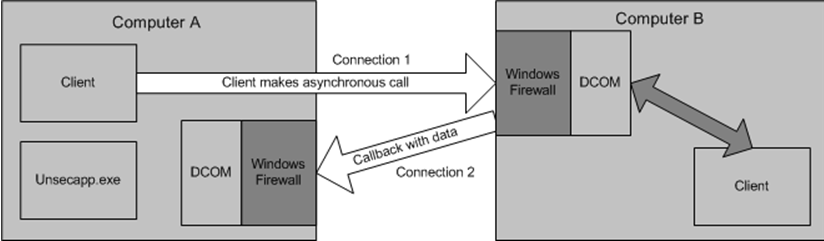
In the diagram below, we have two devices talking to each other: Computer A and Computer B. Computer A is simply a device that sends WMI queries to another device. In our case, Computer A is the WMI proxy server that we'll be setting up in the Configuration Steps section. Computer B is the device that receives the WMI queries and sends back answers. Let's say that Computer B is a Windows 7 machine. Computer A sends a WMI query to Computer B. For example, it might ask who's logged in to Computer B right now. Computer B receives the request, then sends an answer back to Computer A.
In the diagram, Connection 1 represents the part where Computer A says to Computer B "Hey, who's logged in right now?" To do this, WMI has to establish a DCOM connection from Computer A to Computer B. To that end, we'll be configuring the Windows Firewall and DCOM on Computer B in the Configuration section. Connection 2 represents Computer B's response to Computer A. Generally speaking, both connections (1 and 2) are asynchronous.
WMI Is Classy
Remember that class stuff we were talking about earlier? Well, there are tons of WMI classes. If you visit Microsoft's Win32 Provider page, you'll find four broad class categories. Click on Operating System Classes, and you'll see a big list of WMI classes representing objects related to the operating system. From there, click on the class Win32_ComputerSystem. This'll bring up a long list of things that you can learn about a particular Windows device. For instance, you can find out whether a computer belongs to a domain, how many processors it has, its power status, its time zone, and the name of the user currently logged on. And that's just scratching the surface!
Win32_ComputerSystem is one of many operating system classes. If you jump over to the Computer System Hardware Classes, you'll see a lot of hardware-related classes. Check out the class Win32_NetworkAdapter, for example. You can use this class to find out more than you ever wanted to know about a computer's network adapter.
SevOne's WMI plugin takes full advantage of WMI's power and flexibility. Once you set up your devices for WMI polling, you can create hundreds of indicator types based on WMI classes. These indicator types provide you all kinds of statistics about CPU usage, hard drive usage, memory usage, and ASP.NET, for example.
SevOne NMS only ingests Win32_PerfFormattedData classes.
Classes in Action
This is optional. If you would like to see WMI classes in action, open up PowerShell and try out the following commands. Otherwise, proceed to the next section to get started with WMI monitoring using SevOne NMS.
-
The extension class Win32_ComputerSystem represents a computer system running Windows. It's extended from a class called CIM_UnitaryComputerSystem. The CIM_UnitaryComputerSystem class represents any number of single-node computer systems, including desktops, laptops, servers, etc. The following command returns the manufacturer and model of a computer.
Get-WmiObject Win32_ComputerSystem | Select Manufacturer,Model -
Now try something from the Windows Performance Counter Classes. The following command employs the Win32_PerFormattedData_PerfProc_Process extension class and returns the amount of non-paged pool memory in bytes.
Get-WmiObject Win32_PerfFormattedData_PerfProc_Process | Select PoolNonpagedBytes
Prerequisites
Before we get started, you'll need to have the following information handy for the proxy server as well as for any devices that you plan to monitor using WMI.
Proxy Server
-
Name
-
IP address
-
Port number to use (default is 3000)
Devices Monitored via WMI
-
User name and password
-
Name of workgroup or domain
-
Authentication protocol: NT LAN Manager (NTLM) or Kerberos?
Configuration Steps
In this section, we'll cover all of the steps needed to set up your devices to be monitored with SevOne's WMI plugin. This section includes the following topics:
-
Setting up WMI proxy servers
-
Configuring the Windows devices that you're going to monitor
-
Enabling the WMI plugin for the devices you're going to monitor
-
Enabling and managing WMI object types and indicator types
Set up a WMI proxy server
The proxy server is the Windows device that sends WMI queries to any Windows devices you'd like to monitor with SevOne's WMI plugin. SevOne NMS provides a Windows service for your proxy server, and we'll be installing that as part of the setup. During the setup process, we'll be jumping back and forth between SevOne NMS and your proxy server.
-
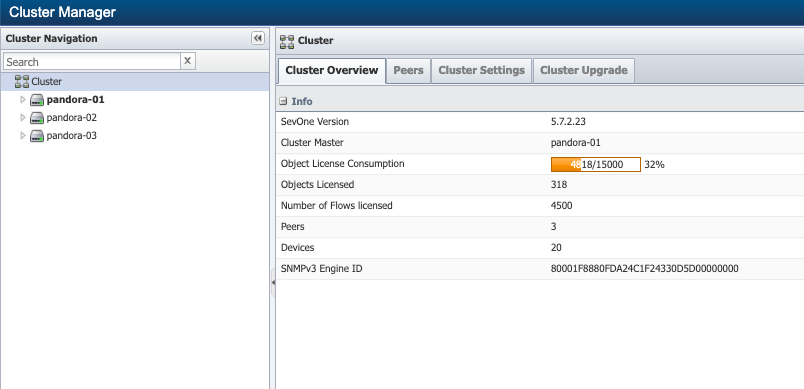
In SevOne NMS, click the Administration menu and select Cluster Manager.
-
Select the Cluster Settings tab.
-
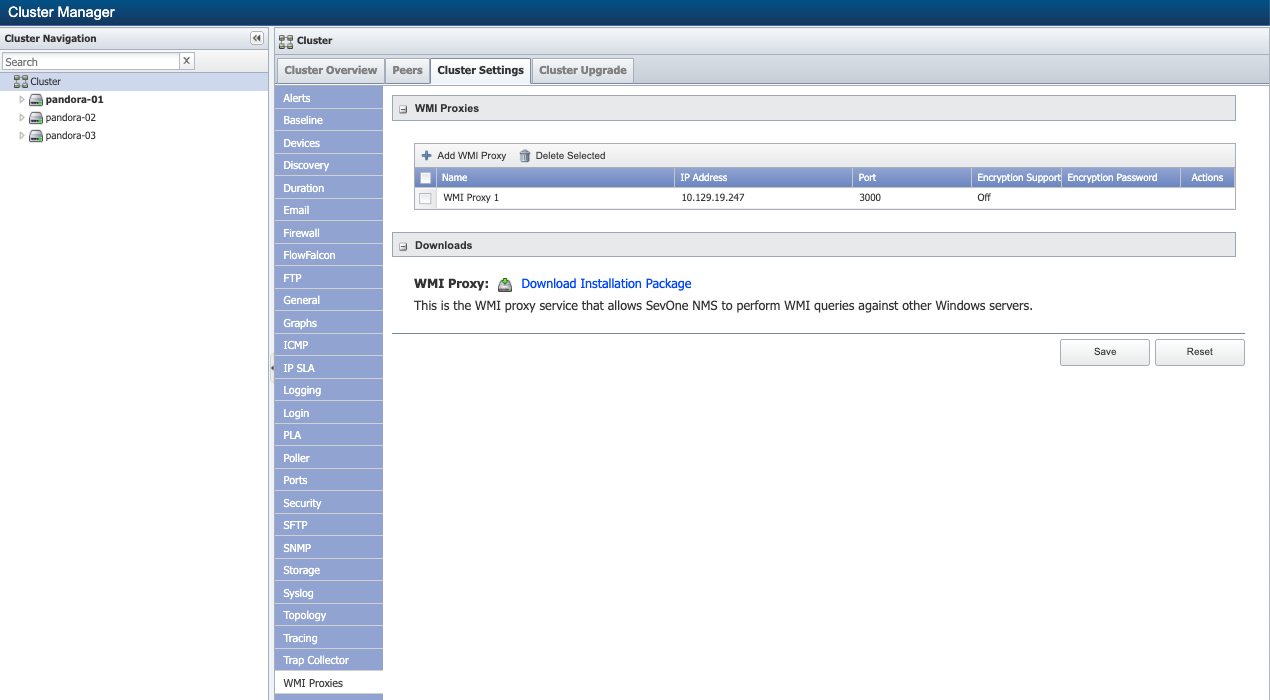
On the left, scroll down and select the WMI Proxies subtab.
-
Under Downloads, next to WMI Proxy, click the Download Installation Package link. Then save the file WMIServerServiceSetup.exe to your proxy server.
-
If the proxy server isn't running the Microsoft .NET 3.5 framework, you'll need to download it. Next to .NET 3.5 Framework, click the Download Installation Package link. Then save the file setup.exe to the proxy server.
-
Go to your proxy server.
-
Log in as the local administrator.
-
If needed, run the .NET 3.5 Framework setup.exe .
-
Run the file WMIServerServiceSetup.exe to install SevOne NMS WMI Proxy.
-
In Windows, click the Start button to display the Start menu.
-
In the search field, type services.msc and hit Enter to display Windows Services.
-
The services are listed in the right pane. Right-click on SevOne WMI Proxy and select Start.
-
Return to SevOne NMS.
-
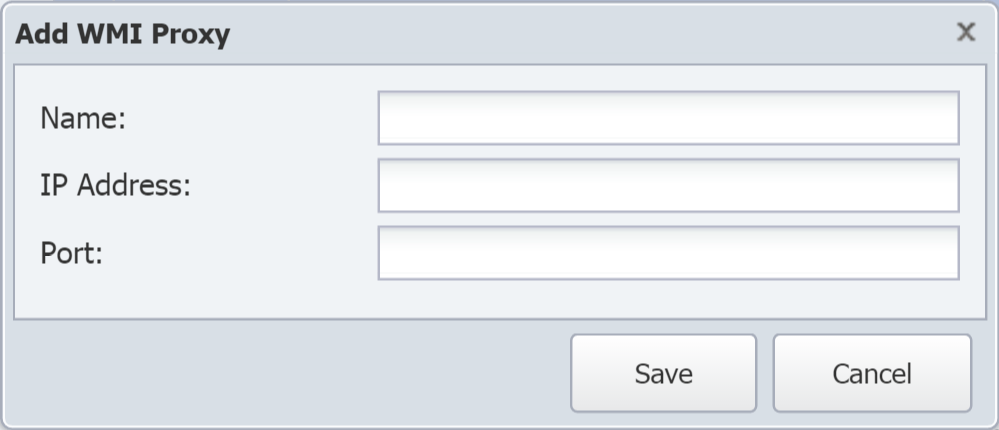
On the Cluster Settings tab > WMI Proxies s ubtab, click Add WMI Proxy to display the Add WMI Proxy pop-up.
-
In the Name field, enter the name of the proxy server.
-
In the IP address field, enter the proxy server IP address.
-
In the Port field, enter the port that the proxy server will use to communicate with SevOne NMS. The default is 3000.
-
Click Save.
-
At the bottom right of the page, click Save to save your settings.
Prepare Windows Devices
Your proxy server is set up and ready to start asking some questions. Now we've got to configure the devices you plan to monitor so they can send responses back to the proxy. All of our work in this subsection will be performed within Windows. Once we're done here, we will have accomplished three things:
-
Enable WMI on the devices you plan to monitor
-
Allow remote administration on those same devices
-
Enable the devices to communicate back to the WMI proxy
The work we'll be doing here is outside of SevOne NMS and may require additional steps depending on your specific device and operating system. The steps below are based on Windows 7 and should work with Windows 8 as well. We've included deprecated versions of the commands for the CLI, which may be useful if you're working with an older version of Windows.
Enable WMI
You'll need to start the WMI service for the Windows devices you'd like to monitor. Perform the following steps for each device.
-
Click the Start button to display the Start menu.
-
In the search field, type services.msc and hit Enter to display Windows Services.
-
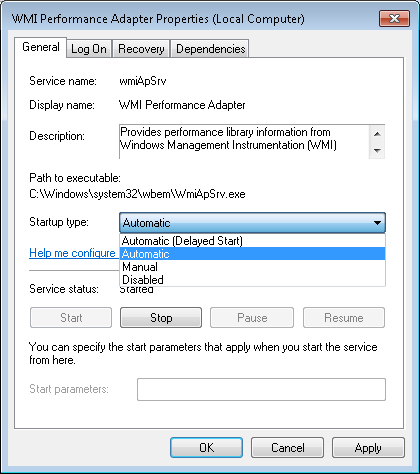
In the right pane, right-click on WMI Performance Adapter and select Properties.
-
Select the General tab.
-
Click the Startup type drop-down and select Automatic. This will set the service to start every time the computer starts.
-
Click OK to apply the change and close the pop-up.
Allow Remote Administration
After you've enabled WMI on a device, you'll need to configure it to be managed remotely. You can do this either through the Control Panel or using the command line. The following instructions are based on Windows 7 and should work with Windows 8 as well.
Option 1: GUI
-
Click the Start button to display the Start menu.
-
In the search field, type gpedit.msc and hit Enter to display the Local Group Policy Editor.
-
In the left pane, expand Computer Configuration.
-
Expand Administrative Templates.
-
Expand Network.
-
Expand Network Connections.
-
Expand Windows Firewall, then perform one of the following actions:
-
If the device belongs to the domain, select the Domain Profile folder.
-
If the device doesn't belong to the domain, select the Standard Profile folder.
-
-
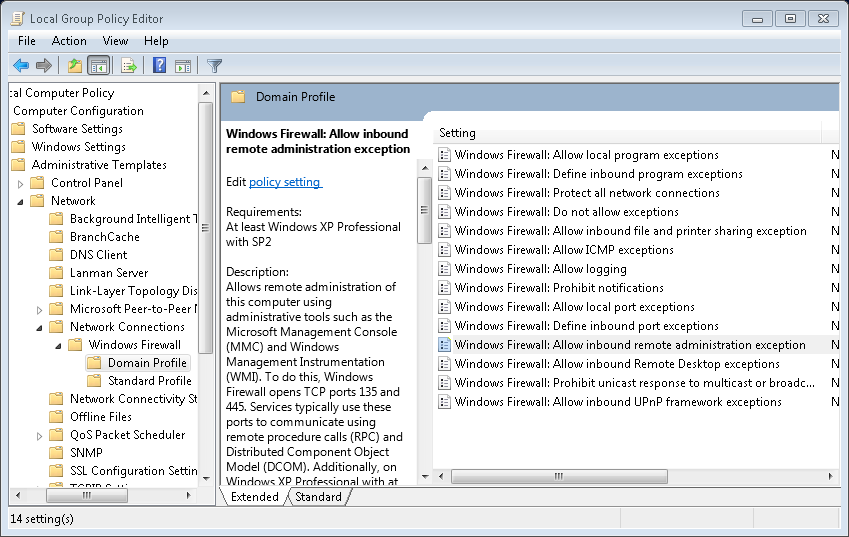
In the right pane, you'll see a list of policy settings. Double-click on the one that says Windows Firewall: Allow inbound remote administration exception.
-
This will display a pop-up where you can edit the policy setting. In the upper left area of the pop-up, select the Enabled radio button.
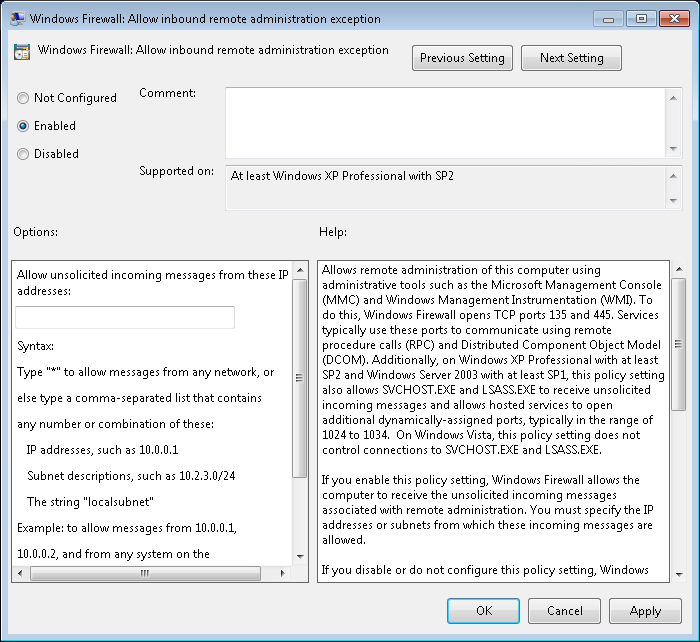
-
Click OK to apply the change and save.
Option 2: Command Line
Perform the following steps.
-
In Windows, click the Start button. Then type cmd in the search bar, but don't hit Enter.
-
Under Programs, right click on cmd and select Run as administrator. If you're not logged in as an administrator, you'll need to enter administrator credentials.
-
At the command prompt, type the following command, then hit Enter.
netsh advfirewall firewallsetrule group="Windows Remote Management"newenable=yes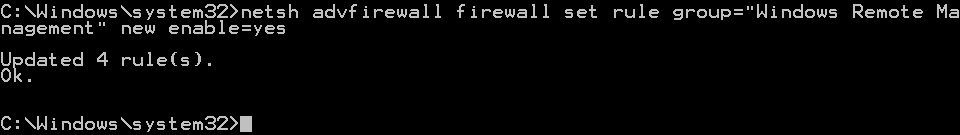
The following is the deprecated version of the command.
netsh firewallsetservice RemoteAdminenable
Enable Windows Devices to Respond to the WMI Proxy
Going back to the diagram we looked at earlier, the connection from Computer B to Computer A (Connection 2) is only necessary when the client script or application on Computer A makes an asynchronous call to Computer B. If Computer B belongs to a workgroup or a domain that isn't trusted by Computer A, then Connection 2 becomes an anonymous connection.
-
If Windows Firewall is enabled on the proxy (Computer A from the diagram), run the following command on it to enable Allow remote administration exception and to open DCOM port TCP 135 on the proxy.
netsh advfirewall firewall add ruledir=inname="DCOM"program=%systemroot%\system32\svchost.exe service=rpcss action=allow protocol=TCP localport=135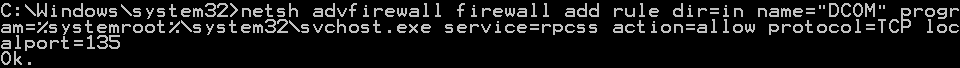
The following is the deprecated version of the command.
netsh firewall add portopening protocol=tcp port=135 name=DCOM_TCP135 -
Next, you'll need to add the client application script, Unsecapp.exe, to the Windows Firewall Exception List on the proxy (Computer A). Unsecapp.exe acts as the WMI callback client and it's used specifically for asynchronous operations. If a process doesn't have DCOM permission, unsecapp.exe is used to send data back to the client because it takes callbacks from everyone.
netsh advfirewall firewall add ruledir=inname="UnsecApp"program=%systemroot%\system32\wbem\unsecapp.exe action=allow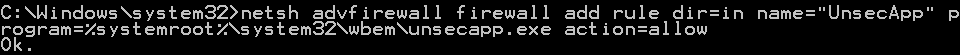
The following is the deprecated version of the command.
netsh firewall add allowedprogram program=%windir%\system32\wbem\unsecapp.exe name=UNSECAPP
Something Extra: Try out WMIC Commands
This is optional. You can use WMIC commands to test the WMI setup on the devices to be monitored. To do this, find a computer that's on the same network as the device you'd like to send commands to. This computer would play the role of Computer A role from the diagram above.
Before getting started, you'll need to know the host name of the computer you're sending commands to (that is, the device playing the role of Computer B) and, if possible, its IP address. Also, make sure that computer is powered on.
These quick steps will get you started:
-
Open the command line interface (CLI) on your computer (Computer A).
Run the CLI as an administrator if you're not already logged into Windows as an admin.
-
At the command prompt, type in wmic, then hit Enter.

-
At the WMIC prompt, type the following command and hit Enter. Replace [host name] with the computer's host name or IP address. This should return the user name.
/node:[host name] computersystem get username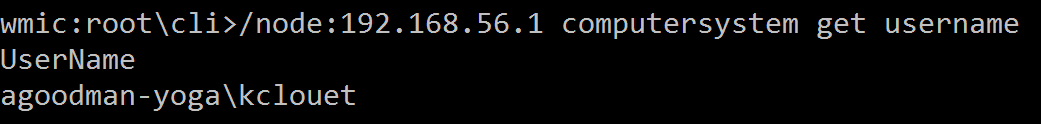
-
Try the following command to return the machine's serial number.
/node:[host name] bios get serialnumber
Enable WMI Plugin
The WMI plugin enables you to monitor Windows Management Instrumentation data, including CPU usage, ASP.NET, hard drive usage, and memory usage. It's disabled on new devices by default because it requires device-specific configuration.
Perform the following steps to enable the WMI plugin for devices .
-
From the navigation bar, click Devices and select Device Manager.
-
Perform one of the following actions.
-
To add a new device, click Add Device under Devices to display the New Device page. For information on adding new devices, please see our documentation on the topic.
-
To edit an existing device, select the device and click
 to display the Edit Device page.
to display the Edit Device page.
-
-
The plugin section appears in the lower half of the page. It's set to SNMP by default.
-
Next to SNMP, click the drop-down and select WMI.

-
Select the WMI Capable check box.
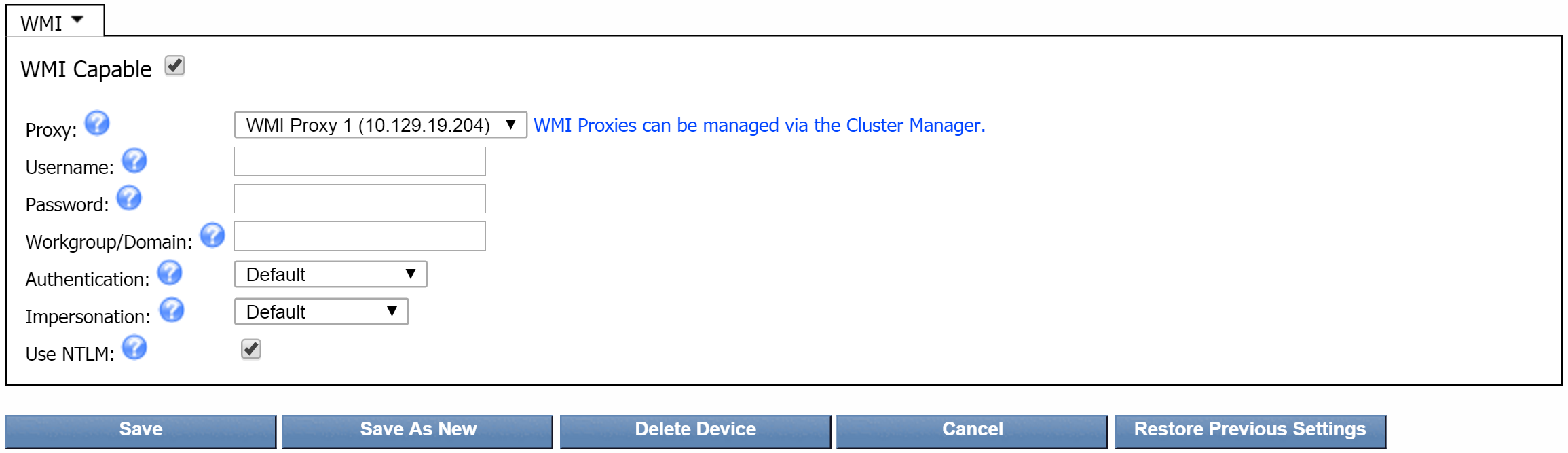
-
Click the Proxy drop-down and select a proxy server to poll WMI data for your device. If you don't see the proxy server that you're looking for, click the WMI Proxies can be managed via the Cluster Manager link to the right of the Proxy field. This will take you to the Cluster Manager, where you can add and edit proxy servers.
-
In the Username field, enter the user name that the proxy needs to authenticate onto the device.
-
In the Password field, enter the password that the proxy needs to authenticate onto the device.
-
In the Workgroup/Domain field, enter the workgroup or domain that the device belongs to.
-
Click the Authentication drop-down and select the authentication level required to access the device. This is typically set to Default or Packet. You may need to experiment with one of the Advanced methods.
-
Click the Impersonation drop-down and select the impersonation level for accessing the device. This is typically set to Default or Impersonate.
-
Select the Use NTLM check box to use Microsoft's NT LAN Manager (NTLM). Leave this check box clear if your network uses Kerberos.
Kerberos has replaced NTLM as the default authentication protocol in an Active Directory-based single sign-on scheme.
-
Click Save.
Manage WMI Object Types
In this section, we'll look at the Object Types page, where you can manage WMI object types. Object types let you determine which objects are discovered on a device. The WMI plugin discovers the WMI indicator types for the object types you enable. WMI object types are disabled by default. The Object Rules page lets you define rules to disable polling of objects, and the Object Manager lets you manage the objects on each device.
Perform the following steps to add and edit WMI object types.
-
From the navigation bar, click Administration and select Monitoring Configuration, then Object Types.
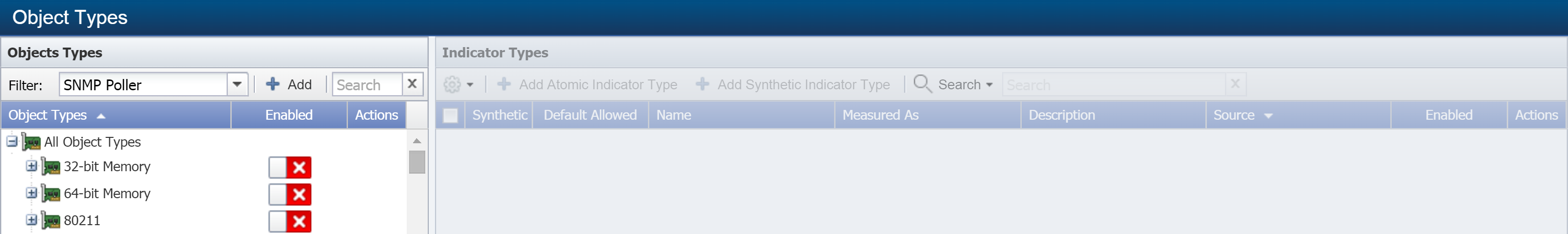
-
Click the Filter drop-down and select WMI Poller. In the Object Types hierarchy on the left, you'll see the object types that the WMI plugin can poll.
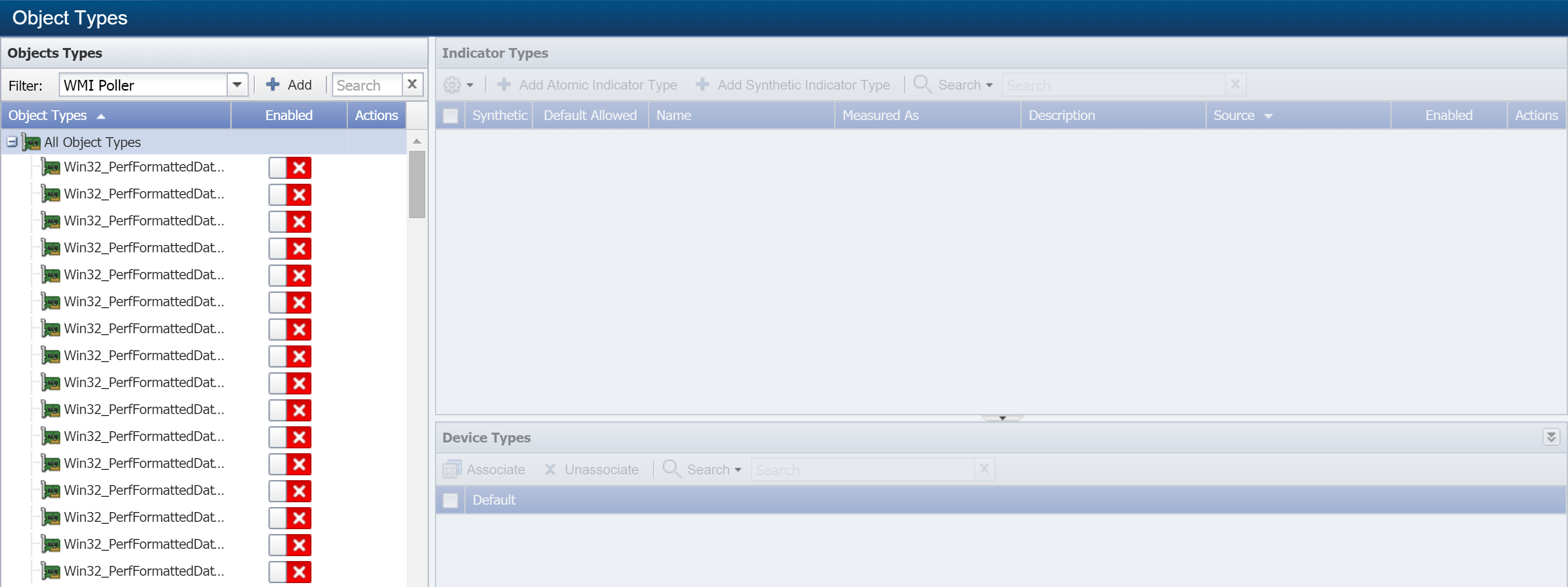
-
Click Add to display the Add WMI Object Type pop-up. To edit an existing object type, select the object type and click
 under Actions.
under Actions. 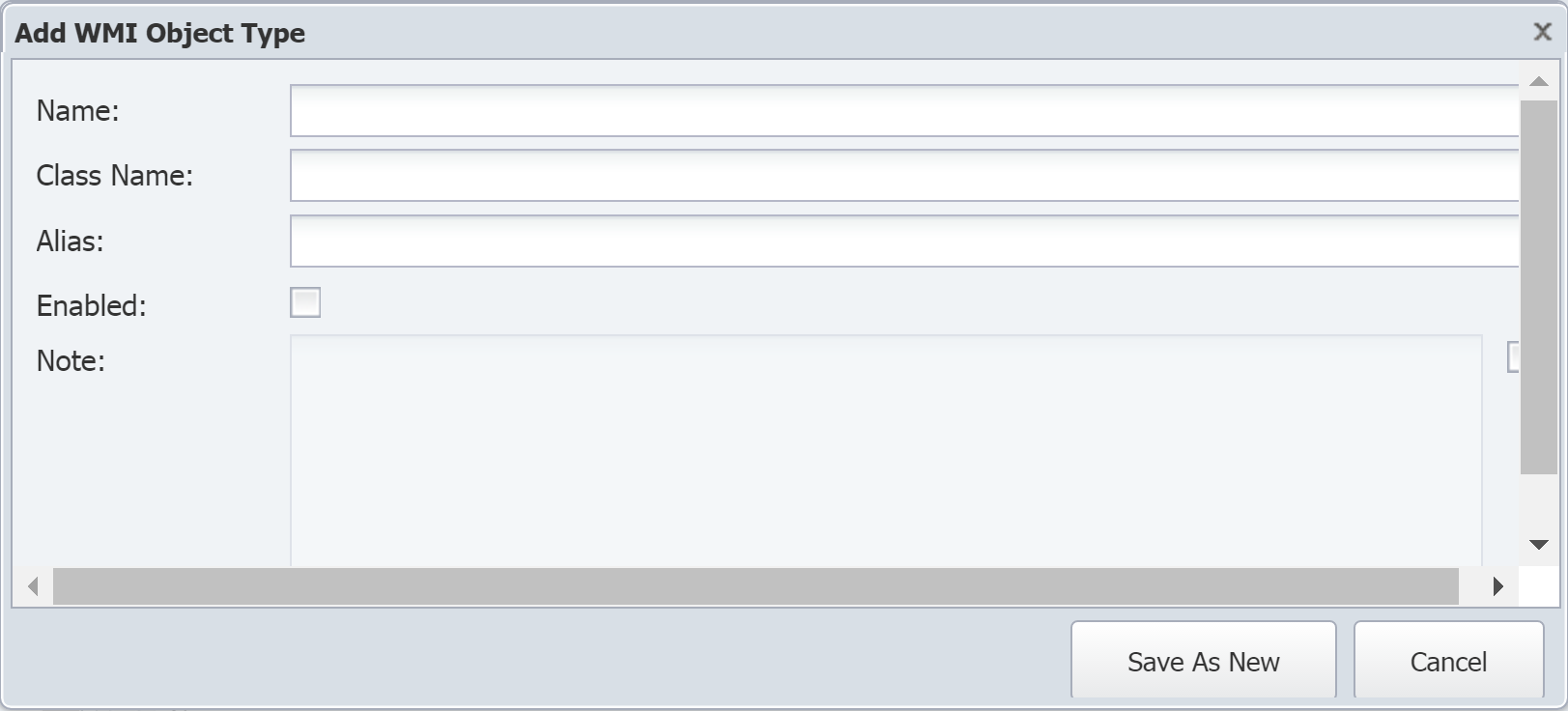
-
In the Name field, enter the object type name.
-
In the Class Name field, enter the object type class name .
-
In the Alias field, enter an alias for the object type.
-
Select the Enabled check box to enable the WMI plugin to poll the indicator types for this object type.
-
Select the check box for the Note field to enable it for editing. Enter any additional information you would like to include.
-
Click Save As New.
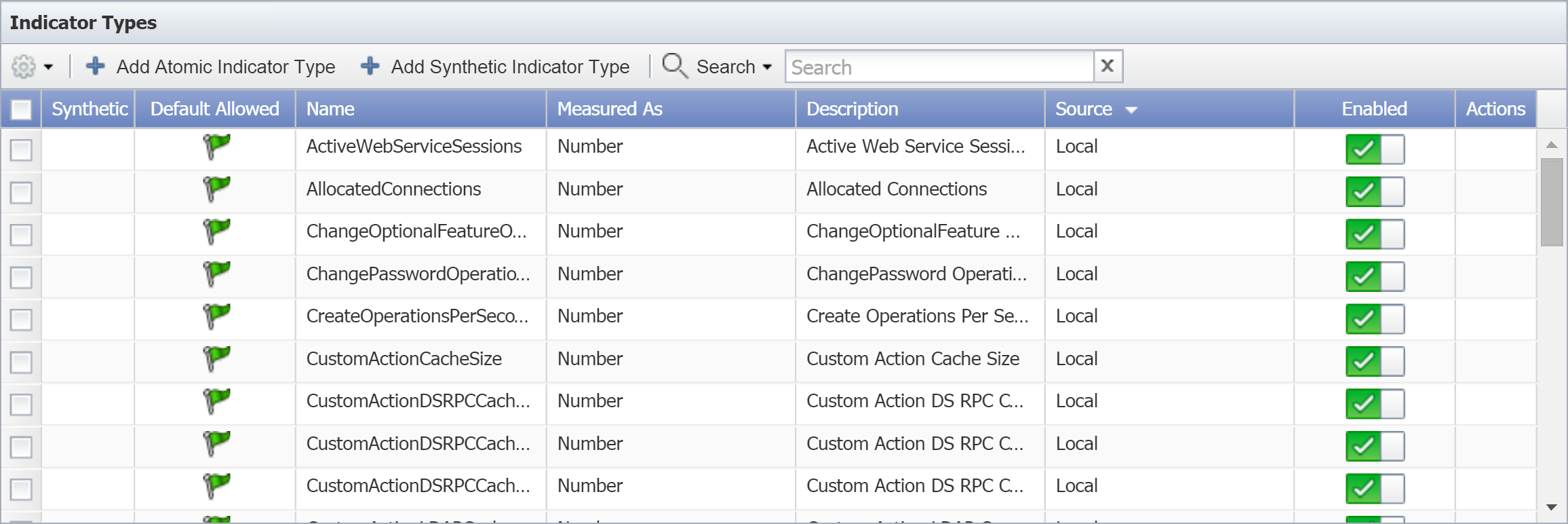
Manage WMI Indicator Types
Indicator types define the kind of metrics an object can have. In this section, we'll walk through the steps for adding (and editing) indicator types. Every indicator of an object needs an indicator type. SevOne NMS plugins–such as SNMP, WMI, etc.–use indicator types to collect data from indicators on the objects that you monitor. For example, the WMI DHCP Server object type has an indicator type to measure how many packets are received per second.
There are two categories of indicator types: atomic and synthetic. Atomic indicator types are measured directly by plugins. Synthetic indicator types, on the other hand, calculate values based on the values resulting from other indicator types.
WMI Atomic Indicator Types
Perform the following steps on the Object Types page to add and edit WMI atomic indicator types.
-
In the Object Types hierarchy on the left, select the object type that you would like to create an indicator type for.
-
On the right side of the page, under Indicator Types, click Add Atomic Indicator Type to display th e Add WMI Indicator Type pop-up . To edit an existing indicator type , select the indicator type and click
 under
Actions
.
under
Actions
.
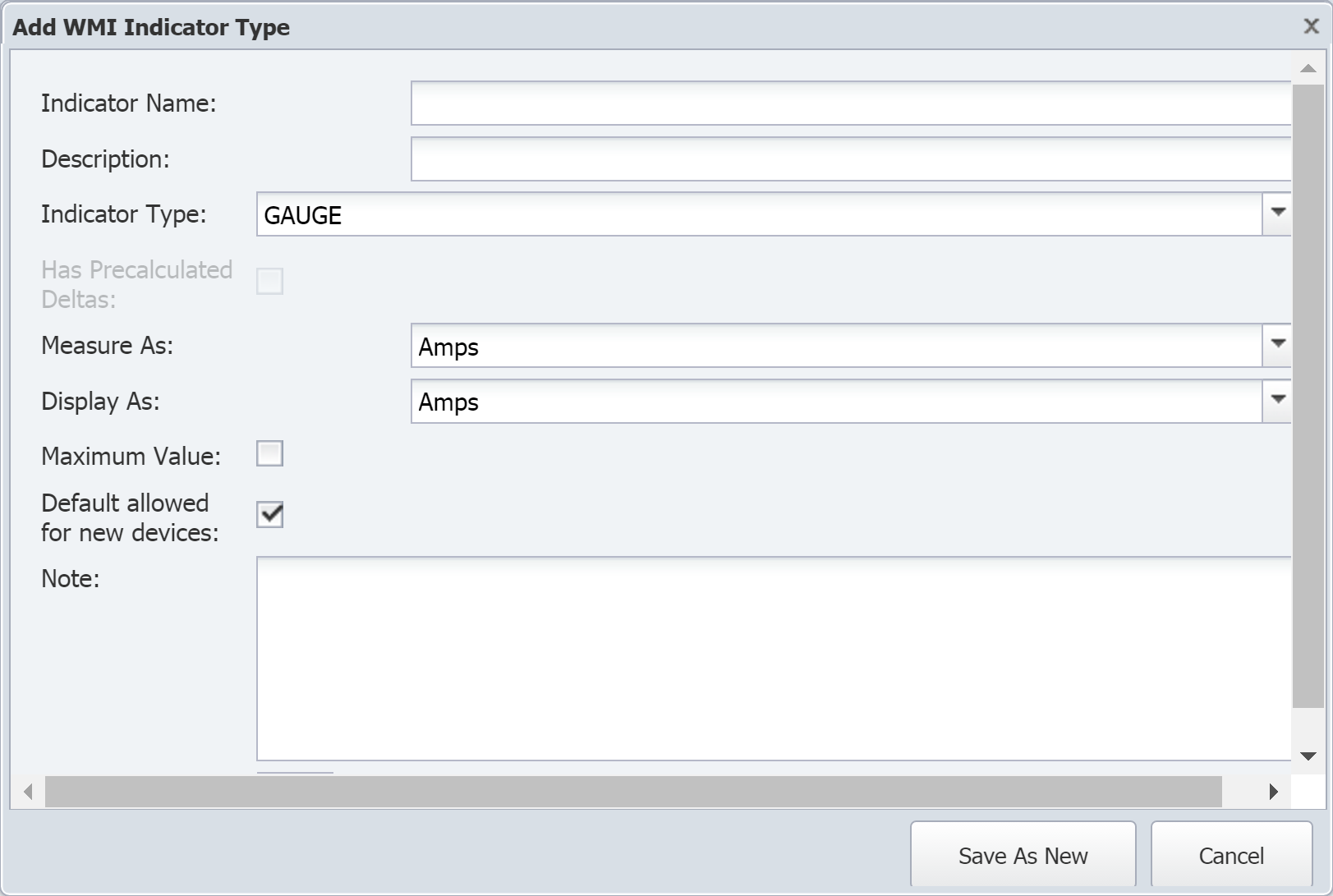
-
In the Indicator Name field, enter the name of the indicator type.
-
In the Description field, enter the name to display.
You'll see the indicator description displayed in reports and elsewhere in the UI. Keep this in mind when creating the indicator type description. For example, when you look at an object's indicators, you'll notice that they're listed based on the first word of their description. If you have the two indicators Queued Bytes and Transmitted Bytes , they may not appear together. However, if you use the descriptions Bytes Queued and Bytes Transmitted, the indicators will appear in close proximity to each other.
-
Click the Indicator Type drop-down and select one of the following options:
-
GAUGE - for indicators that have specific values when polled.
-
COUNTER32 - for 32-bit indicators that continue to increment. If you select this option, you can select the Has Precalculated Deltas check box to total the delta/differences between polls. This provides the ability to graph things like the number of errors in a day, for example.
-
COUNTER64 - for 64-bit indicators that continue to increment. If you select this option, you can select the Has Precalculated Deltas check box.
-
-
Click the Measure As drop-down and select a unit to measure data as–for example, bits, bytes, percent, seconds, etc.
-
Click the Display As drop-down and select a unit to display results as. The options available here are based on your selection for the Measure As field.
-
Select the Maximum Value check box to indicate that the indicator type has a maximum value.
-
Select the Default allowed for new devices check box to have the plugin poll this indicator type by default when the object type is enabled and when the plugin for a device is enabled.
-
In the Note field, enter any additional information you would like to include.
-
Click Save As New.
WMI Synthetic Indicator Types
Using synthetic indicator types, you can create your own key performance indicators (KPIs) even when those KPIs–such as Percent Usage, Percent Loss, Percent Error, and Percent Idle–don't exist on a device. For example, let's say that you want to monitor voice gateways to find out which primary rate interface (PRI) is getting the most usage. Typical poll metrics can tell you the busy status of individual bearer channels, or B channels, but they can't tell you the sum of the statuses for all the B channels. This makes it difficult to find out the total usage of a particular PRI.
In SevOne NMS, you can create a single indicator type that tells you what percentage of a PRI is being used.
First, we need the following:
-
An existing indicator type that tells us how many busy B channels there are for a given PRI. Let's call this BChannelsBusy.
-
The total number of B channels for our PRI. That number is 23.
Using this information, we can create a synthetic indicator type with an expression to perform the following calculation:
(BChannelsBusy*23)/100
Now we have a new indicator type–a synthetic indicator type–that tells us what percentage of the PRI is being used. There's no need to look up the number of busy B channels and perform calculations manually.
Since synthetic indicator types are based on existing indicator types–either synthetic or atomic–there must already be at least one existing indicator type in order for you to create a new synthetic indicator type.
Perform the following steps on the Object Types page to add and edit WMI synthetic indicator types.
-
In the Object Types hierarchy on the left, c lick on an object type to display its indicator types on the right. If the object type doesn't have any indicator types, the Add Synthetic Indicator Type button won't appear.
-
Click Add Synthetic Indicator Type to display the Add Synthetic Indicator Type pop-up. To edit an existing synthetic indicator type, select the indicator type and click
 under Actions.
under Actions. 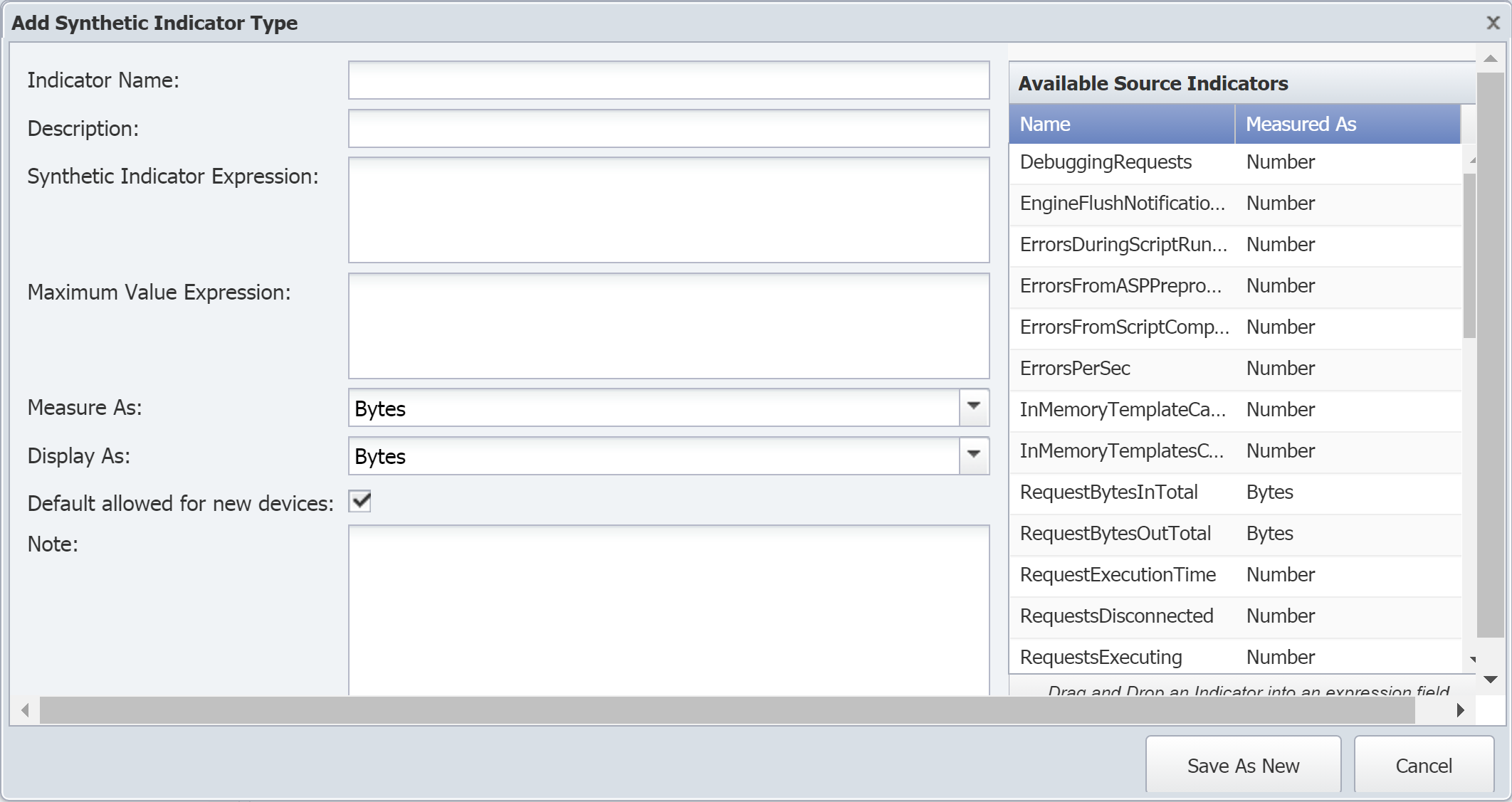
-
In the Indicator Name field, enter the name of the synthetic indicator type.
-
In the Description field, enter the name to display.
You'll see the indicator description displayed in reports and elsewhere in the UI. Keep this in mind when creating the indicator type description. For example, when you look at an object's indicators, you'll notice that they're listed based on the first word of their description. If you have the two indicators Queued Bytes and Transmitted Bytes , they may not appear together. However, if you use the descriptions Bytes Queued and Bytes Transmitted, the indicators will appear in close proximity to each other.
-
The Synthetic Indicator Expression field is where you define the calculation. Perform the following actions to create the expression for this field.
A red border around the Synthetic Indicator Expression field indicates that your calculation is invalid. This also means that your graph results will be incorrect.
-
In the Available Source Indicators field on the right, select an indicator type to use in the expression. Drag and drop it into the Synthetic Indicator Expression field.
The Available Source Indicators field contains the indicator types for the object type that you selected a few steps ago.
-
Next, enter the applicable operators to formulate your calculation in the Synthetic Indicator Expression field. For a list of available operators, see Acceptable Operators below.
-
Drag any additional indicator types from the Available Source Indicators field and enter additional mathematical symbols to complete the expression in the Synthetic Indicator Expression field.
-
-
The Maximum Value Expression field lets you define a maximum value calculation for the indicator type. Perform the following actions to create the expression for this field.
-
In the Available Source Indicators field on the right, select an indicator type to use in the expression. Drag and drop it into the Maximum Value Expression field.
-
Next, enter the applicable operators to formulate your calculation in the Maximum Value Expression field. For a list of available operators, see Acceptable Operators below.
-
Drag any additional indicator types from the Available Source Indicators field and enter additional mathematical symbols to complete the expression in the Maximum Value Expression field.
-
-
Click the Measure As drop-down and select a unit to measure data as–for example, bits, bytes, percent, seconds, etc.
-
Click the Display As drop-down and select a unit to display results as. The options available here are based on your selection for the Measure As field.
-
Select the Default allowed for new devices check box to have the plugin poll this indicator type by default when the object type is enabled and when the plugin for a device is enabled.
-
In the Note field, enter any additional information you would like to include.
-
Click Save As New.
Your expression formula can include the following characters:
-
+ add
-
- subtract
-
* multiply
-
/ divide
-
&& logical AND
-
|| logical OR
-
<= less than or equal to
-
>= greater than or equal to
-
! not equal to
-
== equal to
-
> greater than
-
< less than
-
^ raise x to the power of y
-
% modulus
-
?: if...then...else
-
isnan is Not a Number. This evaluates to 1 if the value is not a number. Otherwise, it evaluates to 0.
-
isValid is valid. This evaluates to 1 if the value has been discovered and is not isnan. Otherwise, it evaluates to 0.
-
useIfValid use if valid. This evaluates to the value if it has been discovered and is not isnan. It evaluates to the second argument otherwise.
If your calculation results in either of the following invalid values, there will be a gap in your graph:
-
Not a Number (NAN)
-
Infinity (+/-INF).
The following describes how SevOne NMS attempts to prevent invalid values. These are listed in the order that they're processed.
-
Zero divided by zero results in NAN.
-
Any positive value divided by zero results in +INF.
-
Any negative value divided by zero results in -INF.
-
Zero multiplied by +/-INF results in NAN.
-
Any value added to, subtracted from, multiplied by, divided by, or divided from NAN results in NAN.
-
Any value compared to NAN (<, <=, ==, >=, >) results in 0. NAN != NAN.
-
Any value compared to +INF is less than +INF, except that +INF == +INF
-
Any value compared to -INF is greater than -INF, except that -INF == -INF
-
Any value added to or subtracted from +INF results in +INF
-
Any positive value multiplied by +/-INF results in +/-INF
-
Any value divided by +/-INF results in 0
Tips
For optimal performance, we recommend doing the following:
-
Always make sure that communication is possible between SevOne NMS and the proxy server.
-
Always make sure that communication is possible between the proxy server and all monitored WMI servers.
-
Configuring Authentication and Impersonation may be tricky. Try a few combinations when attempting to discover new WMI servers. As a general rule, when it works for one WMI server, it will likely work for the rest of them.
Terms & References
Terms
|
Common Information Model (CIM) |
An open standard that provides a schema for organizing managed objects on a network. |
|
Distributed Component Object Model (DCOM) |
A Microsoft technology that enables software to communicate across a network. |
|
Distributed Management Task Force (DMTF) |
An organization that develops and implements standards for simplified management of network technologies. |
|
Windows Management Instrumentation (WMI) |
A collection of tools and extensions that enable both local and remote management of Windows-based systems and applications. |
References
Win32 Provider - Microsoft page for the Win32 Provider component.