Table of Contents (Start)
- Topics
- Introducing SevOne
- Login
- Startup Wizard
- Dashboard
- Global Search - Advanced Search
- Report Manager
- Report Attachment Wizard
- Report Properties
- Report Interactions
- Instant Graphs
- TopN Reports
- Alerts
- Alert Archives
- Alert Summary
- Instant Status
- Status Map Manager
- Edit Maps
- View Maps
- FlowFalcon Reports
- NBAR Reports
- Logged Traps
- Unknown Traps
- Trap Event Editor
- Trap Destinations
- Trap Destination Associations
- Policy Browser
- Create and Edit Policies
- Threshold Browser
- Create and Edit Thresholds
- Probe Manager
- Discovery Manager
- Device Manager
- New Device
- Edit Device
- Object Manager
- High Frequency Poller
- Device Summary
- Device Mover
- Device Groups
- Object Groups
- Object Summary
- Object Rules
- VMware Browser
- Calculation Plugin
- Cisco ACI Plugin
- Database Manager
- Deferred Data Plugin
- DNS Plugin
- HTTP Plugin
- ICMP Plugin
- IP SLA Plugin
- JMX Plugin
- NAM
- NBAR Plugin
- Portshaker Plugin
- Process Plugin
- Proxy Ping Plugin
- SNMP Plugin
- VMware Plugin
- Web Status Plugin
- WMI Plugin
- xStats Plugin
- Indicator Type Maps
- Device Types
- Object Types
- Object Subtype Manager
- Calculation Editor
- xStats Source Manager
- User Role Manager
- User Manager
- Session Manager
- Authentication Settings
- Preferences
- Cluster Manager
- Maintenance Windows
- Processes and Logs
- Metadata Schema
- Baseline Manager
- FlowFalcon View Editor
- Map Flow Objects
- FlowFalcon Views
- Flow Rules
- Flow Interface Manager
- MPLS Flow Mapping
- Network Segment Manager
- Flow Protocols and Services
- xStats Log Viewer
- SNMP Walk
- SNMP OID Browser
- MIB Manager
- Work Hours
- Administrative Messages
- Enable Flow Technologies
- Enable JMX
- Enable NBAR
- Enable SNMP
- Enable Web Status
- Enable WMI
- IP SLA
- SNMP
- SevOne Data Bus
- Quality of Service
- Perl Regular Expressions
- Trap Revisions
- Integrate SevOne NMS With Other Applications
- Email Tips and Tricks
- SevOne NMS PHP Statistics
- SevOne NMS Usage Statistics
- Glossary and Concepts
- Map Flow Devices
- Trap v3 Receiver
- Guides
- SevOne Implementation Guide
- SevOne Best Practices Guide - Cluster, Peer, and HSA
- SevOne Installation Guide - Virtual Appliance
- SevOne NMS Installation Guide
- SevOne SAML Single Sign-On Setup Guide
- Access Control Quick Start Guide - SevOne NMS 5.7
- Data Miner Quick Start Guide - SevOne NMS 5.7
- Flow Quick Start Guide - SevOne NMS 5.7
- Group Aggregated Indicators Quick Start Guide - SevOne NMS 5.7
- IP SLA Quick Start Guide - SevOne NMS 5.7
- JMX Quick Start Guide - SevOne NMS 5.7
- LDAP Quick Start Guide - SevOne NMS 5.7
- Metadata Quick Start Guide - SevOne NMS 5.7
- RESTful API Quick Start Guide - SevOne NMS 5.7
- Self-monitoring Quick Start Guide - SevOne NMS 5.7
- SevOne NMS Admin Notifications Quick Start Guide - SevOne NMS 5.7
- SNMP Quick Start Guide - SevOne NMS 5.7
- Synthetic Indicator Types Quick Start Guide - SevOne NMS 5.7
- Topology Quick Start Guide - SevOne NMS 5.7
- VMware Quick Start Guide - SevOne NMS 5.7
- Web Status Quick Start Guide - SevOne NMS 5.7
- WMI Quick Start Guide - SevOne NMS 5.7
- xStats Quick Start Guide - SevOne NMS 5.7
Flow Quick Start Guide - SevOne NMS 5.7
SevOne Documentation
All SevOne user documentation is available online from the SevOne Support customer portal.
Copyright © 2005-2020 SevOne Inc. All rights reserved worldwide.
All right, title, and interest in and to the software and documentation are and shall remain the exclusive property of SevOne and its respective licensors. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of SevOne.
In no event shall SevOne, its suppliers, nor its licensors be liable for any damages, whether arising in tort, contract, or any other legal theory even if SevOne has been advised of the possibility of such damages, and SevOne disclaims all warranties, conditions, or other terms, express or implied, statutory or otherwise, on software and documentation furnished hereunder including without limitation the warranties of design, merchantability, or fitness for a particular purpose, and noninfringement.
All SevOne marks identified or used on the SevOne website, as updated by SevOne from time to time, may be, or are, registered with the U.S. Patent and Trademark Office and may be registered or pending registration in other countries. All other trademarks or registered trademarks contained and/or mentioned herein are used for identification purposes only and may be trademarks or registered trademarks of their respective companies.
We've Got Flow
Most enterprise-level routers and switches come equipped with some type of flow technology. And with good reason: IT folks use flow records to troubleshoot a wide range of network issues.
Flow technology was originally intended as a way to optimize packet routing. It all started back in the 1990s, when Cisco Systems invented the NetFlow protocol. The idea behind it was that a NetFlow-enabled router would create a table that maintained a cache of routing decisions. In this table, the router would store all the necessary information to route a given packet. When later packets came in with the same signature as the previous packet, the router could use the information from the table to route those packets without having to start from scratch. This saved the router from having to perform the same calculations repeatedly. Eventually, other approaches to packet routing took over, but the information contained in those tables turned out to be pretty valuable in other ways.
Nowadays, a lot of vendors use network flow technologies similar to Cisco's NetFlow. A network flow record contains a number of attributes, including:
-
Source IP address
-
Destination IP address
-
Source port
-
Destination port
-
Layer 3 protocol type
-
Type of Service (ToS)
-
Router/switch input interface
Flow records can tell us things like where traffic's coming from and where it's going. It can tell us who's using our bandwidth and what they're using it for. It can also help us track down the cause of both minor and major network problems, such as network slowdowns, poor VoIP call quality, and security vulnerabilities, for example.
In the following sections, we'll cover all aspects of collecting and reporting on flow technologies in SevOne NMS. Before you do anything else, you'll need to enable your devices to send flow to SevOne NMS. You'll do that part outside of SevOne NMS, but we'll look at examples for a few of the devices supported by SevOne. SevOne supports flow monitoring for tons of devices, so if you don't see yours listed in the examples, you might need to check with the device manufacturer to get specific instructions for your device.
Prepare Your SevOne Appliance
This section applies only if your SevOne appliance has more than one network interface card (NIC).
If your SevOne appliance has more than one NIC, you'll need t o disable reverse path filtering.
In order to do this, you'll need to have the following on-hand:
-
IP address of the appliance. You'll need the IP address or hostname of your SevOne appliance.
-
Root access to the appliance. You'll also need the root user name and password for your SSH session.
-
An SSH client. You'll need an SSH client such as PuTTY.
Perform the following steps to disable reverse path filtering.
-
Open your SSH client and log into your SevOne appliance as the root user.
-
Execute the following command.
echo0 >/proc/sys/net/ipv4/conf/all/rp_filter
Enable Devices to Send Flow Data
Before getting started, you'll need to make sure your devices are enabled to send flow data to SevOne NMS. In this section, we'll discuss recommended settings and then look at steps for enabling flow on some specific devices.
Sampled Flow Data Versus Non-sampled Flow Data
SevOne NMS automatically calculates the flow rate for sampled flow data and dynamically adjusts the calculation when the flow rate changes. Following is port information for sampled and non-sampled flow data.
-
Sampled flow data - SevOne NMS uses port 6343. You can't change this port through the SevOne NMS user interface.
-
Non-sampled flow data - SevOne NMS uses port 9996. You can change this port in SevOne NMS by using in the Cluster Manager > Cluster Settings tab.
Flow Source Flow Timeout Configuration
Manufacturers typically configure routers to send flow data every 30 minutes. This setting is sometimes referred to as the flow cache timeout. It specifies how frequently a router sends the flow table to the collector (SevOne NMS). This, in effect, sets the limit to how much a router allows a flow to grow before breaking it into a new flow.
We recommend that you configure routers to send flow data every minute. This will ensure that the router reports to SevOne NMS in a timely manner, enabling an even distribution of information transfer. If you set the flow source flow timeout configuration to something other than one minute, the router reports less frequently and sends SevOne NMS larger flow tables, resulting in less granular report data. To compensate for this, the SevOne NMS FlowFalcon Reports page provides a Granularity setting. This enables you to view the report at the granularity that matches your router flow timeout configuration. We don't recommend a flow cache timeout of anything other than one minute.
The following table lists use cases along with associated timeout configurations, SevOne FlowFalcon settings, and caveats.
|
Flow Source Flow Timeout Configuration Considerations |
||
|
Applicable Use Cases |
Flow Source Flow Timeout Configuration |
SevOne NMS FlowFalcon Report Settings |
|
Recommended: Billing AND Burst Monitoring |
1 Minute |
Leave the display setting granularity set to the default, Auto. This applies to both the classic FlowFalcon Reports page and the Report Attachment Wizard. This is the optimal SevOne NMS setting for typical flow reporting. |
|
Acceptable |
2-5 Minutes |
Set the display setting granularity to 5 minutes. This applies to both the classic FlowFalcon Reports page and the Report Attachment Wizard. |
|
Not Recommended |
5+ Minutes |
On the classic FlowFalcon Reports page: In the Display Settings section, click the Granularity drop-down and select Custom. Set the granularity time span to twice the router flow timeout. On the Report Attachment Wizard: Go to the Settings page and select the FlowFalcon tab. Click the Granularity drop-down and select 30 minutes . |
Enable Cisco Devices to Send Flow Data
Flexible NetFlow (FNF) - Cisco IOS Router
feature netflowflow exporter SEVONE destination <sevone IP Address> transport udp 9996 source <source interface of netflow export> version 9 template data timeout 600 option sampler-table timeout 600 flow record NetflowExport description Netflow_traffic match ipv4 source address match ipv4 destination address match ip protocol match ip tos match transport source-port match transport destination-port collect routing destination as collect routing forwarding-status collect routing next-hop address ipv4 collect transport tcp flags collect counter bytes collect counter packets collect timestamp sys-uptime first collect timestamp sys-uptime last flow timeout active 60 flow timeout inactive 15flow monitor Monitor_Enterprise description MONITOR_ENTERPRISE record NetflowExport exporter SEVONEPer interface:interface Vlan4 ip flow monitor Monitor_Enterprise input ip flow monitor Monitor_Enterprise outputTraditional NetFlow (TNF) - Cisco IOS Router
-
First, we need to enable Cisco Express Forwarding (CEF), which is required for flow in most recent IOS releases. In global configuration mode, enter the following command to enable CEF.
ip cefGlobal configuration mode is indicated by the host name followed by (config)#. For example, if your router is named Router-2, the command prompt in global configuration mode would be Router-2(config)#.
-
Next, enter the following commands to start the NetFlow Data Export (NDE).
-
Specify your SevOne NMS appliance as the destination (that is, the flow collector) for your router and specify a port. Replace <SevOne-IP> with the IP address of your SevOne NMS appliance.
ip flow-exportdestination <SevOne-IP> 9996SevOne NMS collects flow data on port 9996 by default. To confirm the specified port, look at the FlowFalcon settings. From the navigation bar click Administration > Cluster Manager > Cluster Settings. Then click the FlowFalcon subtab and look at the Incoming Port field.
-
Specify the interface that NetFlow will derive the source IP address from.
ip flow-exportsourceloopback 0 -
Specify the export version format. In the following command, replace <version-number> with the appropriate version (for example, 5 or 9).
ip flow-exportversion <version-number>
-
-
By specifying parameters for the NetFlow accounting flow cache, you can prevent flows from staying in the cache longer than necessary. Perform the following actions to configure the timeout for active and inactive flows.
Note that the active timeout is specified in minutes, while the inactive timeout is specified in seconds.
-
Specify the number of minutes to leave active flows in the cache. Breaking flows into shorter segments prevents sending too many flows to your collector (the SevOne NMS appliance). The following command allows active flows to stay in the cache for 1 minute. In other words, it breaks the flows into one-minute segments.
ip flow-cache timeout active 1 -
Specify the number of seconds to leave inactive flows in the cache. This will cause finished flows to be expired and removed from the cache. The following command allows inactive flows to stay in the cache for 15 seconds.
ip flow-cache timeout inactive 15
-
-
Now you'll need to enable NetFlow on each physical interface that you'd like to collect a flow from. This is normally an Ethernet or WAN interface. You may need to set the speed of the interface in kilobits per second, especially for frame relay or ATM virtual circuits.
You don't need to do this for VLANs or tunnels, because they're automatically included.
-
Specify the interface with the following command. Replace <interface> with the name of the physical interface (for example, Ethernet0/0) that you'd like to enable NetFlow on.
interface <interface> -
Enter one of the following commands to enable the physical interface specified above.
-
To enable flows on individual sub-interfaces rather than all of the sub-interfaces.
ip flow ingress -
To enable flows on the physical interface along with all the sub-interfaces associated with it.
ip route-cache flow
-
-
-
You'll need to save your configuration changes. To do so, enter the following command.
copy run start -
Let's verify that the router is generating flow statistics. First, you'll need to switch to enable mode. Then enter the following commands to view current NetFlow configuration and state.
Enable mode, also known as privileged mode, is indicated by the host name followed by #. For example, if your router is named Router-2, the command prompt in enable mode would be Router-2#.
-
Enter the following command to display the status and statistics of the data export.
show ip flowexport -
Enter the following commands to display summaries of the active flows and the amount of NetFlow data exported from the router.
To display a summary of the data export statistics:
show ip cache flowTo display a detailed summary of the data export statistics:
show ip cache verbose flow
-
-
Enable the the ifIndex SNMP setting. This tells the router to remember ifIndexes so that they don't change during device configuration or reboot.
snmp-server ifIndex persistThis is an important step and is required by SevOne NMS.
Cisco Switches Running CatOS (Hybrid Mode) - Non-4000 Series Catalyst Switches
Router Side
Before enabling flow on this switch, you'll need to enter the following commands on the router side.
First, enter the following global commands.
ip flow-export source <interface>ip flow-export version <version-number>ip flow-export destination <SevOne-IP> 9996ip flow-cache timeout active 1
Now enter the following commands for each physical interface. Replace <interface> with the name of the interface.
interface <interface>ip route-cache flow Switch Side
-
Specify your SevOne NMS appliance as the destination (that is, the flow collector) for your switch and specify a port. Replace <SevOne-IP> with the IP address of your SevOne NMS appliance.
setmls nde <SevOne-IP> 9996 -
Specify the export version. In the following command, version 9 is specified.
setmls nde version 9 -
Perform the following actions to specify how long active and inactive flows stay in the cache.
-
Specify the number of seconds to leave active flows in the cache. The following command allows active flows to stay in the cache for roughly two minutes. In other words, it breaks the flows into ~two-minute segments.
setmls agingtime long 128 -
Specify the number of seconds to leave inactive flows in the cache. The following command allows active flows to stay in the cache for roughly one minute.
setmls agingtime 64
-
-
Enter the following command to set the flow mask to full flows.
setmls flow full -
You'll need CatOS 7.(2) or higher for this step. If you're working with a lower version, jump ahead to the next step. Enter the following command to enable NetFlow Data Export (NDE) for all traffic within the specified VLANs rather than just inter-VLAN traffic.
setmls bridged-flow-statisticsenable -
Enter the following command to enable NDE.
setmls ndeenable
Switches Running IOS (Native Mode)
First, make sure that you're in privileged/enable mode. Enter the following global commands (all commands are entered in the router <enable> config option).
-
Specify the interface that NetFlow will derive the source IP address from.
ip flow-exportsource<interface> -
Specify the export version format.
ip flow-exportversion 9 -
Specify your SevOne NMS appliance as the destination (that is, the flow collector) for your switch and specify a port. Replace <SevOne-IP> with the IP address of your SevOne NMS appliance.
ip flow-exportdestination <SevOne-IP> 9996 -
Enable NDE from the PFC and configure the NDE version.
mls nde sender version 9 -
Perform the following actions to specify how long active and inactive flows stay in the cache.
-
Specify the number of seconds to leave active flows in the cache. The following command allows active flows to stay in the cache for one minute. In other words, it breaks the flows into one-minute segments.
setmls agingtime long 60 -
Specify the number of seconds to leave inactive flows in the cache. The following command allows active flows to stay in the cache for fifteen seconds.
setmls agingtime 15
-
-
If you have a Supervisor Engine 2 or 720 with IOS version 12.1.13(E) or higher, you'll need to enter the following two commands to put interface and routing information into the NetFlow exports.
mls flow ip interface-fullmls nde interface -
Enter the following commands for each physical interface. Replace <interface> with the name of the interface.
interface <interface>ip route-cache flow
4000 Series Catalyst Switches Running in Hybrid or Native Mode
This series requires a Supervisor Engine IV with a NetFlow Services daughter card to support NDE.
-
In the configuration terminal on the router, enter the following commands to start NetFlow export. Replace <SevOne-IP> with the IP address of your SevOne NMS appliance.
ip flow-exportversion 9ip flow-exportdestination <SevOne-IP> 9996 -
Enter the following commands to enable NetFlow on each physical interface. Replace <interface> with the name of the interface.
interface <interface>ip route-cache flow infer-fields
Enable Juniper Devices to Send Flow Data
Juniper supports flow exports by sampling packet headers with the routing engine and aggregating them into flows. Packet sampling is achieved by defining a firewall filter to accept and sample all traffic, applying that rule to an interface, and then configuring the sampling forwarding option.
To configure inline flow monitoring, include the inline-jflow statement at the [edit forwarding-options sampling instance instance-name family inet output] hierarchy level.
Inline sampling supports the version-ipfix format, which uses UDP as the transport protocol. To configure inline sampling, include the version-ipfix statement at the [edit forwarding-options sampling instance instance-name family inet output flow-server address] hierarchy level.
The following operational commands include inline fpc keywords to display inline configuration information.
-
show services accounting errors
-
show services accounting flow
-
show services accounting status
The Juniper Web Site lists all features that were added to JUNOS Release 10.2.
Configure sFlow Features from the CLI
-
Specify the IP address of the collector. Replace <SevOne-IP> with the IP address of your SevOne NMS appliance.
[edit protocols sflow]
user@switch# set collector <SevOne-IP> -
Specify the UDP port for the collector. The default UDP port on the SevOne NMS appliance is 6343.
[edit protocols sflow]
user@switch# set collector udp-port 6343 -
Enable sFlow technology on a specific interface. Replace <interface-name> with the name of an interface (for example, ge-0/0/3) that you'd like to enable sFlow on.
[edit protocols sflow]
user@switch# set interfaces <interface-name>You can't enable sFlow technology on a Layer 3 VLAN-tagged interface. You can't enable sFlow on a LAG interface either, but it can be enabled on the member interfaces of the LAG.
-
Specify how frequently the sFlow agent polls the interface. Replace <seconds> with the number of seconds. If you don't want to poll the interface, specify 0 here.
You have the option of configuring this setting (polling interval) and the next setting (sample rate) at the interface level. If you prefer to do so, jump ahead two steps.
[edit protocols sflow]
user@switch# set polling-interval <seconds> -
Specify the rate at which you want to sample packets. Replace <number> with your desired sample rate. For example, if you specify 6 here, one out of every six packets will be sampled.
[edit protocols sflow]
user@switch# set sample-rate <number> -
This step is optional. If you prefer, you can set the polling interval and sample rate at the interface level. To do this, use the following command, replacing <interface-name> with the name of the interface, <seconds> with the polling interval in seconds, and <number> with the sample rate number.
[edit protocols sflow intefaces]
user@switch# set interfaces <interface-name> polling-interval <seconds>The interface-level configuration overrides the global configuration for the interface.
Enable Alcatel Devices to Send Flow Data
When you enable cflowd on an Alcatel service interface, cflowd collects routed traffic flow samples through a router for analysis. Cflowd is supported on Internet Enhanced Service (IES) and Virtual Private Routed Networks (VPRN) service interfaces. Layer 2 traffic is excluded. All packets forwarded by the interface are analyzed according to the cflowd configuration. At the interface level, cflowd can be associated with a filter (ACL) or an IP interface.
When you enable cflowd on an interface, all packets forwarded by the interface are subject to analysis according to the global cflowd configuration.
When you configure the cflowd interface option in the config>router>interface context, the following requirements must be met to enable traffic sampling on the specific interface.
-
Enable cflowd.
-
Select the interface>cflowd interface option.
-
To omit certain types of traffic from being sampled when the interface sampling is enabled, enable the config>filter>ip-filter>entry>interface-disable-sample option via an ip-filter or ipv6-filter. You'll need to apply the filter to the service or network interface that the traffic to be omitted is on.
Specify Cflowd Options on an IP Interface
The following is the CLI syntax for configuring cflowd on an interface.
config>router>if# cflowd {acl | interface} no cflowdDepending on the option you select, either acl or interface, cflowd extracts traffic flow samples from an IP filter or an interface for analysis. All packets forwarded by the interface are analyzed according to the cflowd configuration.
Select the acl option to enable traffic sampling on an IP filter. You'll need to enable cflowd (filter-sample) in at least one IP filter entry.
Select the interface option to enable traffic sampling on an interface. If cflowd isn't enabled (no cflowd), then traffic sampling won't occur on the interface.
Enable Cflowd on Service Interfaces
The following is the CLI Syntax for enabling cflowd on service interfaces.
config>service>vpls <service-id#> interface <ip-int-name> cflowd {acl | interface}Configure Cflowd for Collectors
The following is the CLI syntax for configuring cflowd.
config>cflowd# collector <SevOne-IP>:<port> version <version-number> aggregation as-matrix destination-prefix protocol-port raw source-destination-prefix source-prefix autonomous-system-type {origin | peer} description description-string no shutdown template-set {basic | mpls-ip}The following is an example of a basic cflowd configuration .
The example below includes the use-vrtr-if-index command. You can use this command to export flow data using interface indexes (ifIndex) instead of using the Alcatel internal global IF index IDs.
active-timeout 20 inactive-timeout 10 overflow 10 rate 100 use-vrtr-if-index collector 10.2.10.31:9996 version 8 aggregation as-matrix raw exit description "SevOne NMS" exit collector 10.2.10.32:9996 version 8 aggregation protocol-port source-destination-prefix exit autonomous-system-type peer description "Neighbor collector" exitEnable Citrix NetScaler AppFlow
As of SevOne NMS version 5.6, SevOne now supports Citrix NetScaler AppFlow.
Perform the following steps to configure AppFlow.
-
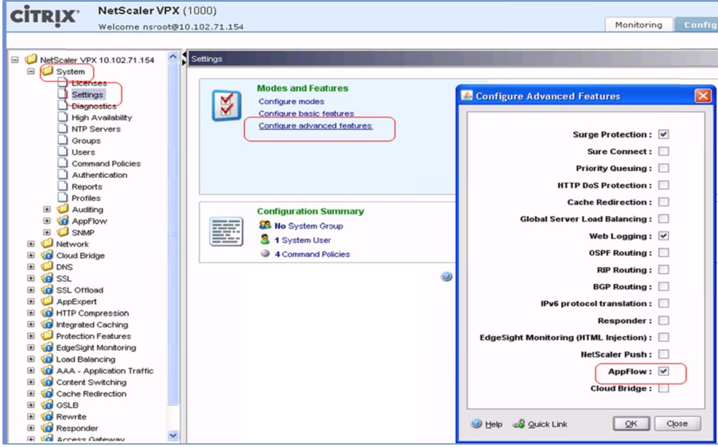
Go to your your Citrix NetScaler configuration UI.
-
From the menu on the left, select System -> Settings.
-
To the right, under Settings, click Configure advanced features.
-
In the Configure advanced features pop-up, select the AppFlow check box.
-
Click OK.
-
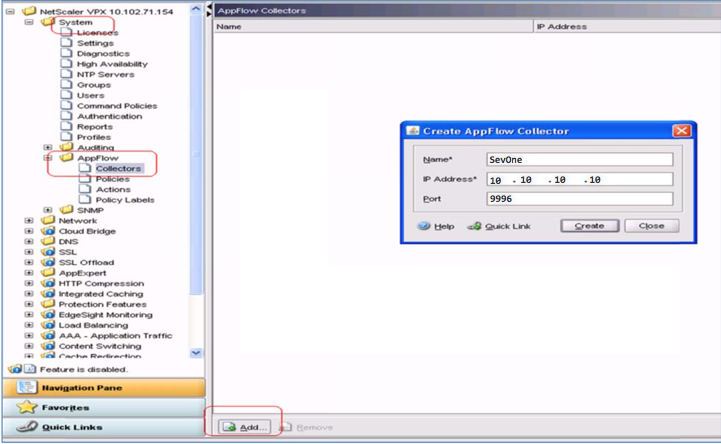
From the menu on the left, under System, expand the AppFlow folder. Under AppFlow, select Collectors.
-
At the bottom of the page, click Add....
-
In the Create AppFlow Collector pop-up, provide the specified input for the following fields:
-
Name - enter SevOne.
-
IP Address - enter the IP address of your SevOne Dedicated NetFlow Collector (DNC).
-
Port - enter 9996.
-
-
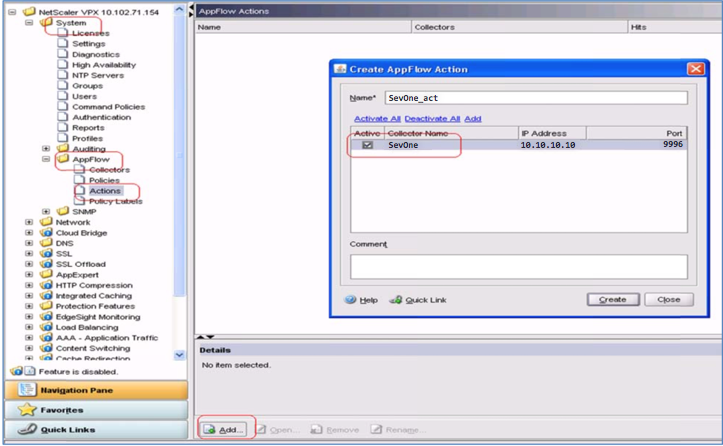
From the menu on the left, under System, expand the AppFlow folder if it's not already expanded. Under AppFlow, select Actions.
An AppFlow action is a set of collectors, that the flow records are sent to if the associated AppFlow policy matches.
-
At the bottom of the page, click Add....
-
In the Create AppFlow Action pop-up, select SevOne (under Collector Name).
-
To the left of the SevOne, under Active, select the check box.
-
Click Create.
-
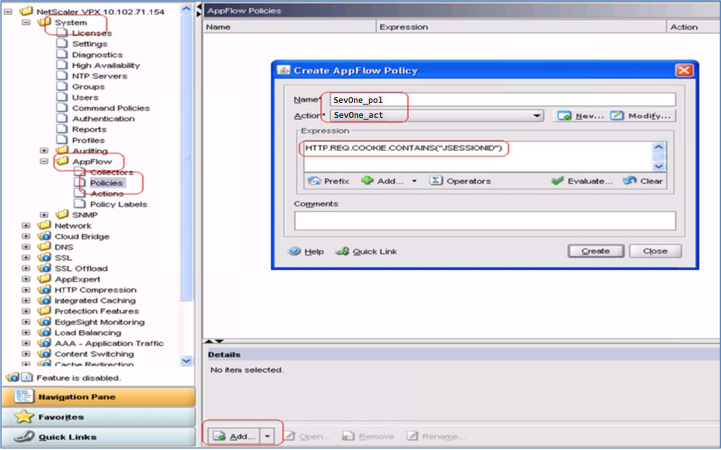
From the menu on the left, under System -> AppFlow, select Policies.
After you configure an AppFlow action, you'll need to configure an AppFlow policy. An AppFlow policy is based on a rule that consists of one or more expressions. For more information about expressions, refer to your Citrix AppFlow Configuration Guide.
-
At the bottom of the page, click Add....
-
In the Create AppFlow Policy pop-up, perform the following actions:
-
In the Name field, provide a name.
-
Click the Action drop-down to select an action.
-
In the Expression field, enter an expression.
-
Click Create.
-
-
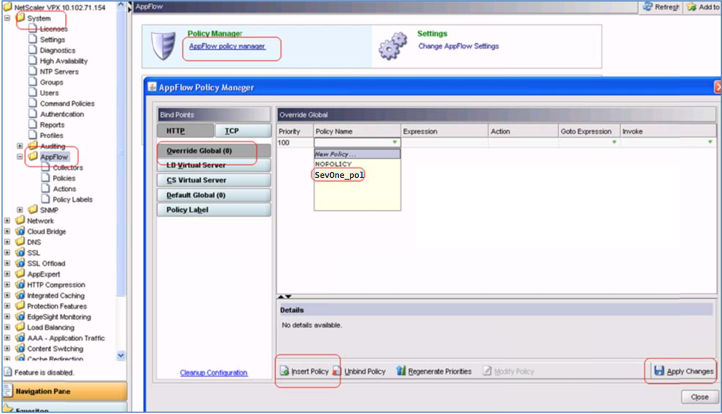
Once you have created your policy, you'll need to put the policy into effect. To do this, you will need to perform one of the following actions:
Policies can be bound to override global/LB vserver/CS vserver/default global.
-
Bind the policy globally so that it applies to all traffic that flows through the NetScaler.
-
Bind the policy to a specific virtual server so that it applies only to traffic related to that virtual server.
-
-
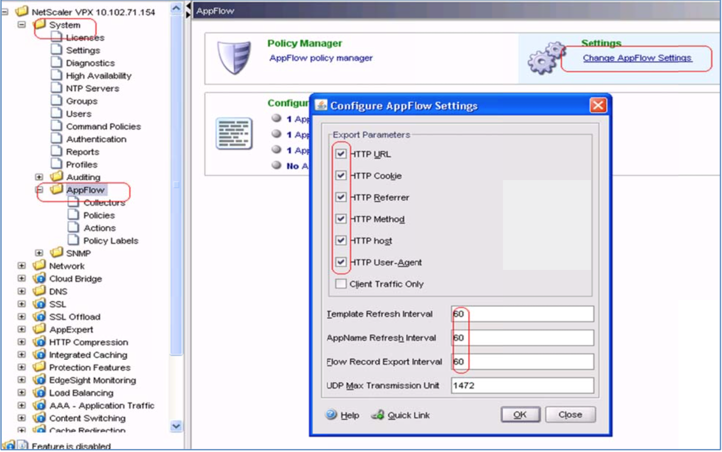
Now you'll need to configure your AppFlow settings to customize the information that's sent to the collector. From the menu on the left, under System, select AppFlow.
-
On the right side of the page, under Settings, click Change AppFlowSettings.
-
In the Configure AppFlow Settings pop-up, specify the necessary settings to customize the information that will be sent to the collector.
-
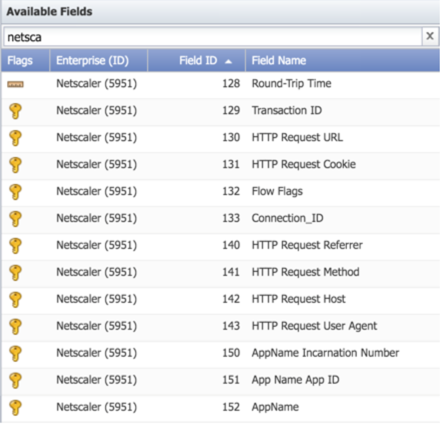
The following NetScaler unique fields are available in reports, along with Bandwidth and Packets metrics. During configuration in SevOne NMS, you'll need to provide the field names by using the FlowFalcon View Editor, described later in this guide.
-
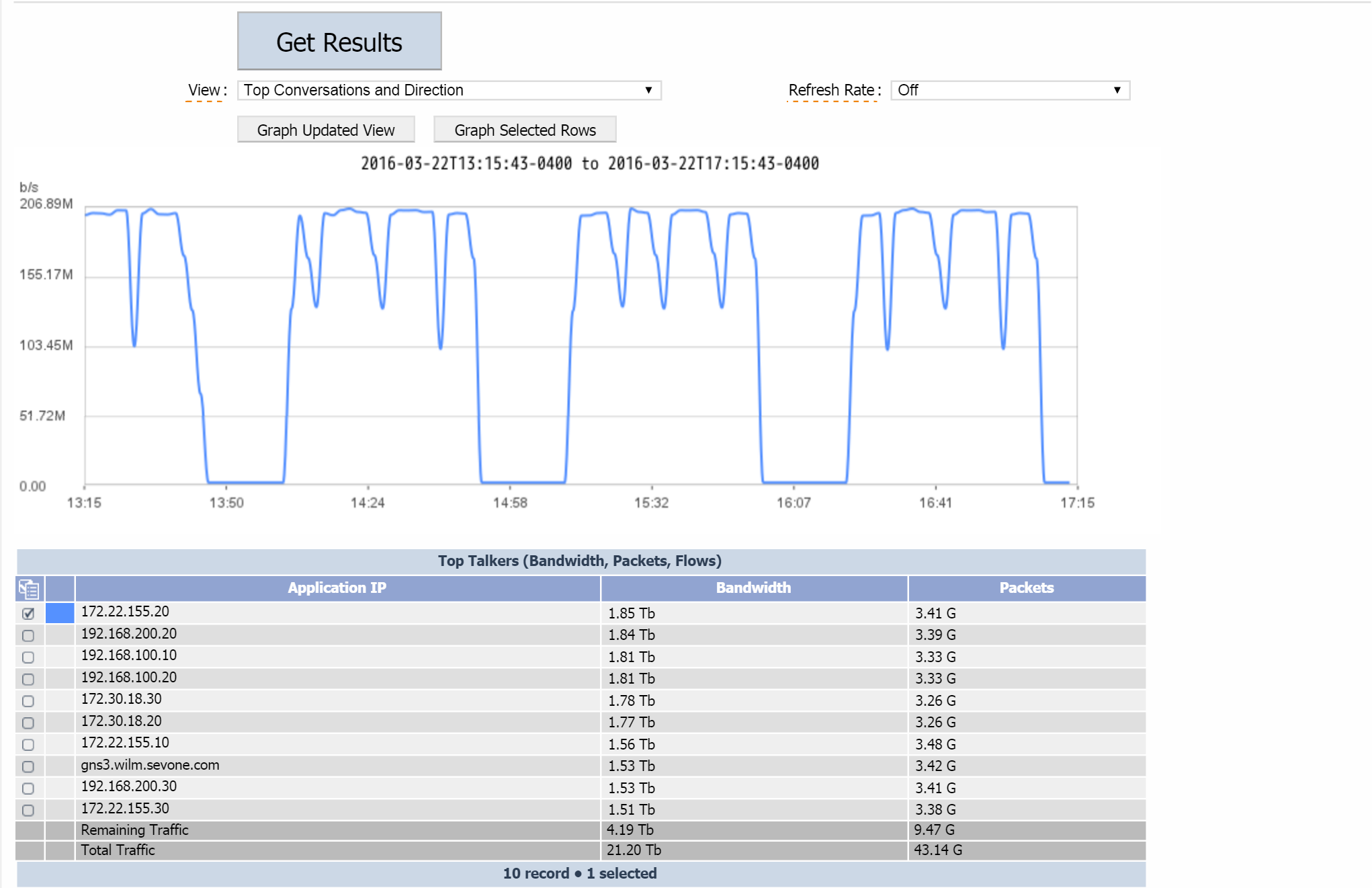
Once you've set up AppFlow and configured settings in SevOne NMS, you'll be able to create report views and generate reports on your AppFlow data, for example:
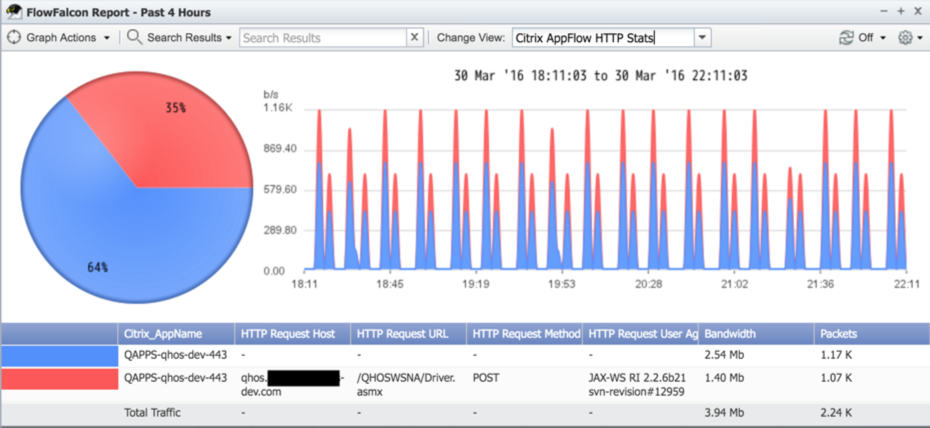
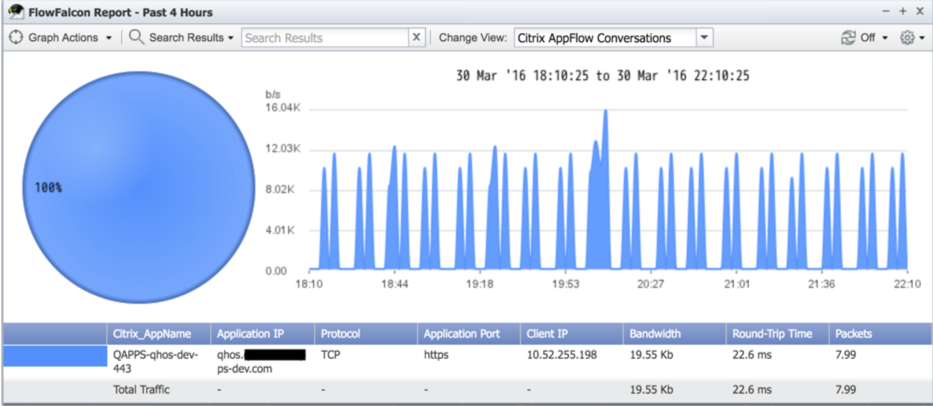
Configuration Steps
In this section, we'll cover the following topics:
-
Configuring flow settings at the cluster level and the peer level
-
Defining rules for processing flow data received by SevOne NMS
-
Managing FlowFalcon report views
-
Uploading MPLS flow maps
-
Defining network segments for grouping flow data
-
Mapping object indicators to flow interfaces
-
Defining protocols and services to collect flow data from
FlowFalcon Cluster-level and Peer-level Settings
The Cluster Manager displays statistics and lets you define settings at the cluster level, peer level, and appliance level. With a few exceptions, the default Cluster Manager settings enable you to run SevOne NMS right out of the box.
To access the Cluster Manager from the navigation bar, click Administration and select Cluster Manager.
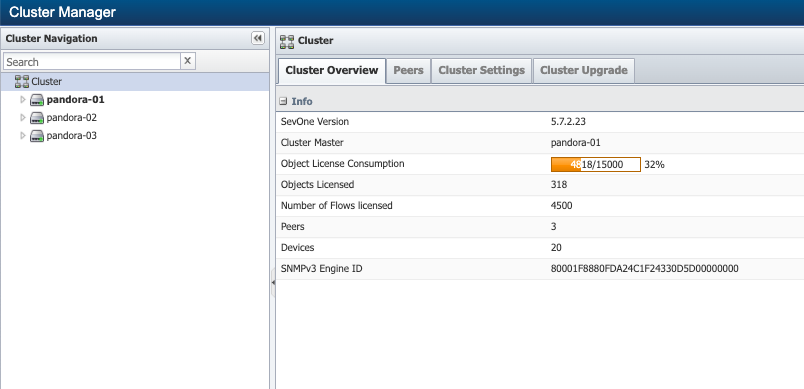
About Cluster-level Flow Settings
In this section, we'll look at the Cluster Manager > Cluster Settings tab > FlowFalcon subtab, where you define how to collect and process raw flow data and aggregated flow data.
Drop Long Flows Option
The settings below include a Drop Long Flows option, which enables you to define a time limit for what you consider to be a long flow. When you use the Drop Long Flows option, SevOne NMS hides traffic from routers that send flows exceeding the specified Max Flow Duration. When flows exceed the Max Flow Duration, an administrative message appears at logon informing administrators that flows from a specific router have been dropped. The Drop Long Flows feature is useful when you set the router cache timeout to be shorter than the Max Flow Duration, because long flows would indicate that a router is misconfigured.
Write Interval Option
You'll also see a Write Interval option, which lets you adjust the interval at which SevOne NMS writes flow data to the database. The Write Interval sets the time window for aggregating raw data into the minimal aggregation. This should be set to 1 minute. In the rare case that you decide to change this setting, keep in mind that every hour SevOne NMS takes flow data and creates 15 minute aggregations for the top <n> flows for each interface and view. This means that you'll want your Write Interval setting to be evenly divisible by 15 when you plan to use aggregated flow data.
Configure Cluster-level Flow Settings
Perform the following steps to configure cluster-level flow settings.
Changes to the settings marked with an asterisk (*) can cause data loss. If you're unfamiliar with the consequences, please contact SevOne Support.
-
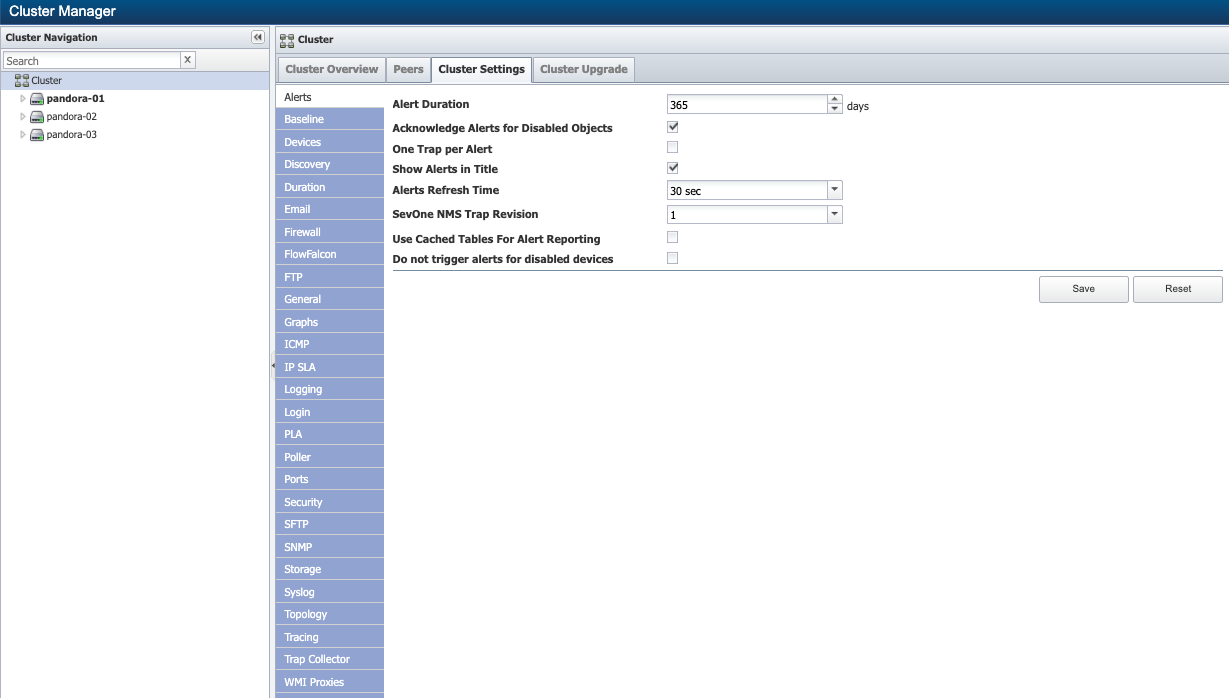
On the right side of the page, select the Cluster Settings tab.
-
On the Cluster Settings tab, click the FlowFalcon subtab.
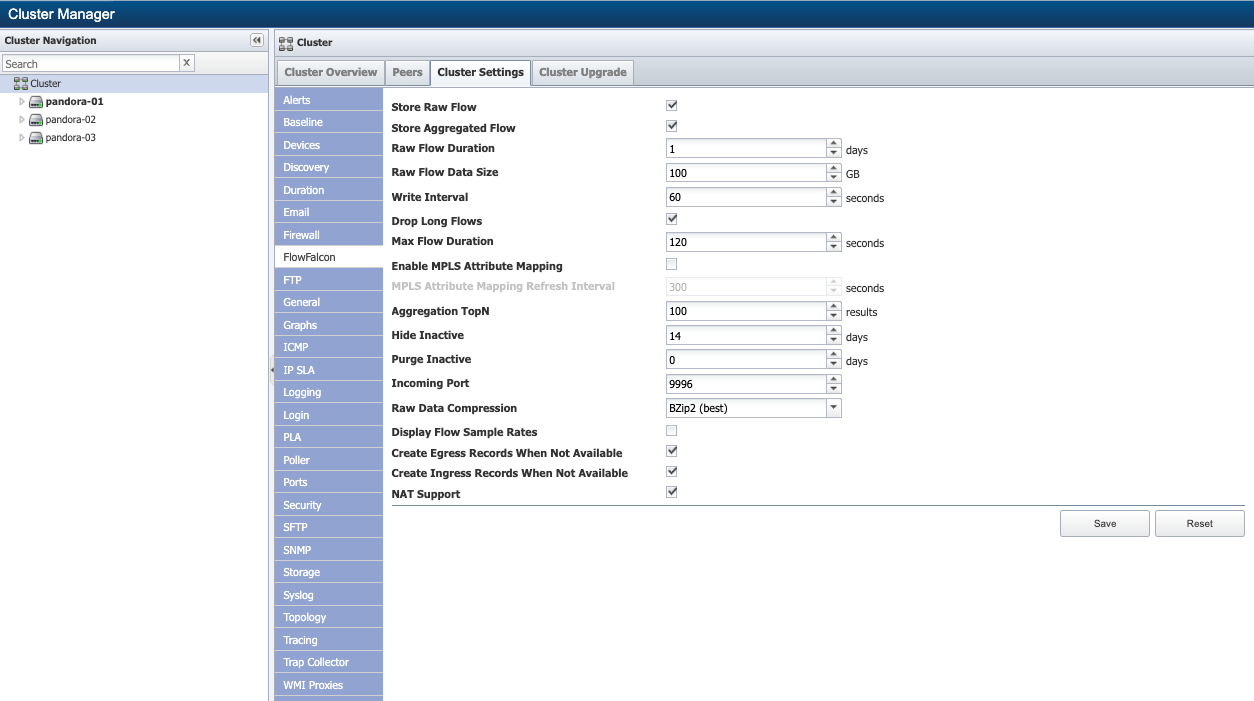
-
* Select the Store Raw Flow check box to collect and store raw flow data. Most FlowFalcon views use raw data. This provides more specificity in the result set but with the trade-off of longer report execution times and less historical data.
-
* Select the Store Aggregated Flow check box to collect and store the most relevant flow data in an aggregated format. FlowFalcon views use this format for faster report execution times.
-
* In the Raw Flow Duration field, enter the number of days to keep raw flow data. Keep in mind that gigabytes of flow data can accumulate quickly.
-
* In the Raw Flow Data Size field, enter the maximum amount of disk space to allocate for raw flow data.
-
* In the Write Interval field, enter the number of seconds to collect flow data before creating a flat file and writing the data to the disk. We recommend 60 seconds. A longer write interval results in fewer–but larger–flat files for raw data and smaller tables for aggregated data. See the example below.
-
Select the Drop Long Flows check box. Then, in the Max Flow Duration field, enter the maximum number of seconds to consider flow data "long".
This drops flows when their duration exceeds the write interval. Long flows are usually due to improper router configuration. This setting triggers an administrative message that appears upon logon to inform you to review the router configuration. Suggested Max Flow Duration is ~2x the Write Interval (from the previous step).
-
Select the Enable MPLS Attribute Mapping check box. Then, in the MPLS Attribute Mapping Refresh Interval field, enter the number of seconds indicating how frequently to read the map files and to refresh the mapping. This enables you to map v9 NetFlow template data from core "P" routers for reports that use the following fields in FlowFalcon views listed below.
This step is necessary for mapping MPLS flow files, which we'll discuss in the MPLS Flow Mapping section.
-
* In the Aggregation TopN field, enter the number of results (50-1000) to store for each aggregation per write interval. The default value is 100. The value you specify represents the maximum number of individual results that an aggregated FlowFalcon view can display. Keep in mind that this consumes disk space.
Warning: Setting a value greater than the default may result in data loss.
-
In the Hide Inactive field, enter the number of days to display data for an inactive device or interface. The default is 14 days. Once the specified amount of time has passed, the device or interface is considered inactive and its information is hidden. An inactive device or interface is one that doesn't send data to SevOne NMS.
-
In the Purge Inactive field, enter the number of days to store data for an inactive device or interface. Enter 0 (zero) to never purge data.
-
In the Incoming Port field, enter the port number for SevOne NMS to use to listen for flow traffic. The default port is 9996.
-
Click the Raw Data Compression drop-down and select a method for compressing raw data files. Greater compression requires less storage but results in higher CPU usage.
-
Select the Display Flow Sample Rates check box to display the sampled flow rate on FlowFalcon reports that contain split interfaces and to display an additional column on the Flow Interface Manager for sampled data. FlowFalcon reports with sampled data display a message. Interfaces that aren't sampled use a sample rate of 1X.
-
Select the Create Egress Records When Not Available check box to automatically create egress records for ingress interfaces that aren't receiving egress records.
-
Select the Create Ingress Records When Not Available check box to automatically create ingress records for egress interfaces that aren't receiving ingress records.
-
Select the NAT Support check box to enable support for routers behind network address translation (NAT).
-
Click Save.
This example uses flows that come from a single device/interface/direction to compare raw and aggregated data at both ends of the settings spectrum (60 to 300 seconds) when flows are received at a rate of 100 flows/minute and each flow is 50 bytes.
Raw
All flows collected during each write interval are written to the disk in a single file. A longer write interval results in larger file sizes, but fewer files (since they're written less often).
For a flow rate of 100 flows/minute at 50 bytes each over a 10 minute time frame:
-
60 second write interval: 10 files are written, one file per minute. Each file contains 100 flows resulting in 5000 bytes per file. (10 x 5 KB files = More smaller files.)
-
300 second write interval: 2 files are written, one file every 5 minutes. Each file contains 500 flows resulting in 25,000 bytes per file. (2 x 25 KB files = Fewer larger files.)
Both approaches result in the same amount of disk usage (in this case, 50 KB).
Aggregated
At the end of each write interval, SevOne NMS calculates a top <n> (100 by default but configurable) per aggregated view (according to the Aggregation TopN setting) and writes those 100 records to the database.
Using a 10 minute time span:
-
60 second write interval: Writes 100 records every minute and adds a total of 1000 records to the database.
-
300 second write interval: Writes 100 records every 5 minutes and adds a total of 200 records to the database.
A larger write interval means fewer entries to the database. This is why a longer time period results in smaller tables.
For every write interval (in this case, 60 seconds), SevOne NMS determines the Top <n> for every device, interface, direction, and view combination. For example, Router 1, Eth0/0, Incoming would have a top 100 for every view (Top Talkers, Top Conversations, etc.). Then SevOne NMS determines a top 100 for Router 1, Eth0/0, Outgoing for every view. This process continues for each interface on every device.
All flows that don't make it into the top 100 are aggregated together into a single record called Remaining Traffic. This happens for every device, interface, direction, and view combination. Total Traffic is the Top <n> plus remaining traffic to represent all traffic in the network.
Configure Peer-level Flow Settings
The Peer Settings FlowFalcon subtab enables you to define the retention of aggregated flow data on the peer for use in FlowFalcon reports. The following diagram provides an explanation of Aggregated Flow Data Retention.
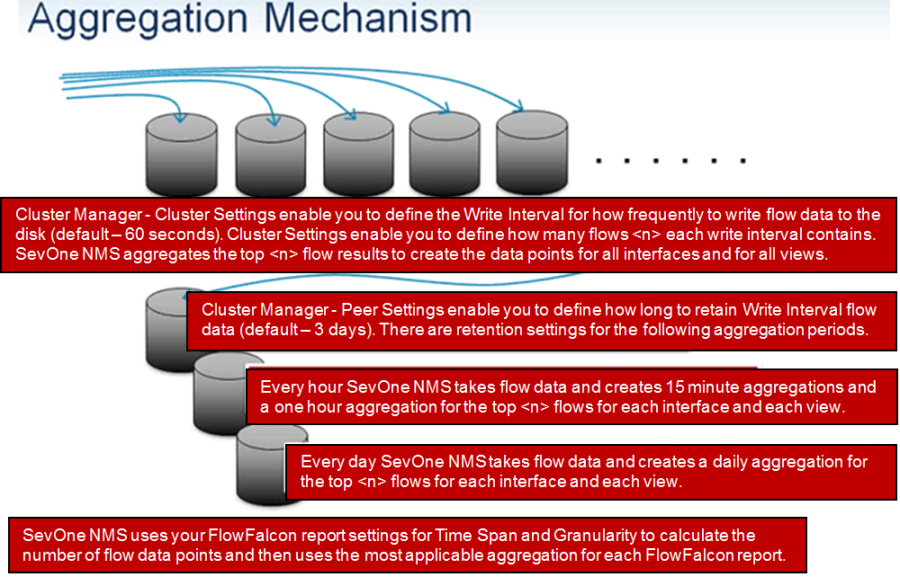
Perform the following steps to configure peer-level flow settings.
Changes to these settings can cause data loss. If you're unfamiliar with the consequences, please contact SevOne Support.
-
In the hierarchy on the left side of the Cluster Manager, select a peer.
-
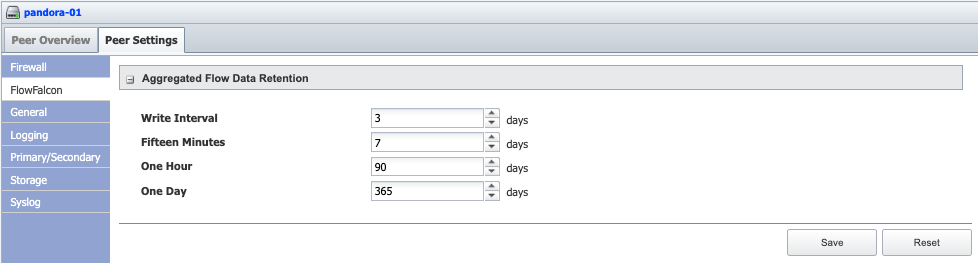
Click the Peer Settings tab. The FlowFalcon subtab is selected by default.
-
In the Write Interval field, enter the number of days to store <write interval> aggregated flow data for calculations. You define the write interval on the Cluster Manager > Cluster Settings > FlowFalcon subtab, which we discussed above.
-
In the Fifteen Minutes field, enter the number of days’ worth of fifteen minute aggregation data to store for calculations.
-
In the One Hour field, enter the number of days’ worth of one hour aggregation data to store for calculations.
-
In the One Day field, enter the number of days’ worth of one day aggregation data to store for calculations.
-
Click Save.
Flow Rules
The Flow Rules page lets you define global rules to not process the flow data SevOne NMS receives. SevOne NMS evaluates the rules you define and applies the rule that is most specific to each source. When you enable devices to send flow data to SevOne NMS, SevOne NMS allows and processes all flow data by default. However, networks have the potential to send large amounts of flow traffic. Using the Flow Rules page, you can define global rules to deny the processing of flows. If you want to override the rules you define here for specific interfaces, you can do so from the Flow Interface Manager.
Add or Edit Flow Rules
Perform the following steps to add (or edit) flow rules.
-
From the navigation bar, click Administration and select Flow Configuration, then Flow Rules.
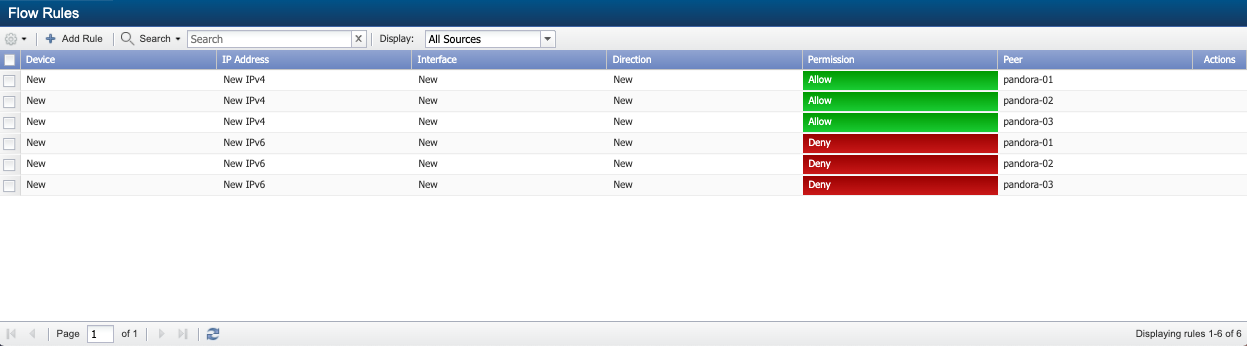
-
Click Add Rule to display the Add New Flow Rule pop-up. If you'd like to edit an existing rule, select the rule and click
 under Actions.
under Actions. 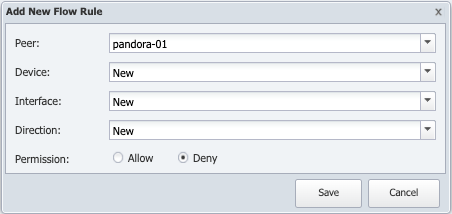
-
Click the Peer drop-down and select the peer that you want the device to send flow data to.
-
Click the Device drop-down and select the device whose flows you want to define a rule for. If you select Specify..., an IP Address field will appear. Enter the IP address here.
-
Click the Interface drop-down and select the interface that you want to apply the rule to. If you select Specify..., an Interface Number field will appear. Enter the interface number here.
-
Click the Direction drop-down and select one of the following:
-
New - to apply the rule to any applicable new flow, incoming or outgoing.
-
Incoming - to apply the rule to data that comes into the device. Older versions of NetFlow are ingress only, meaning they can report on data coming in to the interface but not on data going out from the interface.
-
Outgoing - to apply the rule to data that goes out from the interface. For older versions of NetFlow, SevOne NMS uses data from other flows to create an estimation of outgoing flows.
-
-
For Permission select one of the following options:
-
Allow - to process the flow data across the interface.
-
Deny - to not process the flow data across the interface.
-
-
Click Save.
When the rule specifies both a device and an interface, a green bar appears at the top of the page to indicate that the rule is specific enough to be a Flow Interface Manager rule, and the rule appears on the Flow Interface Manager (rather than the Flow Rules page).
Manage Flow Rules
Perform the following steps to manage existing flow rules.
-
Select the check box for the flow rule that you want to manage. You can select more than one at a time.
-
Click
 and select one of the following options.
and select one of the following options. -
Allow Selected Flows - to process the flow data across the interface.
-
Deny Selected Flows - to not process the flow data across the interface.
-
Delete Selected Rules - to delete the rules you select.
-
Flow Interface Manager
The Flow Interface Manager lets you limit the flow data that SevOne NMS processes from specific devices and specific interfaces. As we mentioned in the previous section, enabling devices to send flow data to SevOne NMS means that SevOne NMS will allow and process all flow data by default. These devices have the potential to send large amounts of flow traffic. The rules you define here override the global rules you define on the Flow Rules page.
To access the Flow Interface Manager from the navigation bar, click the Administration menu, select Flow Configuration, and then select Flow Interface Manager.
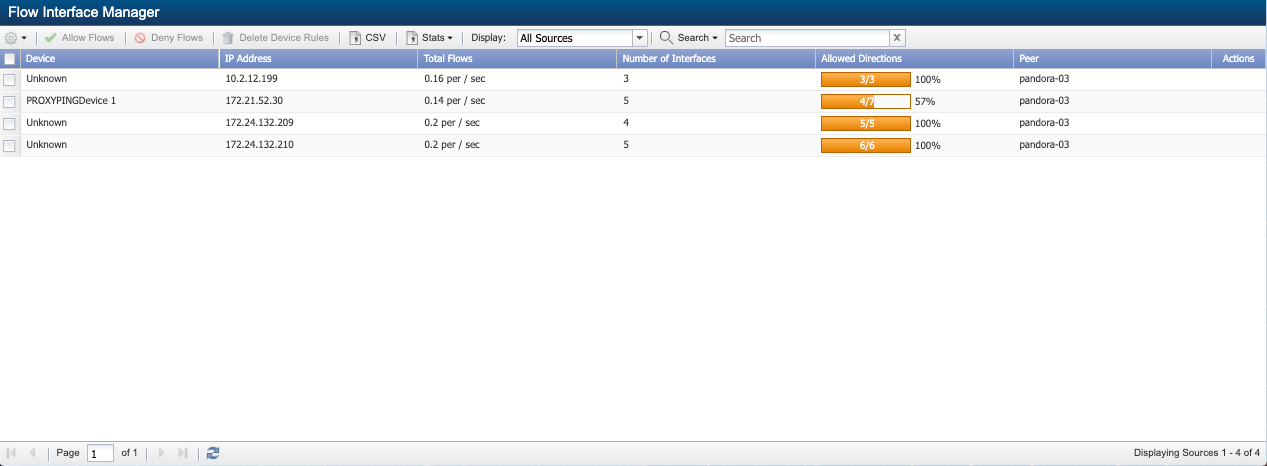
The list displays the following information for all devices from which SevOne NMS can receive flow data. Click the Display drop-down to display rules for All Sources, Allowed Sources, or Denied Sources.
-
Device – Displays the name of the device when SNMP resolvable. Displays Unknown if you do not enable the SNMP plugin for the device.
-
IP Address – Displays the IP address of the device.
-
Total Flows - Displays the number of flows processed per second across all interfaces on the device over the past minute. Malformed flows and flows denied by a rule are not processed. The flow rate on the Flow Interface Manager is calculated after duplication.
The Flow Interface Manager displays the rate of flows over the past minute for each interface and direction after SevOne NMS duplicates flows that lack directional information. Since NetFlow v5 only exports information about the incoming interface, SevOne NMS duplicates the flow statistics for v5 NetFlow to factor for outgoing flows on devices that use v5 NetFlow. Therefore, if your network only uses v5 NetFlow, you can expect the flow rate to be double the actual rate of flows that arrive. The flow rate on the Flow Interface Manager is therefore different from the flow rates that display in FlowFalcon reports and on the Cluster Manager, Peer Overview tab which use different calculations.
-
Number of Interfaces – Displays the number of interfaces on the device from which flow data is received.
-
Allowed Direction - Displays the number of interfaces from which flow data is processed and the number of directions of flow data received. Each interface can have incoming flow and outgoing flow and you can define rules to deny flow by direction.
-
Sample Rate - Displays the flow data sample rate when the interface sends sampled flow data. This column is only available when you select the Display Flow Sample Rates check box on the Cluster Manager > Cluster Settings tab > FlowFalcon subtab.
-
n/a – Flow data has yet to be received from the interfaces.
-
1x - Sample rate is 1-to-1 (data is not sampled).
-
<n>x – The sample rate (e.g., if 1 packet out of 100 packets is received, this column displays 100x).
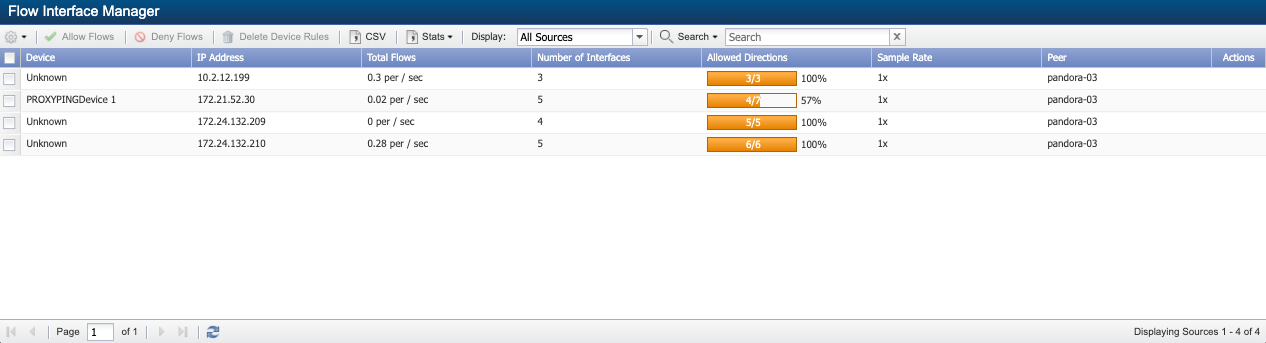
Some flow devices only record data for a selection of messages that the device encounters based on a sample flow rate. The device notifies monitoring systems about only a fraction of its total traffic. The sample rate enables SevOne NMS to scale the data to compensate for the lack of notification of sampled data. The Sample Rate column is only available when you select the Display Flow Sample Rates check box on the Cluster Manager > Cluster Settings tab > FlowFalcon subtab.
-
-
Peer - Displays the name of the peer that receives the flow data.
Manage Device Level Flows
-
Select one or more devices and the following highlighted controls are available from the navigation bar and
 drop-down to manage the selected device(s) and its associated flow data.
drop-down to manage the selected device(s) and its associated flow data. 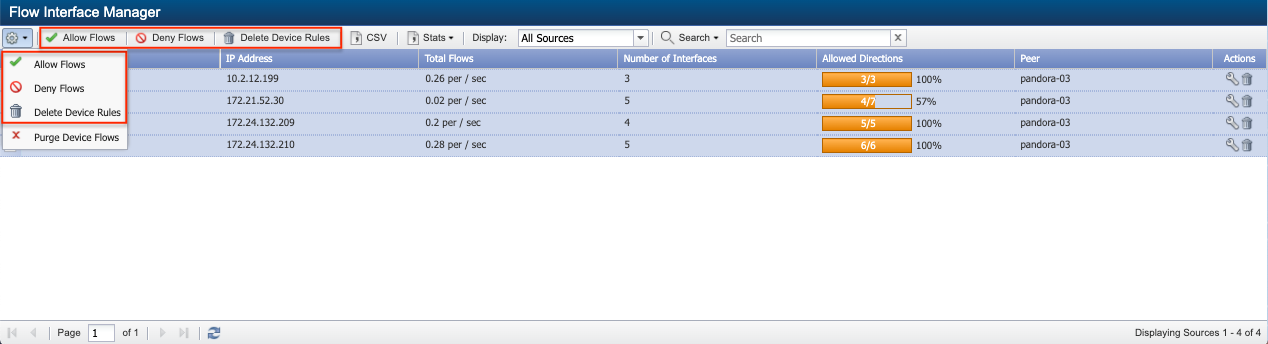
-
Allow Flows - to process the flow data across all interfaces on the selected devices.
-
Deny Flows - to not process the flow data for the selected devices.
-
DeleteDevice Rules to delete the selected flow device(s) and its associated flow data.
-
-
CSV - to create a .csv report on all devices with flow. This includes such details as peer name, flows per second, maximum sample rate, interface, etc.
-
Stats - click the drop-down and select Selected Devices to view statistics for selected devices or All devices to view statistics for all devices. This creates a .csv file with information such as number of accepted flows, number of dropped flows by duration, total number of dropped flows, etc.
-
Display - click the drop-down to display rules for All Sources, Allowed Sources, or Denied Sources.
-
Click
 and select Purge Device Flows to delete the flow data processed for the devices.
and select Purge Device Flows to delete the flow data processed for the devices.
Delete Device Level Flow
-
Select a device from the list or hover in the Actions column on a row for the device and its associated flow data you wish to delete. Click on
 to delete the flow device and its associated flow data.
to delete the flow device and its associated flow data. 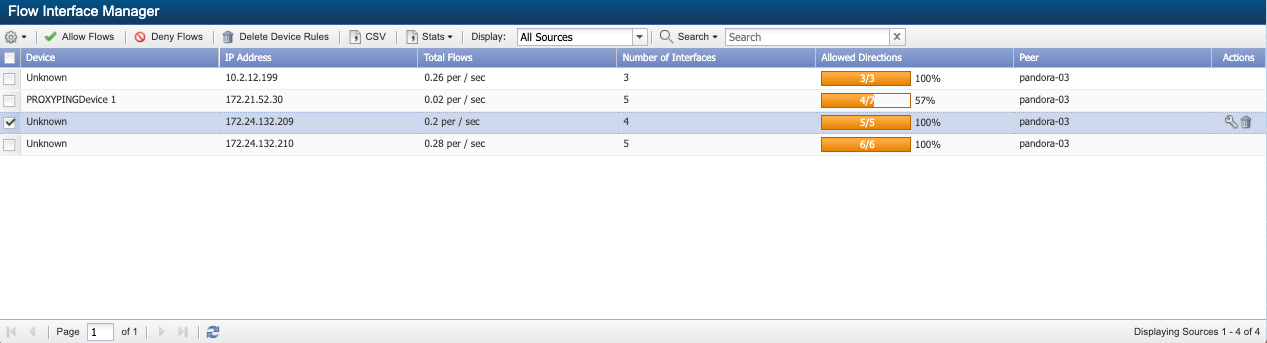
-
Click on OK in the warning message pop-up if you are sure you want to delete the selected flow device. Click on Cancel or x to cancel the operation.
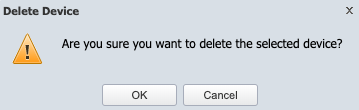
This allows deletion of only one selected flow device at a time.
Manage Interface Level Flow
-
Select a device from the list or hover in the Actions column on a row for the device whose interface you want to manage. Click on
 to manage the selected device's interface.
to manage the selected device's interface. 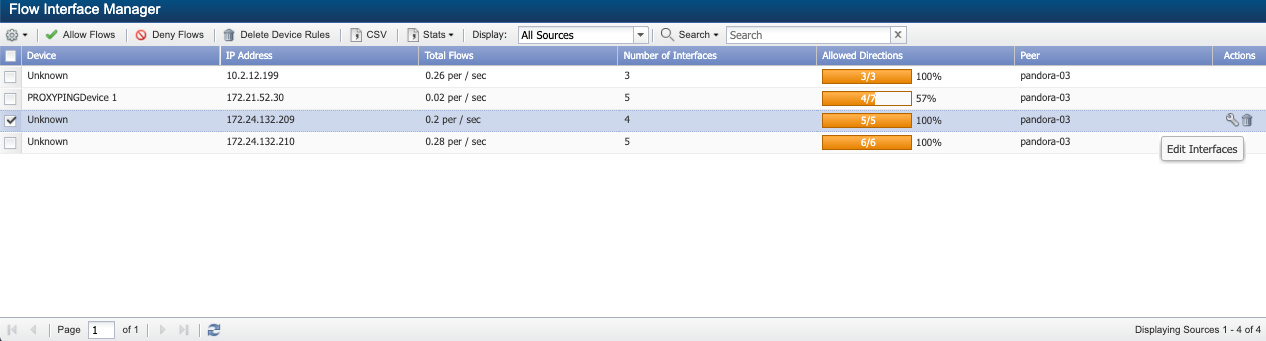
-
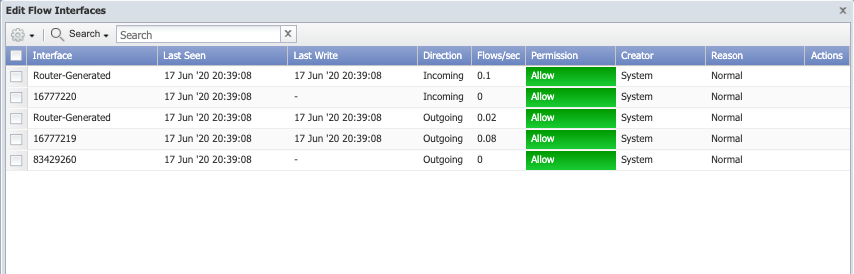
The Edit Flow Interfaces pop-up enables you to manage flow rules at the interface level.
-
The list displays the following information for each individual interface on the selected device.
-
Interface - Displays the interface number the device sends to SevOne NMS.
-
Last Seen - Displays the last time flow data passed through the interface.
-
Last Write - Displays the last time flow data from this interface was written to the database. This is either the last time flow data was received for the interface or the last time SevOne NMS wrote flow data to the database based on the Write Interval you define on the Cluster Manager > Cluster Settings tab > FlowFalcon subtab.
-
Direction - Displays Incoming for incoming flow data or displays Outgoing for outgoing flow data.
-
Flows/Sec - Displays the number of flows processed per second across the interface over the past minute.
-
Sample Rate - Displays the flow data sample rate when the interface sends sampled flow data.
-
n/a – Flow data has yet to be received from the interfaces.
-
1x - Sample rate is 1-to-1 (data is not sampled).
-
<n>x – The sample rate (e.g., if 1 packet out of 100 packets is received, this column displays 100x).
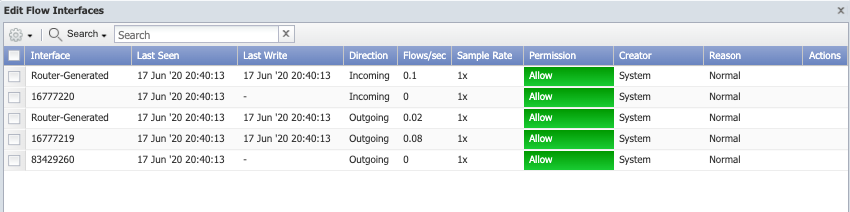
The sample rate enables SevOne NMS to scale the data to compensate for the lack of notification of sampled data. The Sample Rate column is only available when you select the Display Flow Sample Rates check box on the Cluster Manager > Cluster Settings tab > FlowFalcon subtab.
-
-
Permission - Displays Allow when data is processed across the interface. Displays Deny when data is not processed across the interface.
-
Creator - Displays System when SevOne NMS creates the interface or a FlowFalcon Interface rule updates the interface. Displays User when a user creates or updates the interface.
-
Reason - Displays Normal when data can be processed across the interface. Displays Exceeds Capacity when the object count exceeds the peer license capacity and flows cannot be processed for the interface. For licensing purposes, each interface is equal to 300 objects.
-
-
To manage the interface(s), select one or more interface from the list. Click
 drop-down and select one of the following options.
drop-down and select one of the following options. 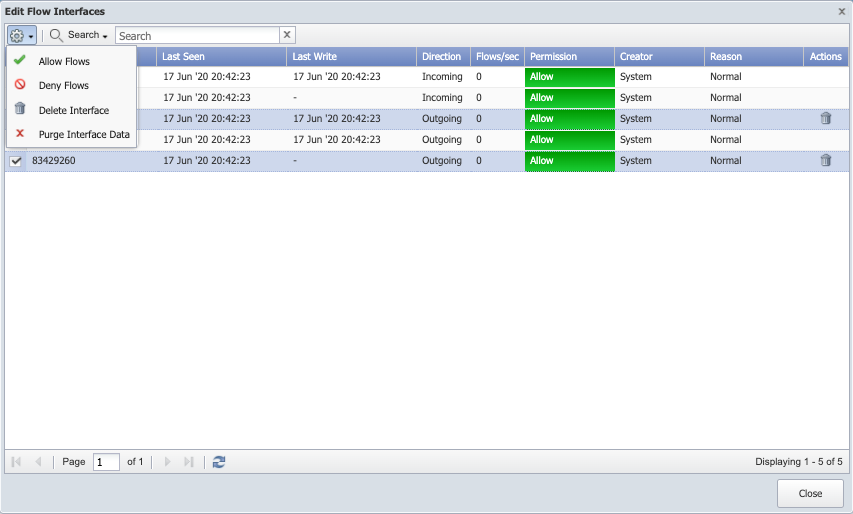
-
Allow Flows - to process the flow data across the selected interface(s).
-
Deny Flows - to not process the flow data across t he selected interface(s).
-
Delete Interface - to delete the selected flow device interface(s) and its associated flow data.
-
Purge Interface Data - to delete the flow data for the interfaces.
-
Delete Interface Level Flow
-
Select an interface from the list or hover in the Actions column on a row for the interface you want to delete. Click on
 to delete the selected interface and its associated flow data.
to delete the selected interface and its associated flow data. 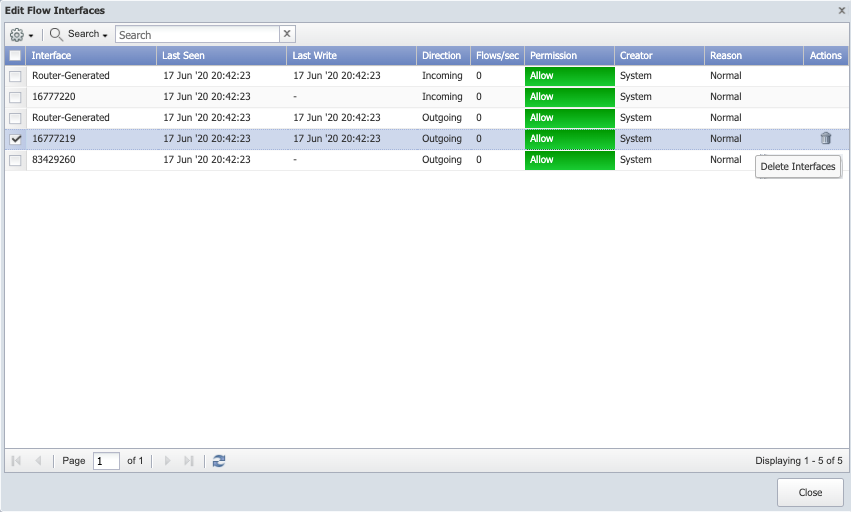
-
Click on OK in the warning message pop-up if you are sure you want to delete the selected interface. Click on Cancel or x to cancel the operation.
This allows deletion of only one selected interface at a time.
FlowFalcon View Editor
The FlowFalcon View Editor lets you define which flow template fields that devices send to SevOne NMS are used in the FlowFalcon views you use to create FlowFalcon reports. In this section, we'll look at the following activities:
-
Creating FlowFalcon views
-
Viewing template information for devices
-
Editing template fields
-
Creating synthetic key fields
Manage FlowFalcon Views
Perform the following steps to create (or edit) a FlowFalcon view.
-
From the navigation bar, click Administration and select Flow Configuration , then FlowFalcon View Editor .
-
The FlowFalcon Views tab is selected by default.
-
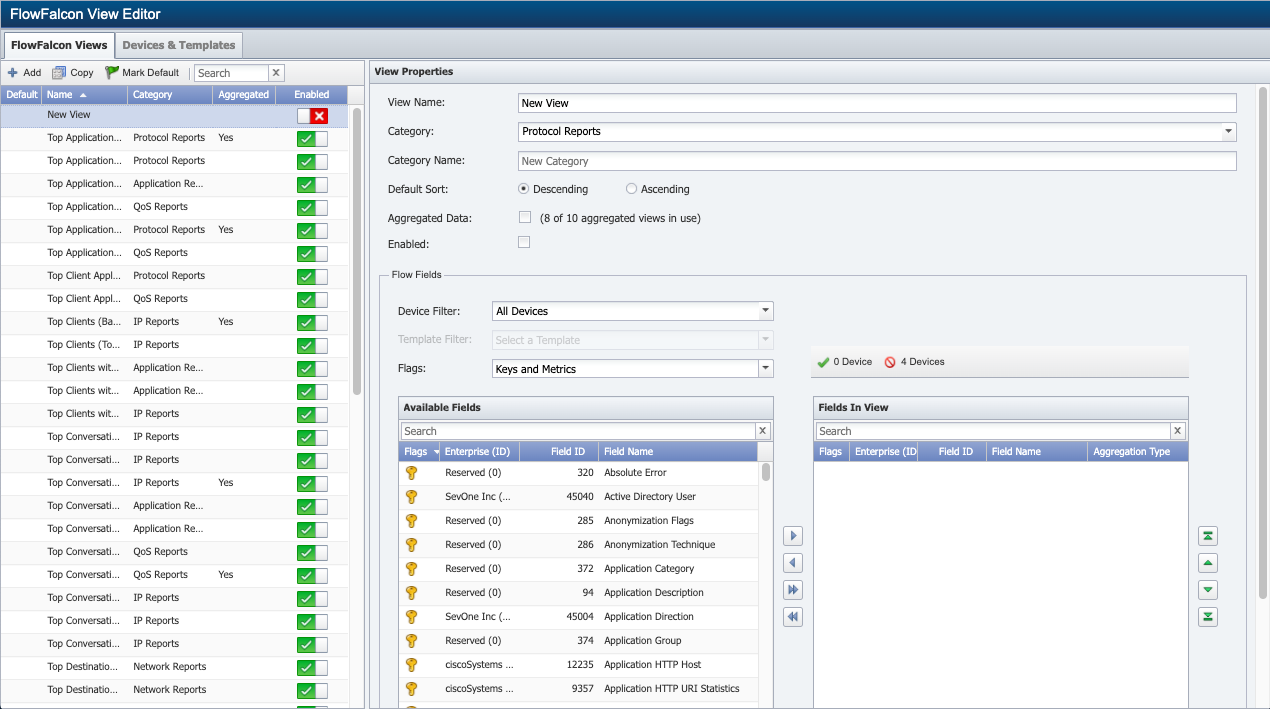
On the left side of the page, click Add. A view named New View will appear in the list. The properties for your new view appear on the right side of the page, under View Properties.
-
Under View Properties, in the View Name field, provide a name for the view.
-
Click the Category drop-down and select a category. To select a category that's not in the list, select New Category.
-
In the Category Name field, perform one of the following actions:
-
If you selected New Category in the previous step, provide a name for the new category.
-
If you selected an existing category in the previous step, there's no need to provide input here. However, if you do provide a different name here, it will appear as an additional category in the Category drop-down selection.
-
-
For Default Sort, select one of the following options:
-
Descending - to sort results in descending order (high to low).
-
Ascending - to sort data in ascending order (low to high).
-
-
Select the Aggregated Data check box to create a view based on aggregated flow data. To create a view using raw flow data, leave the check box clear. There is a limit to the number of aggregated views your appliance can support.
For an existing FlowFalcon view, if you previously selected the Aggregated Data check box and later clear it, you will lose all aggregated data for the view.
-
Select the Enabled check box to enable the use of the view in FlowFalcon reports.
-
The Flow Fields section allows you to specify which fields to include in the view. Perform the following actions to configure the Flow Fields settings.
-
Click the Device Filter drop-down and select a device to display flow fields from.
-
Click the Template Filter drop-down and select one of the templates for the device that you selected.
-
Click the Keys and Metrics drop-down and select one of the following options:
-
Keys and Metrics - to display both keys and metrics.
-
Keys - to display only keys.
-
Metrics - to display only metrics.
-
-
The Available Fields column provides a list of fields that you can include in your view. Click on fields to select them. Once you've made your selection, click
 to move the fields to the Fields In View column.
to move the fields to the Fields In View column. -
The fields display in the report in the same order that they're listed in the Fields In View column. Also, the report sorts on the first metric type listed in the field. To change the order, click on the fields and use the green up/down arrow buttons to move them to the desired location.
-
-
Click one of the following:
-
Save As New - to save a new view. If you're editing an existing view, you can make a copy of the view by clicking Save As New. This is useful if you previously configured the view to use aggregated data but are now changing from aggregated data to raw data. When you save the view as new in this case, you can keep the aggregated data from the original view.
-
Save - this option appears if you're editing an existing (previously saved) view. Clicking Save will overwrite the view with any changes that you make. This can result in losing any aggregated data if you're working with an aggregated view.
-
Reset - to reset the settings to what they were before you started editing the view.
-
Delete - to delete the view along with any associated aggregated data.
-
Devices & Templates Tab
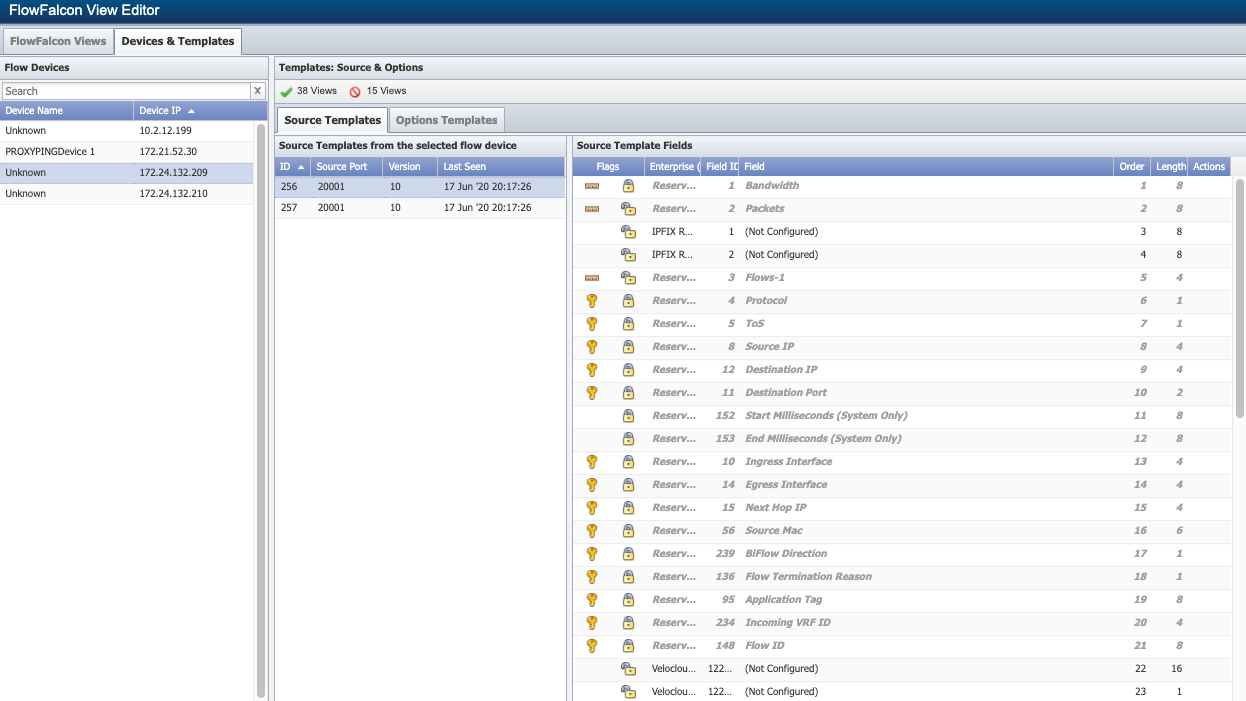
Click on the Devices & Templates tab to view template information for the devices that you enable to send flow data. On the left side of the page, the Flow Devices section lists all of the flow-enabled devices along with their IP addresses. The Source Templates tab and the Option Templates tab appear on the right side of the page. We'll be taking a closer look at both of these tabs in the steps that follow.
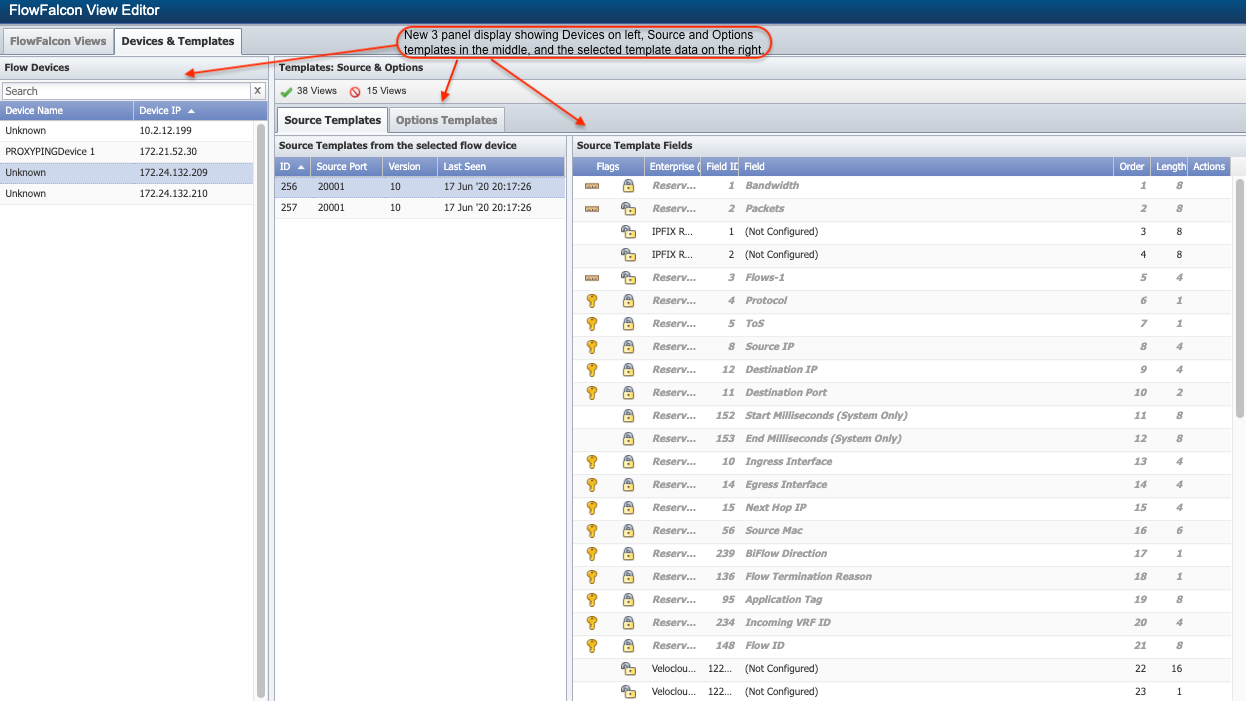
Perform the following steps to view source templates and source template fields for devices.
-
On the left side of the page, under Flow Devices, select the device that you would like to see template information for.
-
Under Templates: Source & Options, the Source Templates tab is selected by default.
-
Under Source Templates from the selected flow device, you'll see a list of the available source templates for the device. The following information is available for each source template:
-
ID - displays the field identifier sent from the device with the flow template.
-
Source Port - displays the port on the device that the flow template was sent from.
-
Version - displays the flow version.
-
Last Seen - displays the last time the template was received from the device.
-
-
Select one of the source templates to view the fields for it.
-
To the right, under Source Template Fields, are all of the available fields for use in FlowFalcon views for FlowFalcon reports. The following information is available:
-
Flags:
-
 - indicates that the flow field is a key.
- indicates that the flow field is a key. -
 - indicates that the flow field is a metric.
- indicates that the flow field is a metric. -
 - indicates that you can edit the field.
- indicates that you can edit the field. -
 - indicates that you can't edit the field.
- indicates that you can't edit the field.
-
-
Enterprise (ID) - displays the identification of the enterprise (typically the manufacturer) that creates the field identifier.
-
Field ID - displays the flow template field identifier.
-
Field - displays the field name.
-
Order - displays the sequence location of the field within the flow template.
-
Length - displays the size of the field in bytes.
-
Perform the following steps to edit template fields.
These steps apply to template fields on both the Source Templates tab, which we just looked at, and the Options Templates tab, which we'll be looking at next.
-
Select a field and click
 under Actions to display a pop-up where you can edit the field settings.
under Actions to display a pop-up where you can edit the field settings. -
Under Name and Type, in the Name field, edit the field name.
-
Select one of the following:
-
Select Key to define the field as a key.
Example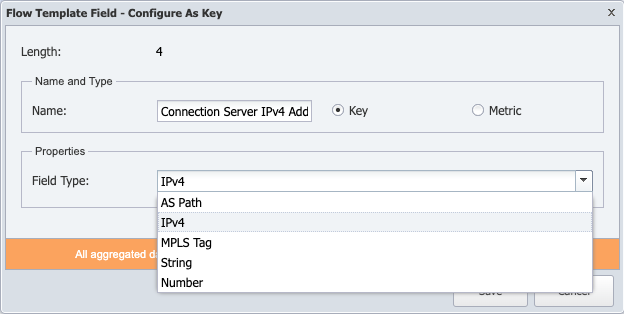
-
Click the Field Type drop-down. Select the appropriate field type from the drop-down. The drop-down options depend on the key length.
Key Length
Field Types
1
Direction, Protocol, String, Number
2
Port, Interface, String, Number
4
AS Path, IP, MPLS Tag, String, Number
6
MAC, String
8
String, Number
16
IP Hybrid, IPv6, String
32
String
128
AS Path, String
If field is a variable-length field, then String is the only option available. And, there is no drop-down available for this scenario.
256
String
-
Select one of the following if field type String or Number is chosen.
-
Select Without Lookup to not use a lookup table for the field.
-
Select Lookup Table to use a lookup table for the field. If you select this option perform the following steps.
-
Click the Lookup Table drop-down.
-
Select the lookup table for the field to use.
-
Select New Lookup Table and enter the lookup table name in the Name field to define a new lookup table.
-
-
Click Add Code or click

to add or edit a code in the lookup table.
-
In the Code field, enter the lookup table code.
-
In the Value field, enter the code value.
-
Click Update to save the code.
-
Repeat to add additional codes to the lookup table.
-
-
If an editable field has a length of 1, 2, 4, or 8, it can also be configured as a Metric.
-
-
Select Metric to define the field as a metric.
Example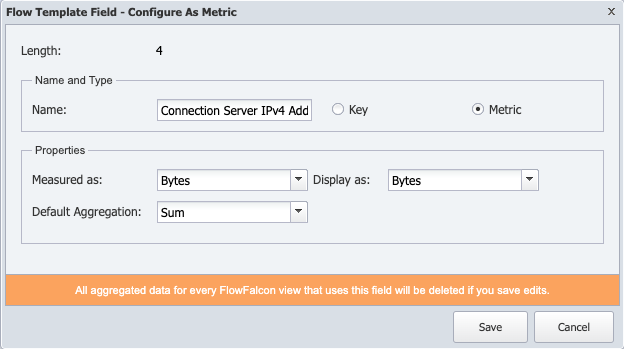
-
Click Measured as drop-down to choose how to measure the metrics.
-
Click Display as drop-down to choose how to display the metrics.
-
Click the Default Aggregation drop-down and select the aggregation to use by default.
-
-
-
Click Save.
Options Templates Tab
Devices sometimes send metadata via NetFlow using a feature known as "Options Templates". On the Options Templates tab, you can view options templates and options template fields. You can can also create synthetic key fields by combining existing options template fields. Once you create a synthetic key field, it will appear in the Source Template Fields, which we looked at earlier (see Source Templates Tab). This means that the new synthetic key field will be available for use in FlowFalcon views and FlowFalcon reports.
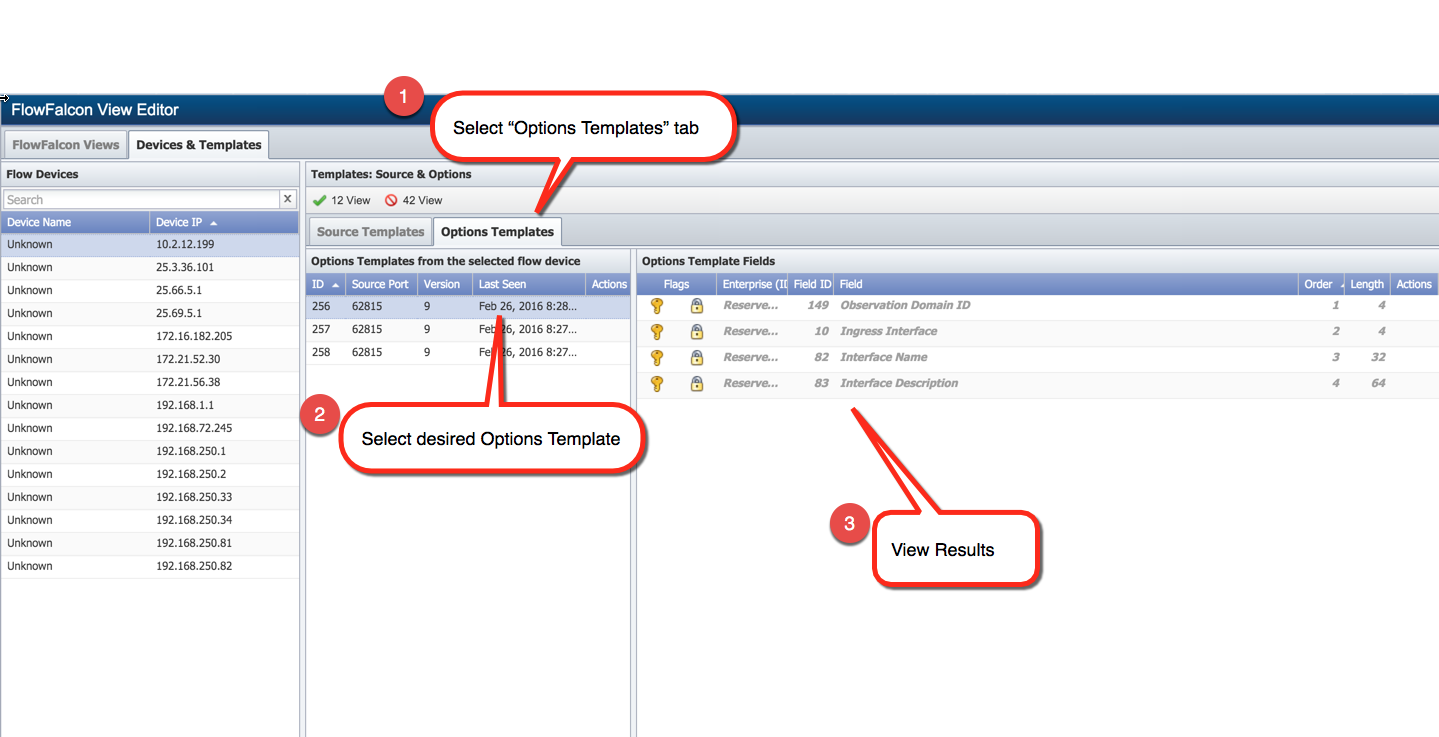
Perform the following steps to view options templates for devices and to create a synthetic key field.
-
On the left side of the page, under Flow Devices, select the device that you would like to see template information for.
-
Select the Options Templates tab.
-
Under Options Templates from the selected flow device, select an options template to view the fields for it under Options Template Fields.
All fields have to be configured before you continue. For any fields that display Not Configured, see the steps in the Edit Template Fields section above.
-
Again under Options Templates from the selected flow device, select an options template that you want to create a synthetic key field for. Under Actions, click
 to display the Synthetic Key Field Editor pop-up.
to display the Synthetic Key Field Editor pop-up. 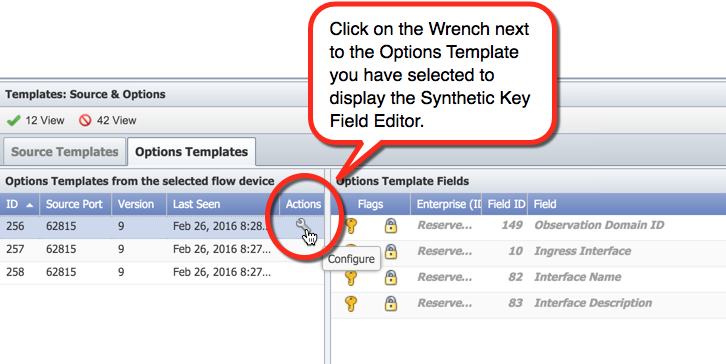 About Synthetic Key Fields
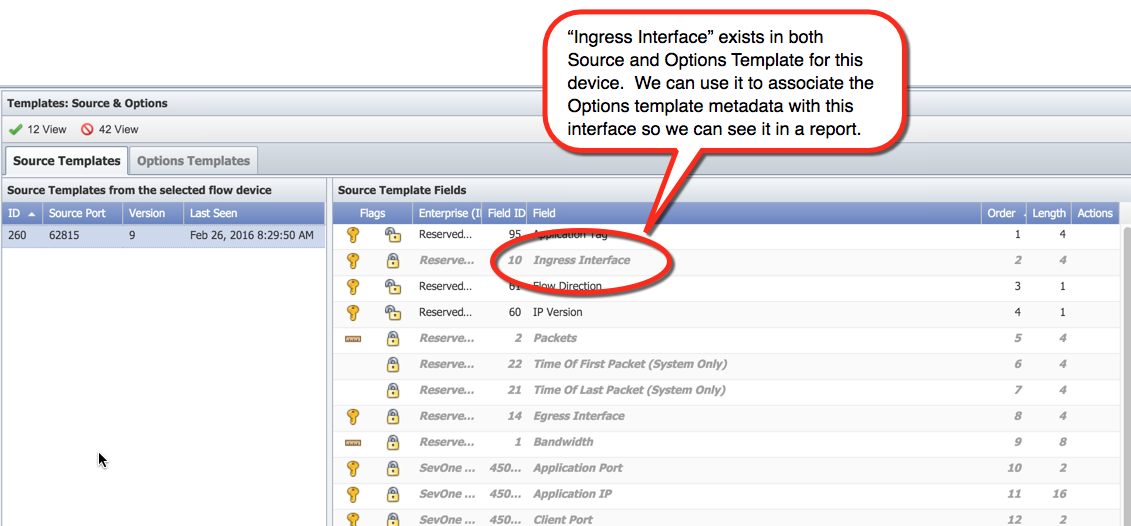
About Synthetic Key FieldsA Synthetic Key Field is used to create an association between a field in the source template and the metadata supplied by the Options Template. Without this association, there would be no way to see the metadata in FlowFalcon reports. In the image below, we see a source template for our device. Within the source template, there's a field called Ingress Interface. Looking at the Options Template image above, we also see a field called Ingress Interface. Because the field exists in both the source and options template, we can use it as a reference point to link the metadata from the Options Template to the tuple containing the Ingress Interface field.
-
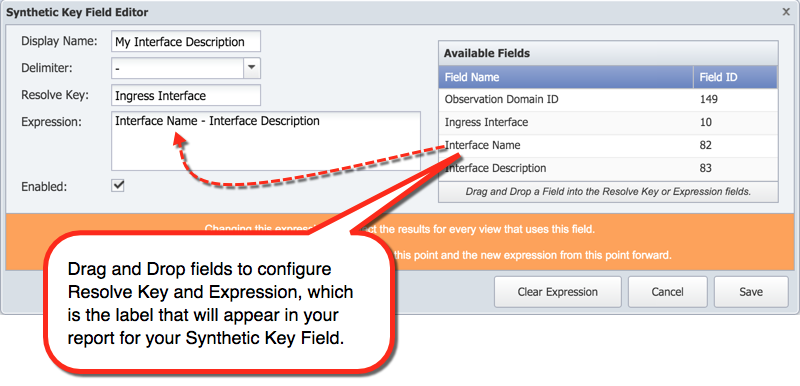
Perform the following actions to configure the synthetic key field.
-
In the Display Name field, enter a name to display in FlowFalcon Reports.
-
Click the Delimiter drop-down and select a delimiter to display between the fields that you plan to add here.
-
In the Resolve Key field, you're going to specify the key field to resolve on. On the right side, under Available Fields, select a field and drag it to the Resolve Key field.
The field you select here has to exist in the source template. It also has to be a string field type.
-
In the Expression field, you'll combine the available fields into a single synthetic field, which will display in reports. On the right side, under Available Fields, select fields to add to the expression and drag them to the Expression field.
The Expression field accepts fields that have generic storage type or string storage ty pe. You can see the storage type for each of the available fields under Storage Type.
-
Select the Enabled check box to make the field available for inclusion in FlowFalcon views and FlowFalcon reports.
-
Click Save.
-
-
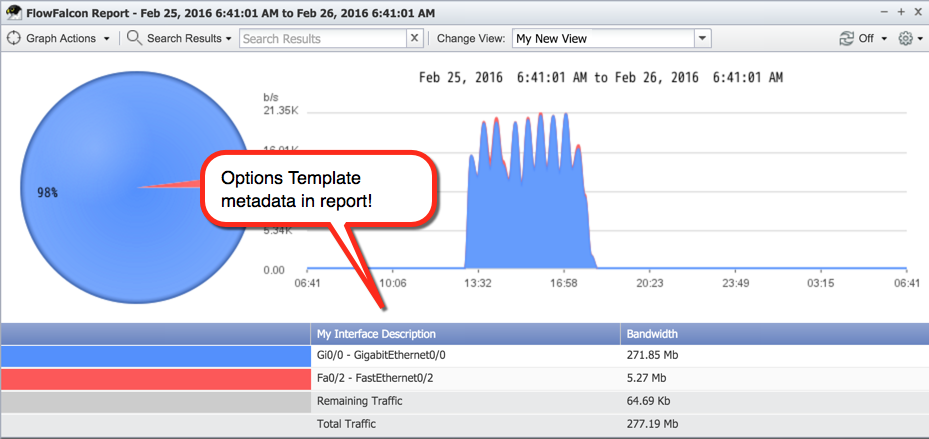
Once you've created your Synthetic Key Field, you can now add it to a View and then see it in reports:
The MPLS Flow Mapping page lets you upload your network's MPLS flow map files. These files map MPLS attributes to flow data so that MPLS data can appear in FlowFalcon reports. You'll need to understand MPLS well enough to know which MPLS attributes correspond to your network's VPN 2nd Top Layer ID, PE Egress Address, Customer VRF, Source IP Address, and PE Ingress Address. Use any application to create two .csv files that map MPLS attributes to flow data. Then use this page to upload the map files into SevOne NMS. The .csv files must be encoded in UTF-8.
SevOne NMS requires the following three actions to map MPLS attributes to flow data for FlowFalcon reports:
-
On the Cluster Manager > Cluster Settings tab > FlowFalcon subtab, select the Enable MPLS Attribute Mapping check box and enter the MPLS Attribute Mapping Refresh Interval. (We discussed these settings in the Configure Cluster-level Flow Settings section.)
-
On the MPLS Flow Mapping page, upload two MPLS mapping files. The steps for this are below.
-
On the FlowFalcon View Editor, create FlowFalcon views that include at least one of the following fields. (We discussed creating FlowFalcon Views in the Manage FlowFalcon Views section.)
-
45050: Customer Client IP
-
45051: Customer Client Subnet
-
45052: Customer VRF Name
-
45053: Customer Application IP
-
45054: Customer Application Subnet
-
45055: PE Ingress IP
-
45056: PE Egress IP
-
Upload Map Files to DNC
The map files must be uploaded to a single SevOne Dedicated NetFlow Collector (DNC) that uses the file. Because each DNC may be responsible for different mappings, it is necessary to upload a mapping file to each DNC that performs mapping. In order to direct the mapping file to a DNC, first navigate to the IP of the DNC, then upload the file.
Upload Map Files in SevOne NMS
Perform the following steps to upload the two files that map MPLS attributes. The first map file maps the VPN 2nd Top Label ID, PE Egress Address, and Customer VRF. The second one maps the Customer VRF, Source IP Address, and PE Ingress Address.
-
From the navigation bar, click Administration and select FlowConfiguration, then MPLS Flow Mapping.
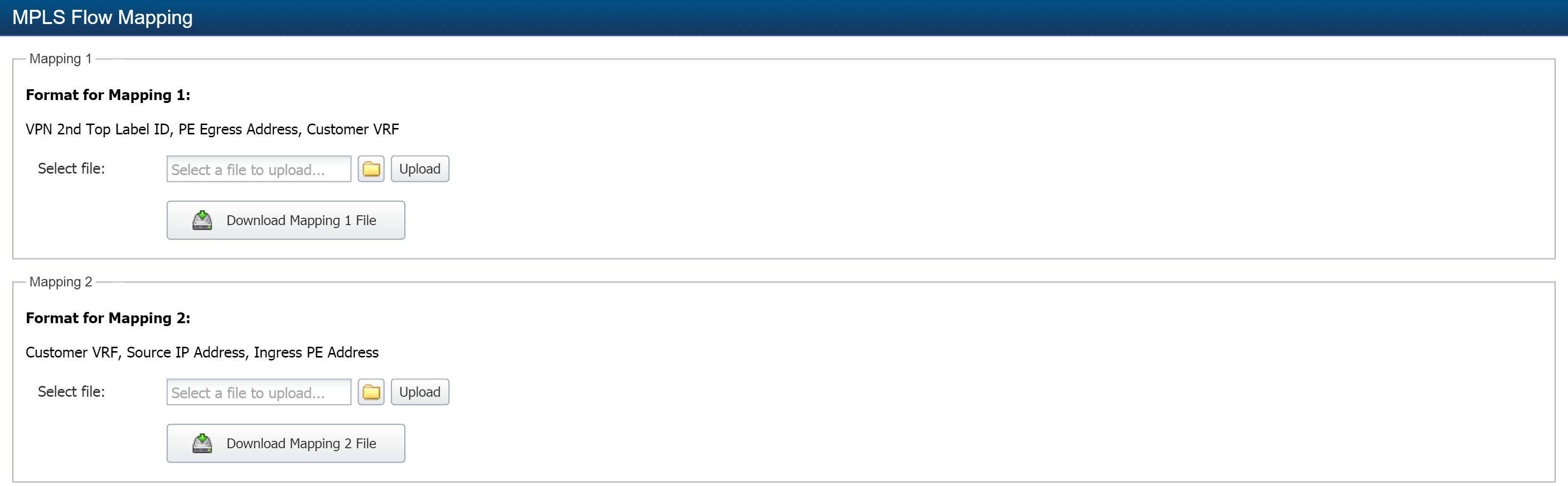
-
In the Mapping 1 section, click
 to display the file upload pop-up.
to display the file upload pop-up. -
Navigate the file structure to locate and select the file that maps the VPN 2nd Top Label ID, PE Egress Address, and Customer VRF.
-
Click Open on the pop-up to save the file locally.
-
Click Upload to move the file to the correct location and to complete the upload of the first map file.
-
Click Download Mapping 1 File to display the content of the first map file in a .csv format.
-
In the Mapping 2 section, click
 to display the file upload pop-up.
to display the file upload pop-up. -
Navigate the file structure to locate and select the file that maps the Customer VRF, Source IP Address, and PE Ingress Address.
-
Click Upload to move the file to the correct location and to complete the upload of the first map file.
-
Click Download Mapping 2 File to display the content of the second map file in a .csv format.
Network Segment Manager
The Network Segment Manager lets you define network segments to group flow data. You group subnets into the network segments, which enables you to identify the traffic that comes from the group of networks. You can create network segments that contain multiple subnets with the same name to group flow data. The network segments you define here appear on the Report Attachment Wizard and on the FlowFalcon Reports page in the Network Segment drop-down list.
Perform the following steps to manage network segments.
-
From the navigation bar, click Administration and select FlowConfiguration, then Network Segment Manager.
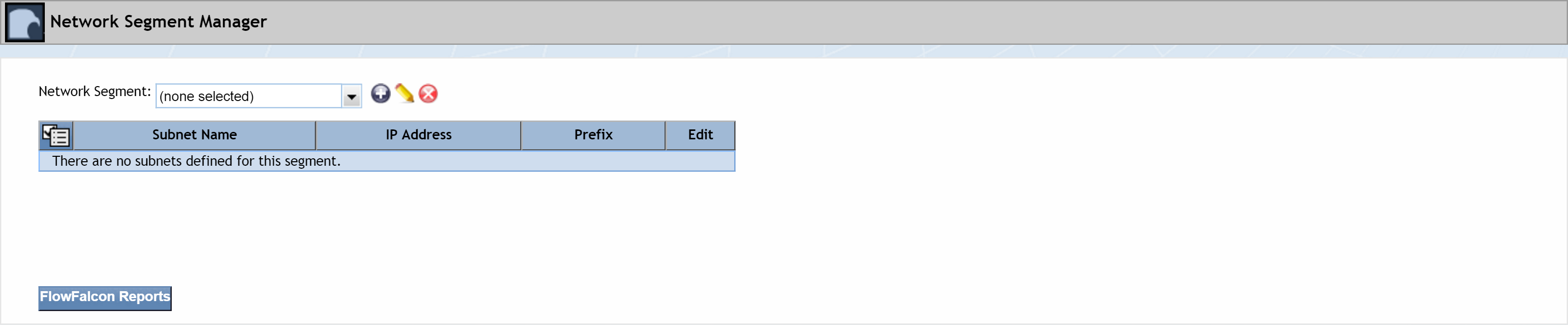
-
Click the Network Segment drop-down and select a network segment to view its subnets. The subnets appear in the table below it.
-
Click
 to create a new network segment. In the Network Segment pop-up, enter the name for it, then click Save.
to create a new network segment. In the Network Segment pop-up, enter the name for it, then click Save. 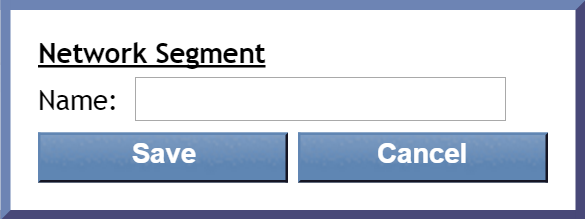
-
To edit an existing network segment, select the segment from the Network Segment drop-down. Then click
 to display the Network Segment pop-up, where you can change its name.
to display the Network Segment pop-up, where you can change its name. -
To delete a network segment, select the segment from the Network Segment drop-down and click
 .
. -
Perform the following actions to add a subnet.
-
Click
 and select Add New Subnet to display the Subnet pop-up.
and select Add New Subnet to display the Subnet pop-up. To edit an existing subnet, first click the Network Segment drop-down and select a network segment. Then select the subnet that you would like to edit and click
 to display the Subnet pop-up. Continue with the actions below.
to display the Subnet pop-up. Continue with the actions below. 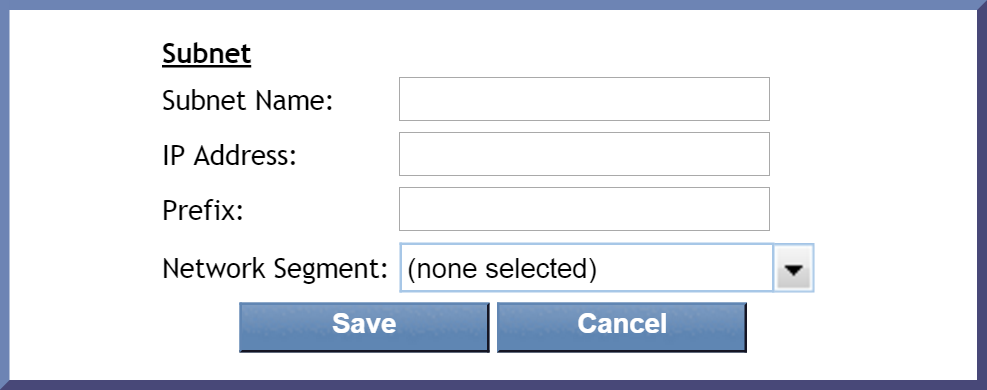
-
In the Name field, enter the subnet name.
When you create more than one subnet with the same name, the data from those subnets is combined in reports. For example, let's say that you have subnets 192.168.30.0/24 and 192.168.20.0/24. You name both subnets Web Servers. FlowFalcon reports combine the traffic from both Web Servers subnets and display one result.
-
In the IP Address field, enter the subnet IP address.
-
In the Prefix field, enter the subnet prefix (also referred to as the CIDR address, network mask, or number of borrowed bits, e.g., /24).
-
Click the Network Segment drop-down and select the network segment that you want to associate the subnet to.
-
Click Save.
When you add a new subnet (or edit an existing subnet), the canonical IP address for the subnet will appear in the table based on the IP address and prefix that you provide. For example, if you provide the IP address 192.168.10.1 and the prefix 8, the IP address that will appear for the network segment would be 192.0.0.0.
-
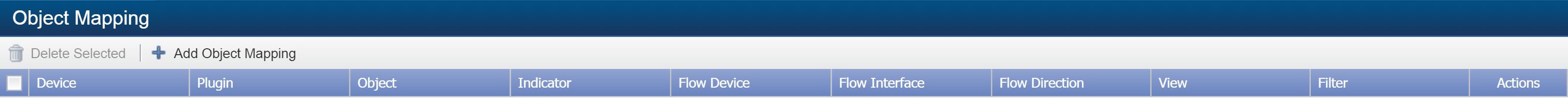
Object Mapping
On the Object Mapping page, you can map indicators on SevOne devices to flow interfaces on the devices that send flow data to SevOne NMS. This means that you'll be able to display a FlowFalcon report of the flow data related to poll data from an indicator that appears in a SevOne NMS Instant Graph.
When you map an indicator to a flow interface, you'll specify a for the FlowFalcon Reports page to display for that indicator's interface data.
Let's say that you want to display the flows for QoS queues. In that case, you'd create an object mapping that uses a FlowFalcon view that contains DSCP and has an appropriate filter to display a FlowFalcon report of the traffic that moves across the queue.
Add Object Mapping
Perform the following steps to add (or edit) an object mapping.
-
From the navigation bar, click Administration and select Flow Configuration, then Object Mapping.
-
Click Add Object Mapping to display the Add Object Mapping pop-up.
To edit an existing object mapping, select it and click
 to display the Edit Object Mapping pop-up. Continue with the steps below.
to display the Edit Object Mapping pop-up. Continue with the steps below. 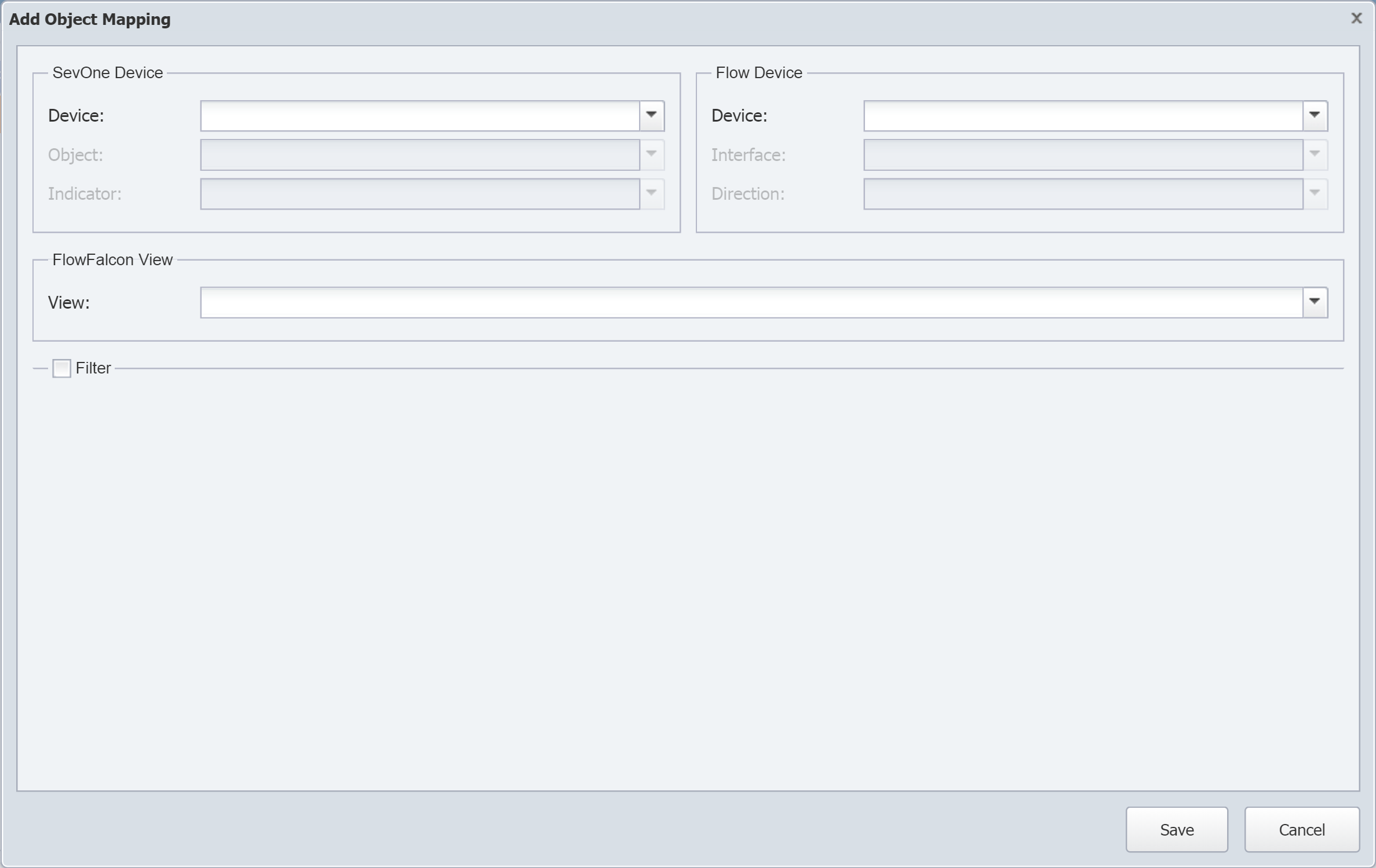
-
In the SevOne Device section, perform the following actions:
-
Click the Device drop-down and sele ct the device that contains the indicator that you want to map to a flow interface .
-
Click the Object drop-down and select the object that contains the indicator that you want to map to a flow interface .
-
Click the Indicator drop-down and select the indicator that you want to map to a flow interface .
-
-
In the Flow Device section, perform the following actions:
-
Click the Device drop-down and select the flow device that contains the interface that sends flow data to SevOne NMS.
-
Click the Interface drop-down and select the flow interface to map the indicator to .
-
Click the Direction drop-down and select the direction of the interface mapping.
-
-
Under FlowFalcon View, click the View drop-down and select the view for the FlowFalcon Reports page to display for the indicator's interface data.
-
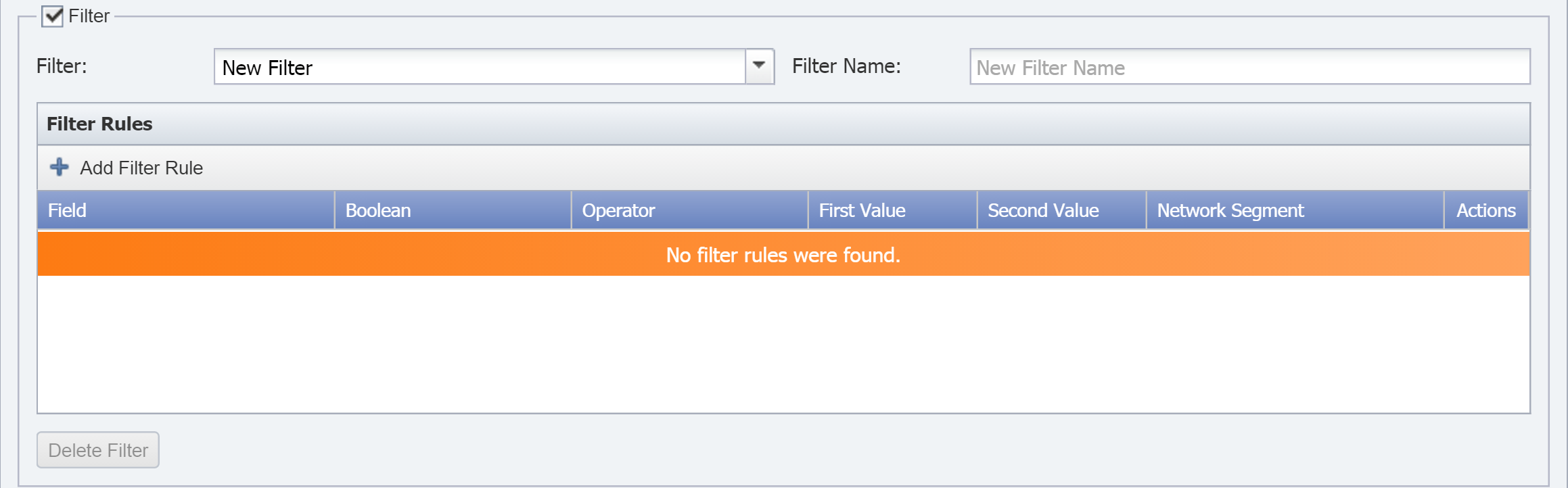
To add a filter that limits the results from the object mapping, select the Filter check box and perform the following actions:
-
To create a new filter, select New Filter.
To use an existing filter, click the Filter drop-down and select the filter.
-
In the Filter Name field, enter the filter name.
-
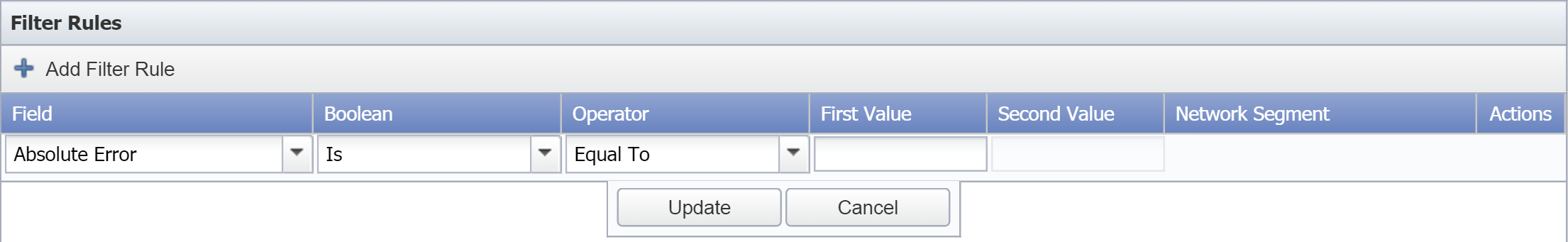
Under Filter Rules, click Add Filter Rule to add a new filter rule. Continue with the actions below to provide input for the fields that appear.
-
Click the Field drop-down and select the field to apply the rule to. The fields that appear first are from the view that you selected under FlowFalcon View. After that, all known fields from flow data appear.
-
Click the Boolean drop-down and select one of the following options:
-
Is - to define the rule with an Is Boolean operator.
-
Is Not - to define the rule with an Is Not Boolean operator.
-
-
Click the Operator drop-down and select a comparison operator.
Depending on the field you selected for Field, the Operator options may include Mask and Subnet (in addition to Equal To, Greater Than, Less Than, and Between). Select Mask to report on flow data that needs to match in the manner of IP address subnet masking. Select Subnet to report on flow data that needs to be from the subnet you select from the Network Segment drop-down. The Network Segment drop-down becomes available when you select Subnet as the operator. For information about defining network segments, please see the section Network Segment Manager.
-
In the First Value field, enter the first value to filter data data on.
-
In the Second Value field, enter the second value in a value range if applicable (for example, when you select Between as an Operator).
-
Click Update to save the rule.
-
-
Click Save to save the object mapping.
Protocols and Services
The Protocols and Services page lets you edit and define new protocols and services that SevOne NMS can collect flow data from. You can create FlowFalcon reports for the protocols and services that you add.
Add a Protocol
Perform the following steps to create a new flow protocol or edit an existing one.
-
From the navigation bar, click Administration and select Flow Configuration, then Protocols and Services.
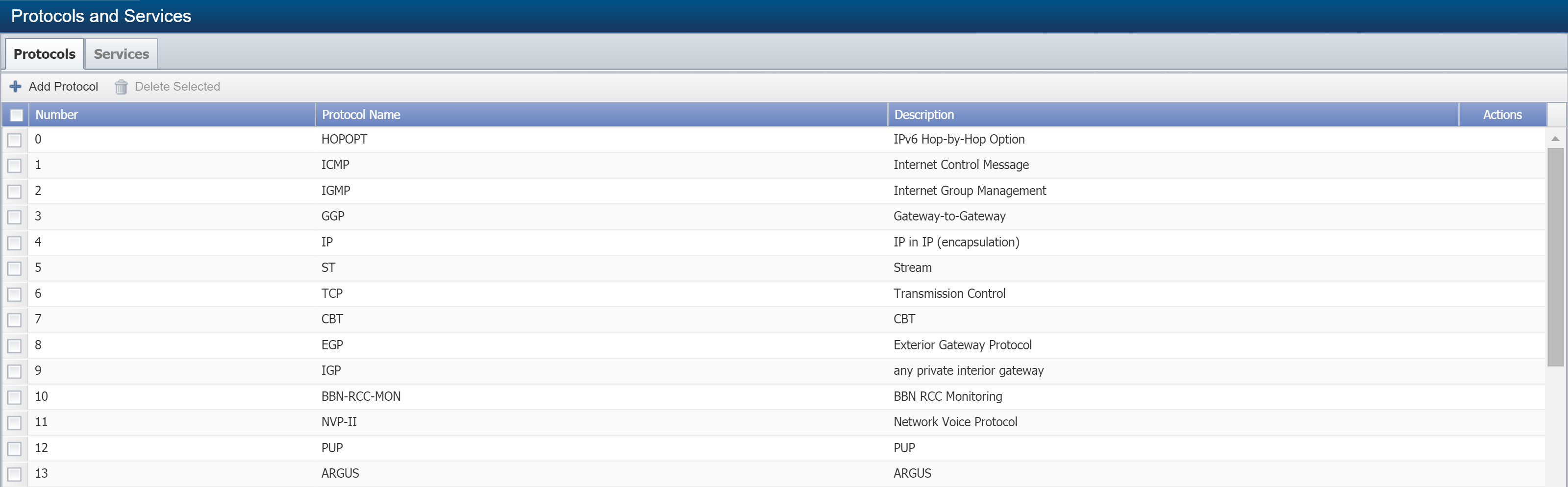
-
On the Protocols tab, click Add Protocol to display the Add Protocol pop-up. To edit an existing protocol, select the protocol and click
 to display the Edit Protocol pop-up.
to display the Edit Protocol pop-up. 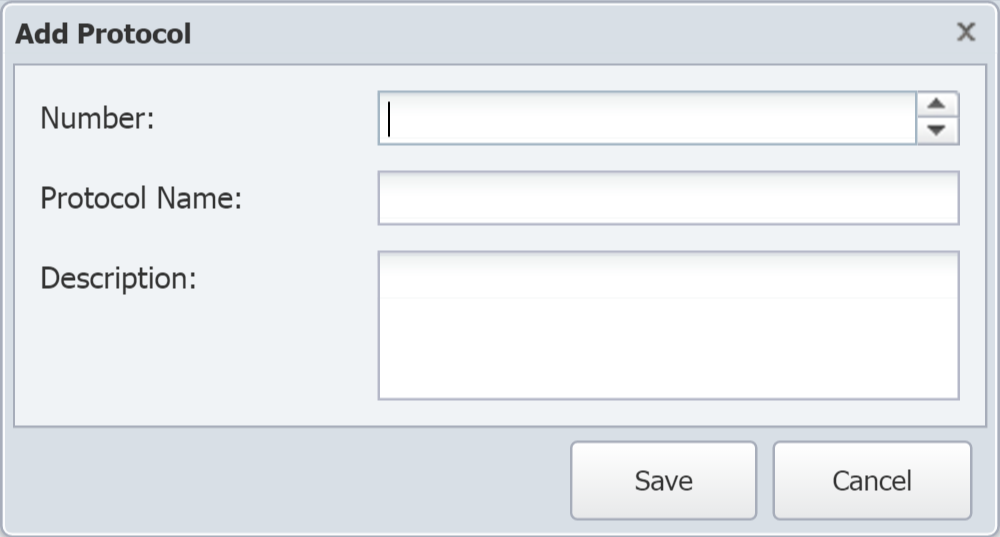
-
In the Number field, enter a unique number for the protocol.
-
In the Protocol Name field, enter the protocol name.
-
In the Description field, enter a description of the protocol.
-
Click Save.
Add a Service
Perform the following steps to add a new flow service or edit an existing one.
-
Select the Services tab.
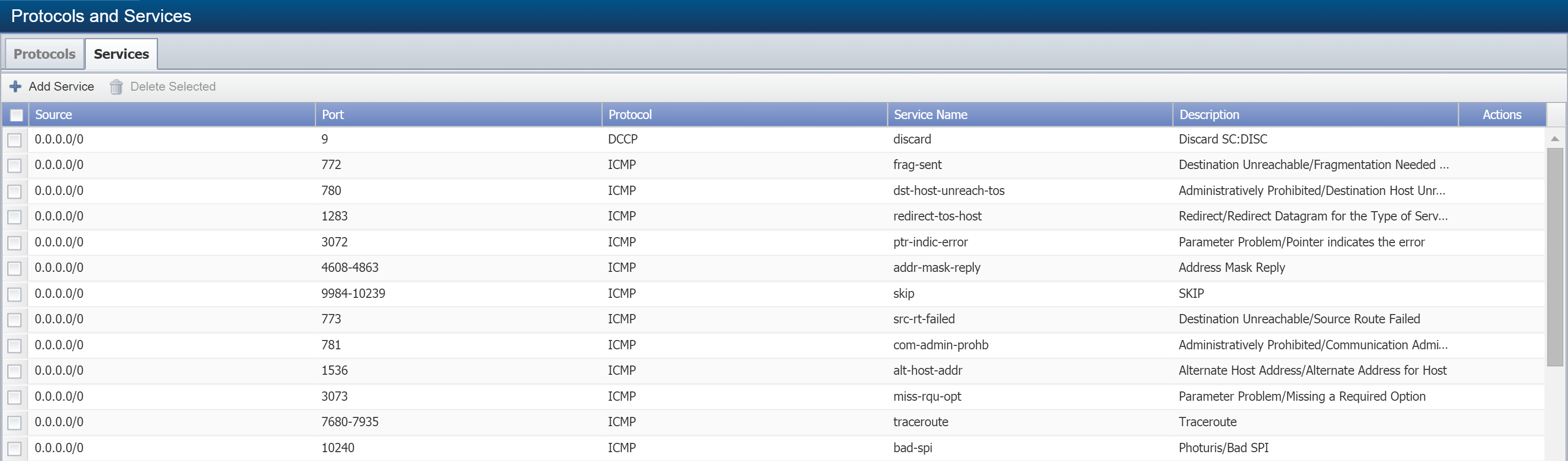
-
Click Add Service to display the Add Service pop-up. To edit an existing service, select the service and click
 to display the Edit Service pop-up.
to display the Edit Service pop-up. 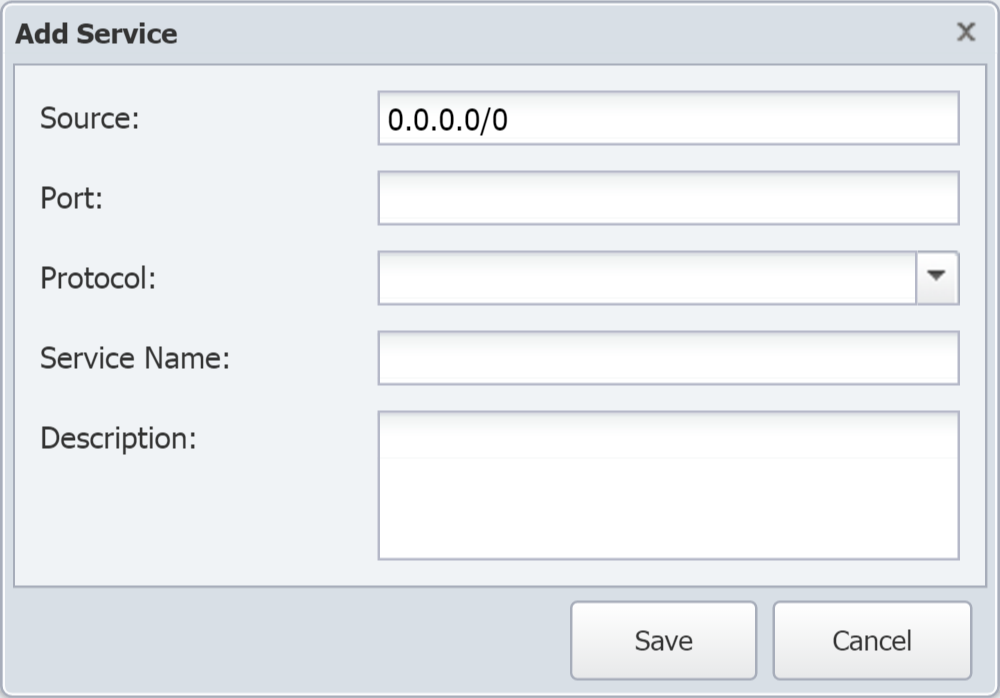
-
In the Source field, enter the IP address of the service coupled with the subnet. To poll for the service from any device, enter 0.0.0.0/0. To poll a specific device for the service, enter an IP address and a subnet.
-
In the Port field, enter the port number that the service uses.
-
Click the Protocol drop-down and select the protocol that the service uses.
-
In the Service Name field, enter the name of the service as it should appear in reports.
-
In the Description field, enter a description of the service.
-
Click Save.
Report Creation
In this section, we'll look at creating FlowFalcon reports in two different ways:
-
Using the Report Attachment Wizard
-
Using the classic FlowFalcon Reports page
Create Reports Using the Report Attachment Wizard
Perform the following steps to create a FlowFalcon report using the Report Attachment Wizard.
Sources
-
From the navigation bar, click Reports and select Create Report.
-
Under Sources, select FlowFalcon.
-
Continue to the next subsection, Resources.
Resources
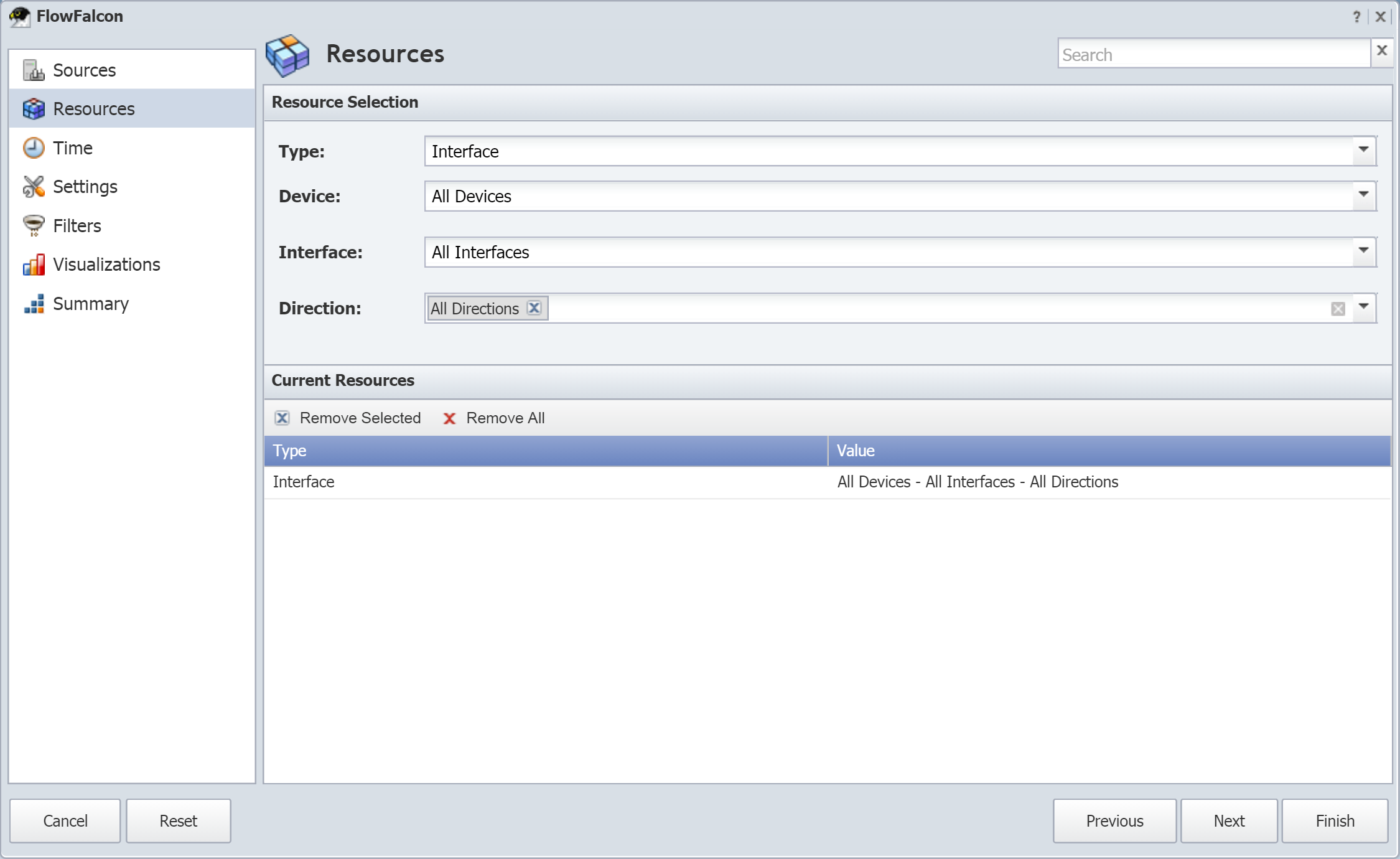
-
Click the Type drop-down and select one of the following options.
-
Interface - to graph flow data from the interfaces you allow on the Flow Interface Manager. After selecting this option, perform the following actions.
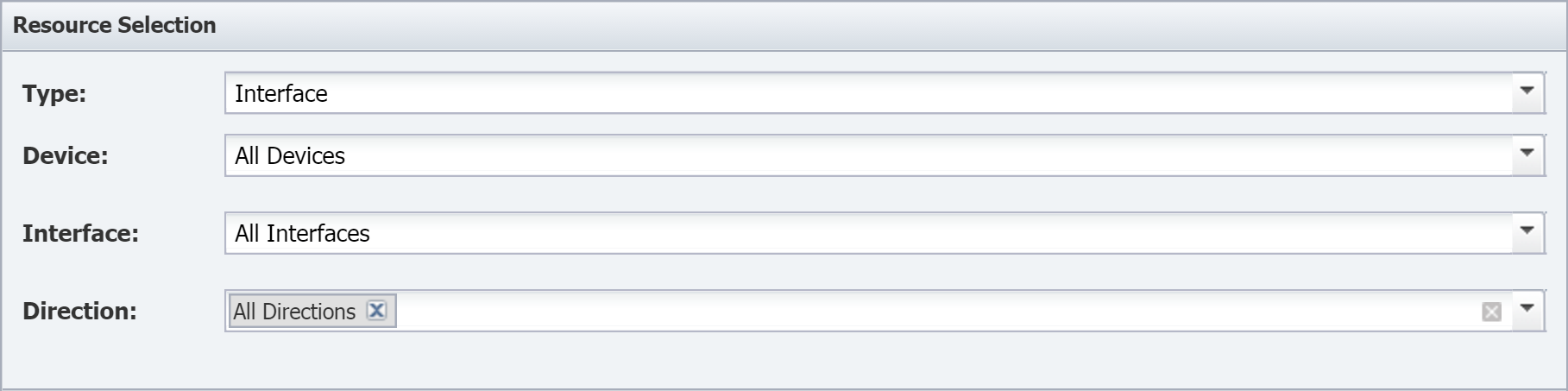
-
Click the Device drop-down and select a device that flow data originates from. Select All Devices to graph flow data from all devices.
-
Click the Interface drop-down and select the interface that flow data originates from. Select All Interfaces to graph flow data from all interfaces on the device you select in the previous step.
-
Click the Direction drop-down and select whether to graph flow data that is Incoming, Outgoing, or for All Directions. Some flow sources provide only incoming data.
-
-
Device Group - to graph flow data for a device group or device type. Click the Device Group drop-down and specify the device type(s) and/or device group(s).
-
Object Group - to graph flow data for an object group. Click the Object Group drop-down and specify the object group(s).
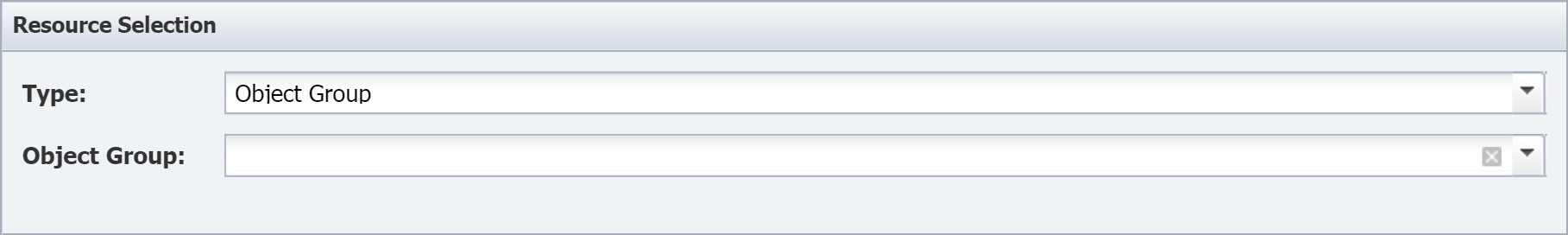
-
-
Click Next and continue to the next subsection, Time.
Time
Perform the following steps to configure time settings for the report attachment.
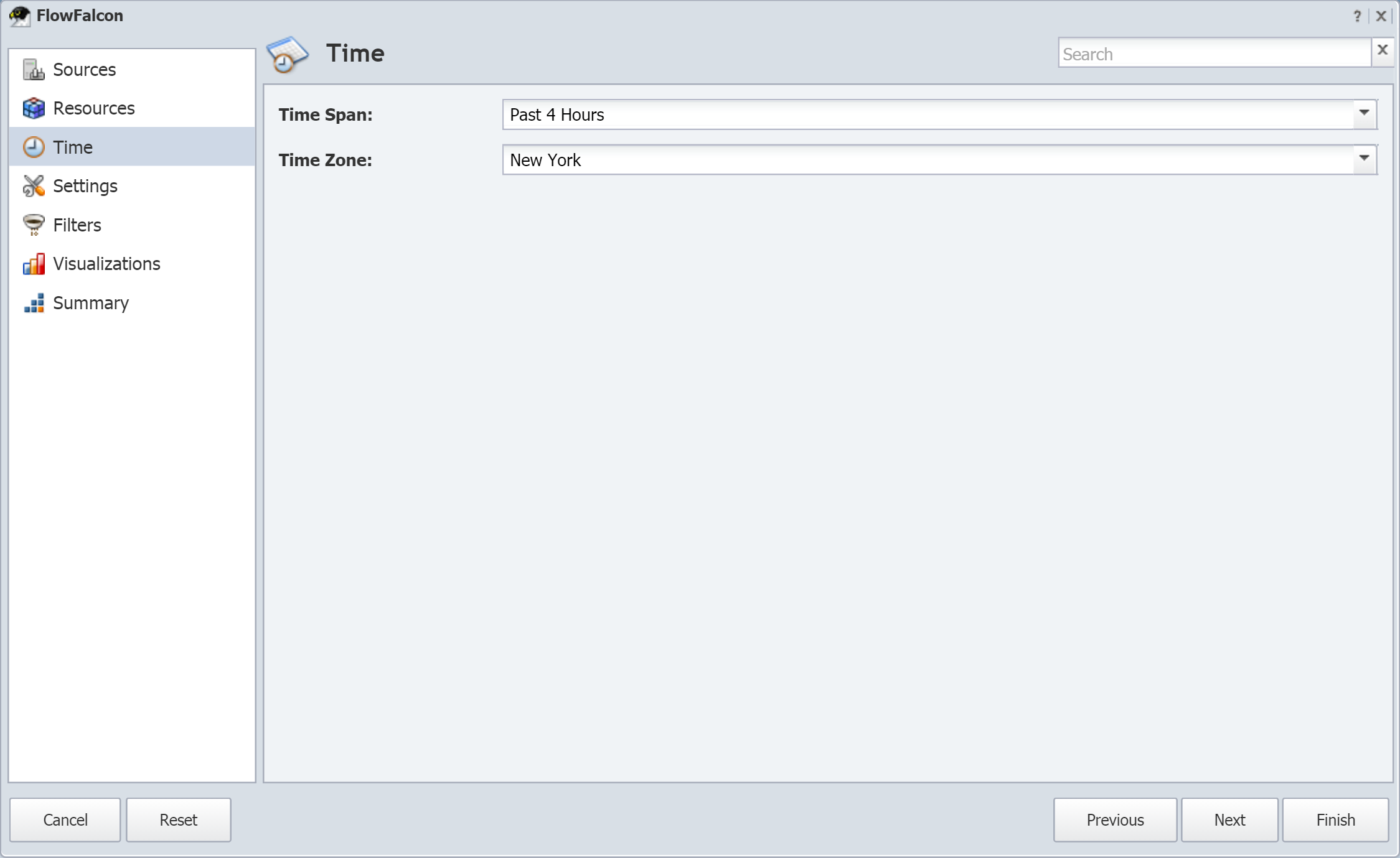
-
Click the Time Span drop-down and select one of the following options. The first three options below are customizable.
-
Specific - to display fields to enable you to define a specific time span.
-
Relative - to display a text field where you can enter a relative time span, such as past 4 hours, last week, this month, today, etc.
-
Week - to display a pop-up where you can designate a specific week in the year by number (for example, week 23), to change when the year begins. You can also specify which day and month should be considered the first (for example, Monday as the first day of the week instead of Sunday).
-
Past <X> Hours, Days, Weeks, Months - to display data from <X> hours, days, weeks, or months ago until now.
-
Today - to display data from 12:00am today until now.
-
Yesterday - to display data from 12:00am yesterday until 12:00am today.
-
This Week, Month, Quarter - to display data from 12:00am on the first day of the week, month, or quarter until now.
-
Last Week, Month, Quarter - to display data from 12:00am on the first day of the last completed week, month, or quarter to 11:59pm on the last day of the last completed week, month, or quarter.
-
-
Click the Time Zone drop-down and select a time zone.
-
Click Next and continue to the next subsection, Settings.
Settings
Perform the following steps to define attachment settings.
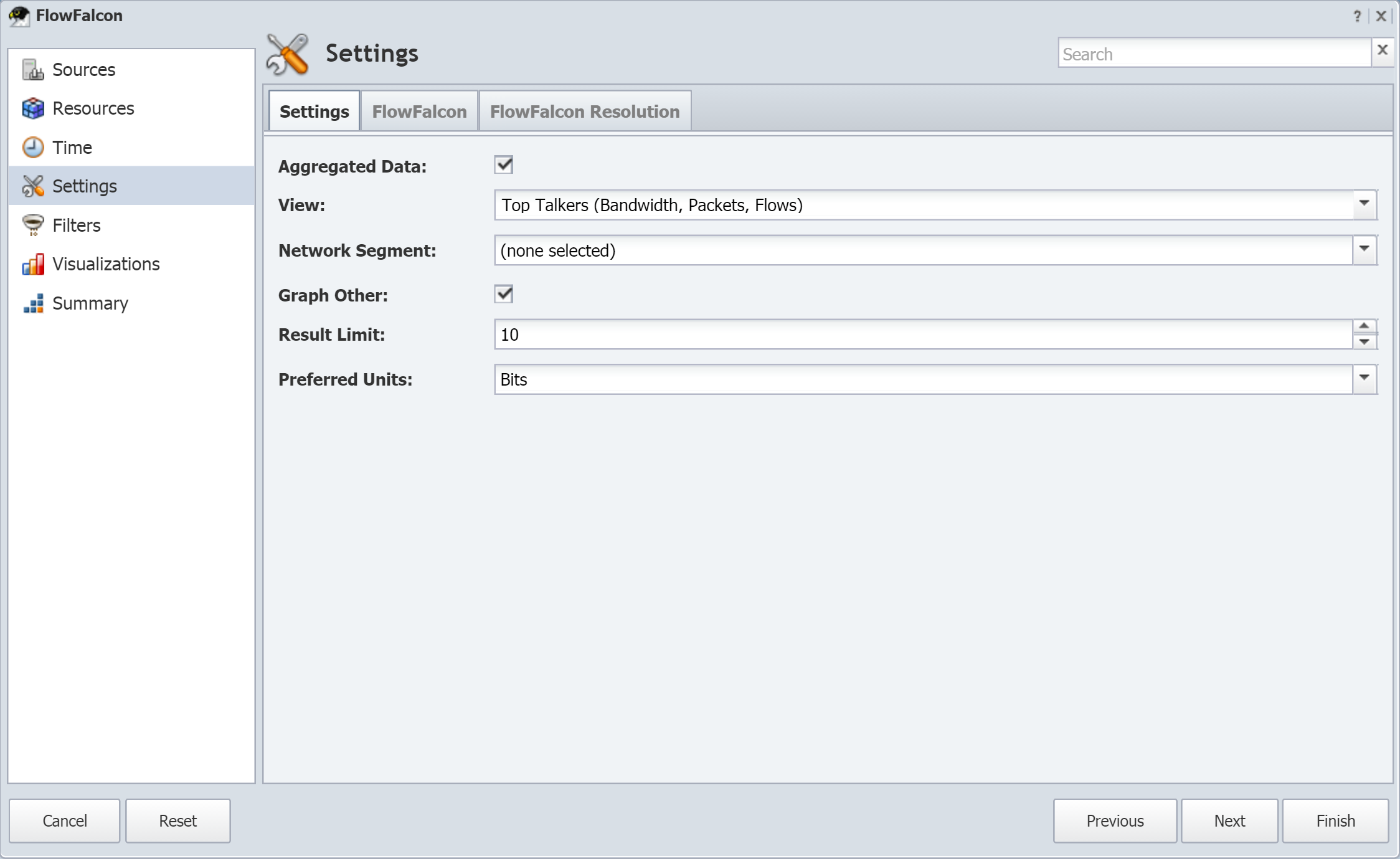
Settings Tab
-
On the Settings tab, select the Aggregated Data check box to populate the View drop-down list with FlowFalcon views that use aggregated flow data (faster and less specific). Leave it clear to populate the View list with views that use raw flow data (slower and more specific).
When you create a TopN flow report (e.g., Top Talkers) based on aggregated data, the report will not be entirely precise. You can increase the value for the Aggregation TopN setting (go to Cluster Manager > Cluster Settings tab > FlowFalcon subtab) for greater precision. However, any value greater than 100 will increase the system load, which may eventually lead to data loss.
-
Click the View drop-down and select a view.
-
Click the Network Segment drop-down and select a network segment. This enables you to resolve IP addresses into segments and to roll up results from the same segment into a single result.
-
If you select the Graph Other check box, SevOne NMS will display the flow for the top <n> results individually in the Pie Visualization and the Stacked Line visualization. It will also display a Remaining Traffic graph item that groups the flow for the remaining flow sources that meet the filter criteria. You'll define the <n> results in the next step.
If you leave the check box clear, SevOne NMS will display only the top <n> results in the Pie visualization and the Stacked Line visualization. Remaining Traffic will still display in the Table visualization.
-
In the Result Limit field, enter the number of individual results to display in the report attachment. Filters enable you to narrow the scope of the request (see the Filters subsection below). You can also modify the Current Resources list (on the Resources page) to limit the number of resources.
-
Click the Preferred Units drop-down and select either Bits for network-oriented data or Bytes for server-oriented data.
FlowFalcon Tab
-
Select the FlowFalcon tab.
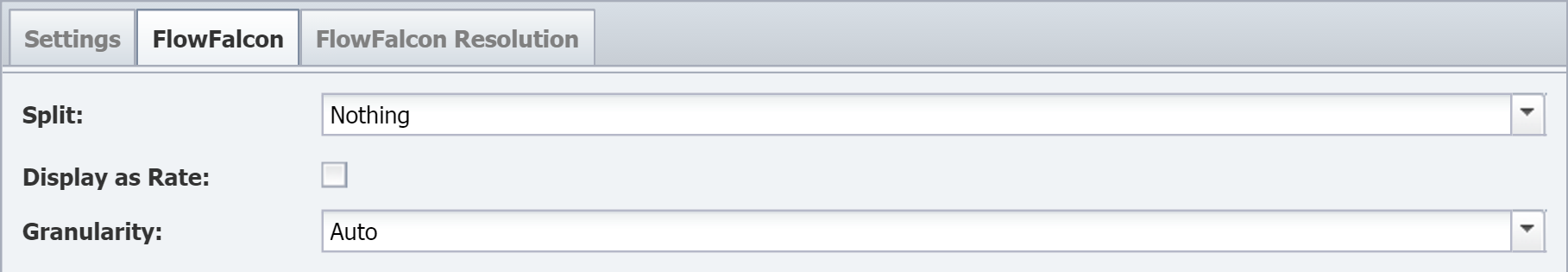
-
Click the Split drop-down and select one of the following options.
-
Groups - to separate flow data by device group/device type or object group, depending on the resource you select. This option only appears when you select Device Group or Object Group on the Resources page.
-
Interfaces - to separate flow data into individual interfaces.
-
Nothing - to combine all results from the same direction across the same interface in order to allow for greater detail in the result set.
-
-
Select the Display as Rate check box to display the results as bits or bytes per second. Leave it clear to display the total number of either bits or bytes.
-
Click the Granularity drop-down and select the interval between data points in the results. Select either a predefined interval or Auto. Auto uses the highest applicable granularity for the best display and fastest load time based on the time span you select on the Time page.
SevOne NMS is optimized to receive flows every one minute. If you configure the router to send flows at a different interval, this setting enables you to view the report at the granularity that matches the router flow timeout setting. Again, we recommend against using anything other than one minute for the router flow cache timeout.
FlowFalcon Resolution Tab
-
Select the FlowFalcon Resolution tab.
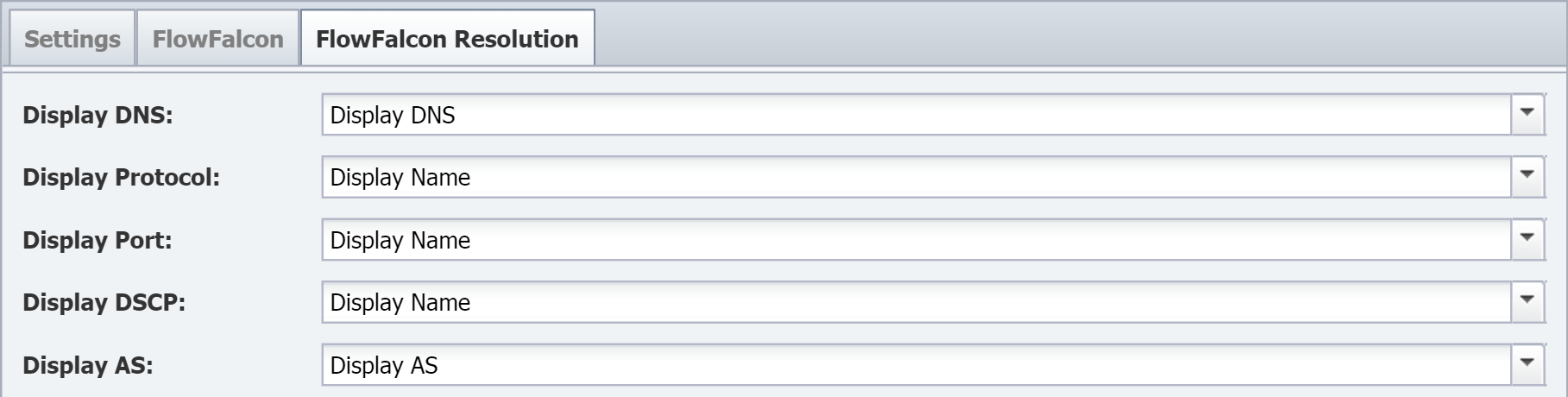
-
Click the Display DNS drop-down and select one of the following options.
-
Display IP - to display raw IP addresses.
-
Display DNS - to display resolved domain names when possible.
-
Display Both - to display IP addresses and resolved domain names.
-
-
Click the Display Protocol drop-down and select one of the following:
-
Display Number - to display raw protocol numbers.
-
Display Name - to display resolved protocol names.
-
Display Both - to display both numbers and resolved names.
-
-
Click the Display Port drop-down and select one of the following options.
-
Display Number - to display raw port numbers.
-
Display Name - to display resolved port names.
-
Display Both - to display both numbers and resolved names.
-
-
Click the Display DSCP drop-down and select one of the following options.
-
Display Number - to display DSCP port numbers.
-
Display Name - to display DSCP port names.
-
Display Both - to display both numbers and resolved names.
-
-
Click the Display AS drop-down and select one of the following options.
-
Display Number - to display AS port numbers.
-
Display AS - to display AS port names.
-
Display Both - to display both numbers and resolved names.
-
-
Click Next and continue to the next subsection, Filters.
Filters
The Filters wizard page lets you limit the results that appear in the attachment. Each filter contains one or more rules. Each filter rule applies to a specific flow field. A filter rule for a field not in the view is ignored. This enables you to define filters independently from views.
When you apply filters to an attachment that uses an aggregated view, the Remaining Traffic and Total Traffic numbers may appear inaccurate due to how the data is aggregated and stored in pre-calculated buckets. If you don't receive the expected number of results after you apply a filter to an aggregated view, increase the number of aggregated results to store for each write interval on the Cluster Manager.
Perform the following steps to configure filters.
-
Under Filters Selection, click the drop-down on the left and select the field that you want to define the filter on. Fields that are in the view you select appear first, followed by every other known field from flow data.
-
Click the second drop-down and select a comparison operator.
The Operator options include Mask and Subnet (as well as Not Mask and Not Subnet ). Selecting Mask means that flow data has to match in the manner of IP address subnet mask. Selecting Subnet means that flow data has to be from the network segment that you specify in the drop-down to the right (the drop-down will appear when you select Subnet). For information about defining network segments, please see the section Network Segment Manager.
-
In the Enter Value field, enter the value to base the filter on.
-
Click Add Filter to display the rule in the Current Filters list.
-
Click Next and continue to the next subsection, Visualizations.
Visualizations
The Visualizations page lets you define how you want to display your data. Perform the following steps to configure visualization settings.
Pie
-
Click
 to expand the section.
to expand the section.
-
Select the Display Logo check box to display a logo in the attachment.
-
The Display Minimum check box is selected by default. This indicates that the minimum data point will display in the legend.
Stacked Line
-
Click
 to expand the section.
to expand the section.
-
Select the Display Logo check box to display a logo in the attachment.
-
Select the Display Legend check box to display a legend in the attachment.
-
The Display Minimum check box becomes available when you select the check box for Display Legend (previous step). Select this check box to display the minimum data point in the legend.
-
Select the Display Time Span check box to display the time span in the attachment.
-
Select the CSV When Mailed check box to email the attachment in a .csv format to the recipients you define on the Report Properties Delivery tab . Leave it clear to email the table as a .pdf in the format that displays in the report.
Table
-
Click
 to expand the section.
to expand the section.
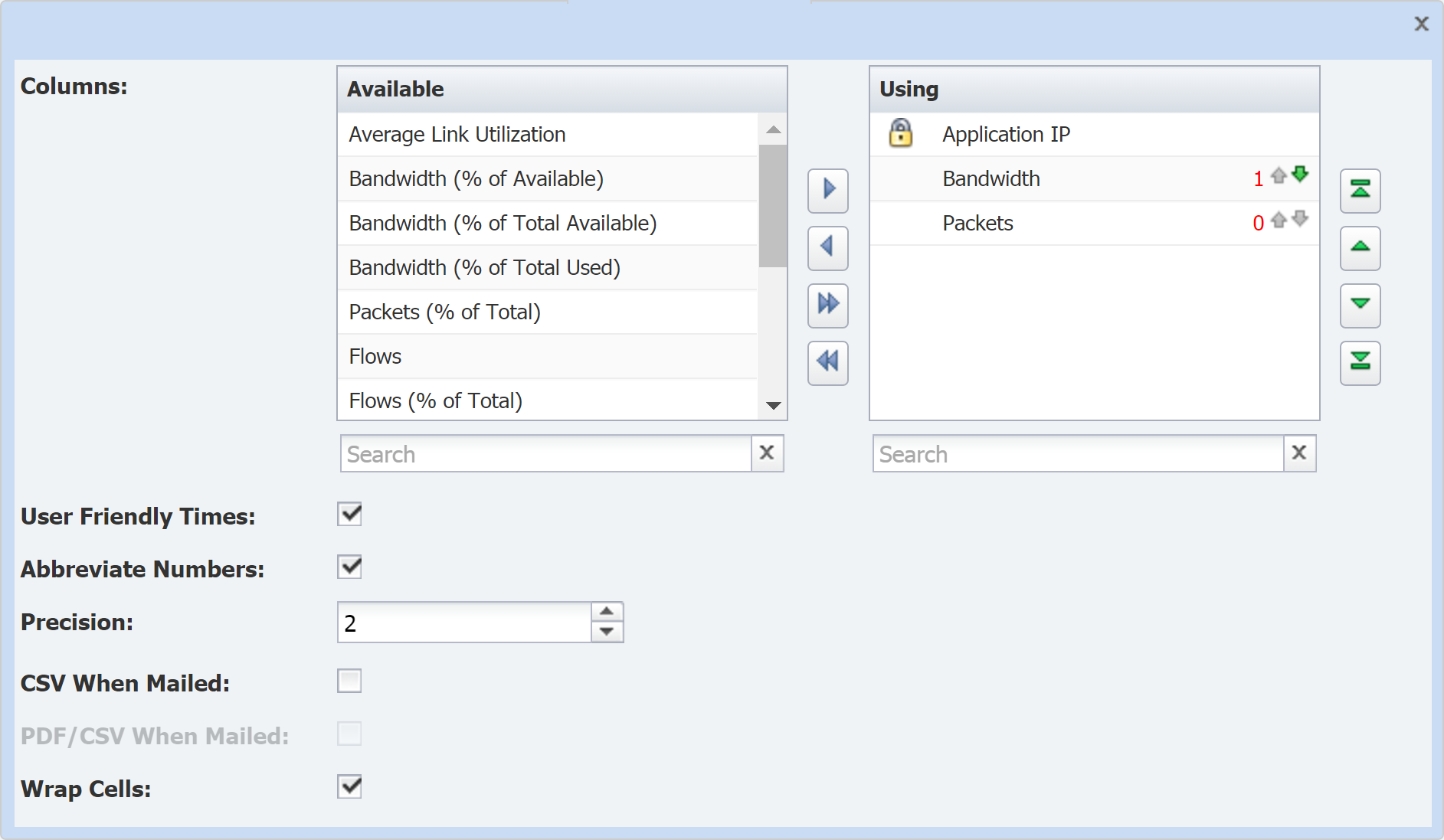
-
Next to Columns, under Available, select fields to display in the report attachment.
-
Click
 to move the fields to Using.
to move the fields to Using.
The column with the red number one ( 1 ) is the primary sort column. Data from this column displays in the Pie visualization and the Stacked Line visualization.
-
Select the User Friendly Times check box to use human-readable dates when you extract the report attachment data to .csv format. Leave it clear to use a UNIX time stamp in the .csv file. The UNIX time stamp allows for greater manipulation of the data.
-
Select the Abbreviate Numbers check box to abbreviate large numbers. If you leave the check box clear, the Precision field will appear, where you can enter the number of decimals to round the report results to.
-
Select the CSV When Mailed check box to email the report attachment as a .csv file to the recipients you specify on th e Report Properties Delivery ta b . Selecting this check box enables you to select the check box for PDF/CSV When Mailed. Select this check box to include the attachment as a .pdf file and convert it to a .csv file when it is emailed.
-
Select the Wrap Cells check box to wrap long text in a data row so that all text displays. Leave clear to display as much text as fits into the cell.
-
Click Next and continue to the next subsection, Summary.
Summary
The Summary page lets you view a summary of the report attachment definition. To make changes to any of the items in the Summary, click on the item. This will take you to the appropriate Report Attachment Wizard page, where you can change settings.
Report Results
If you don't need to make further changes to the Report Attachment Wizard settings, click Finish to display the report.
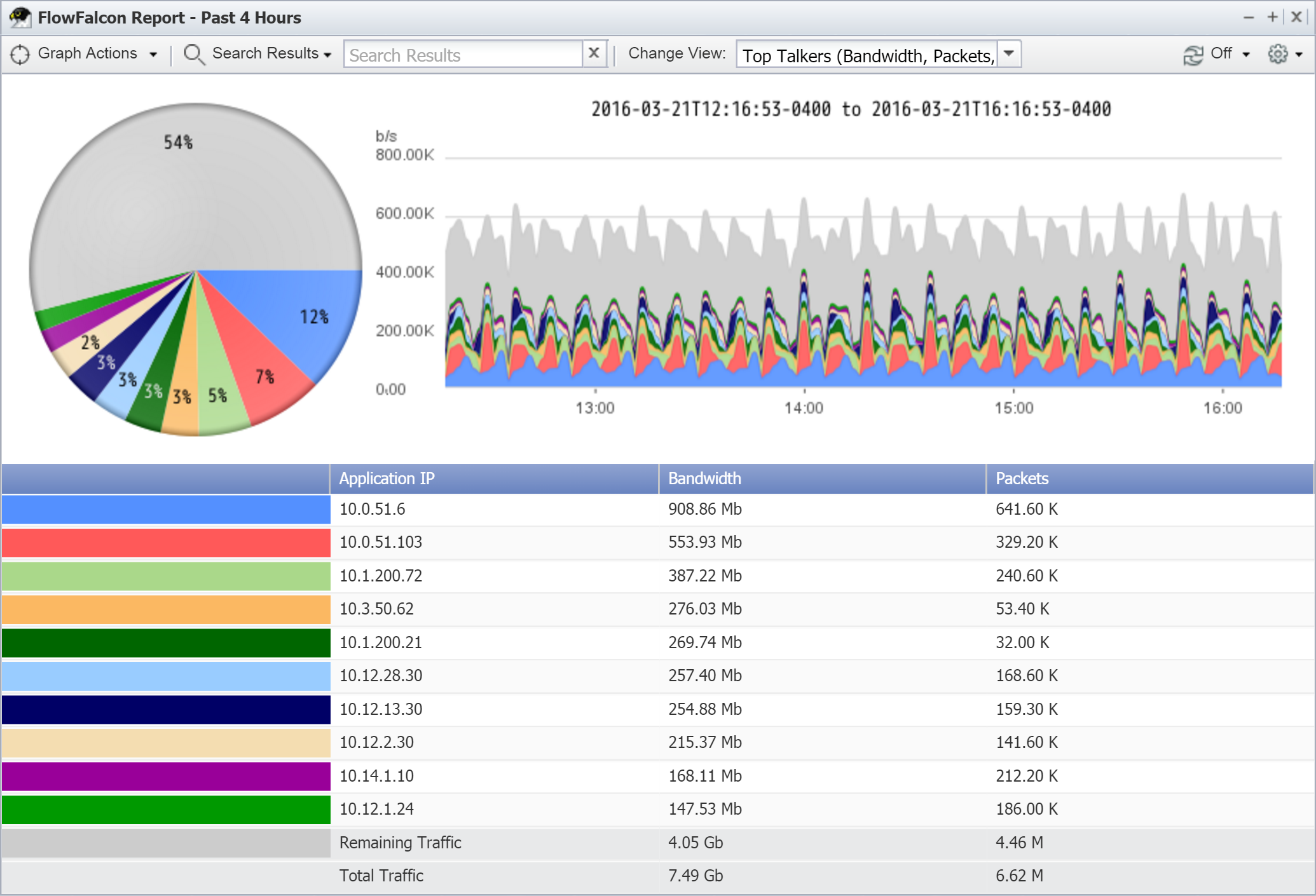
Create Reports Using FlowFalcon Reports
The classic FlowFalcon Reports page lets you to create individual FlowFalcon reports. In this section, we'll walk through the FlowFalcon Reports settings, which allow you to configure the report output according to your needs. Alternatively, you can quickly create a FlowFalcon report based on the page's default settings. We'll talk about that in the subsection The FlowFalcon Report - Getting Results.
You can get a FlowFalcon report instantly by using the default settings for the FlowFalcon Reports page. Afterwards, you can change report settings to tweak the report as needed. Perform the following steps to create a FlowFalcon report based on the default settings.
-
Under Resources, click Add Resource.
-
At the bottom of the page, click Get Results.
Once you've created your initial report, change settings as needed. The subsections below provide information about all the FlowFalcon Reports settings.
Perform the following steps to configure FlowFalcon Reports settings and create a report.
From the navigation bar, click Applications and select FlowFalcon Reports. Continue to the Resources subsection.
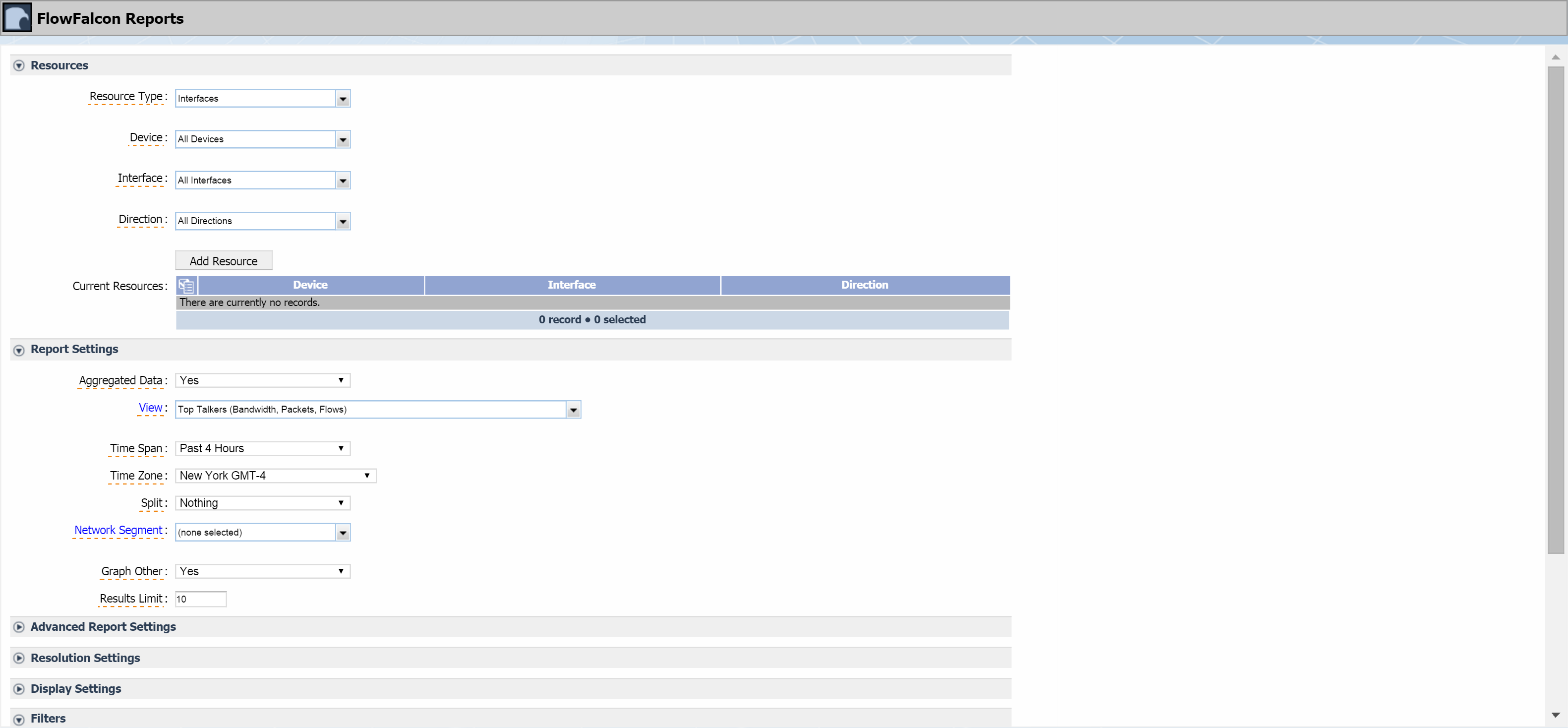
Resources
-
Click the Resource Type drop-down and select one of the following options:
-
Interfaces - to graph flow data from the interfaces you allow on the Flow Interface Manager. After selecting this option, perform the following actions.
-
Click the Device drop-down and select a device that flow data originates from. Select All Devices to graph flow data from all devices.
-
Click the Interface drop-down and select the interface that flow data originates from. Select All Interfaces to graph flow data from all interfaces on the device you select in the previous step.
-
Click the Direction drop-down and select whether to graph flow data that is Incoming, Outgoing, or for All Directions. Some flow sources provide only incoming data.
-
-
Device Groups - to graph flow data for a device group or device type. Click the Device Group drop-down and specify the device type(s) and/or device group(s).
-
Object Groups - to graph flow data for an object group. Click the Object Group drop-down and specify the object group(s).
-
-
Click Add Resource to add the specified resources to the Current Resources list.
-
Continue to the next subsection, Report Settings.
Report Settings
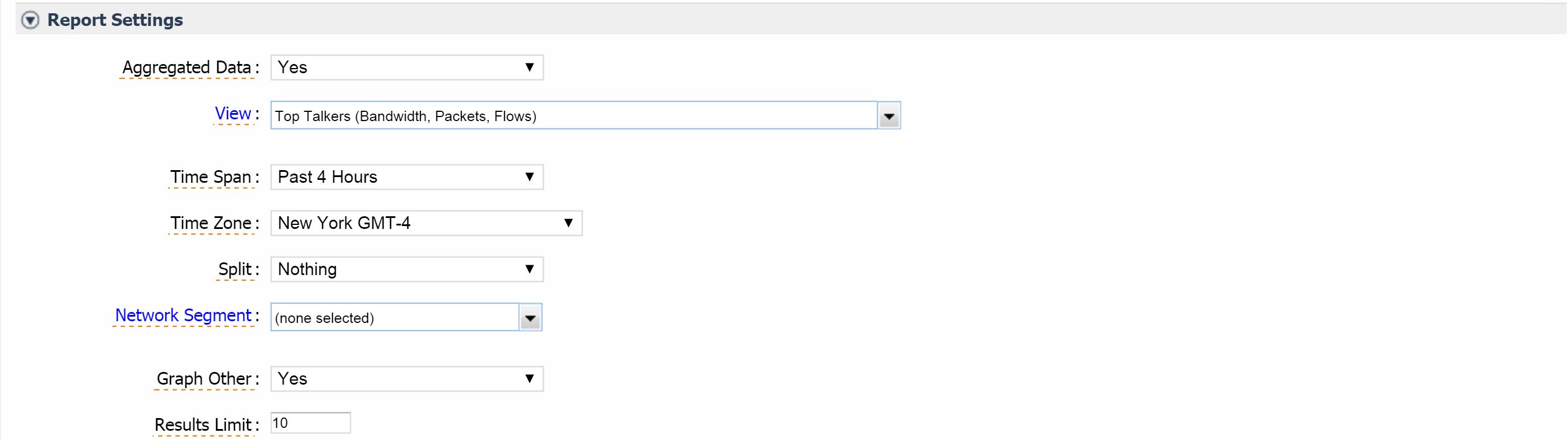
-
Click the Aggregated Data drop-down and select one of the following options.
-
Yes - to populate the View drop-down list with views that use aggregated flow data, which stores the most relevant flow data for faster report creation.
-
No - to populate the View drop-down list with views that use raw flow data to allow for more specificity in the result set. This option results in longer report execution times and less historical data availability.
-
-
Click the View drop-down and select a view. The selection of views is based on your input for the previous step.
Clicking on the View link will take you to the FlowFalcon View Editor. For information on creating/editing views using the FlowFalcon View Editor, see the section Manage FlowFalcon Views.
-
Click the Time Span drop-down and select one of the following options. The first three options below are customizable.
-
Past <X> Hours, Days, Weeks - to display data from <X> hours, days, or weeks ago until now.
-
Today - to display data from 12:00am today until now.
-
Yesterday - to display data from 12:00am yesterday until 12:00am today.
-
This Week, Month, Quarter - to display data from 12:00am on the first day of the week, month, or quarter until now.
-
Last Week, Month, Quarter - to display data from 12:00am on the first day of the last completed week, month, or quarter to 11:59pm on the last day of the last completed week, month, or quarter.
-
Custom - to display the Specify a Range pop-up, where you can define a custom time span.
-
-
Click the Time Zone drop-down and select a time zone.
-
Click the Split drop-down and select one of the following options.
-
Groups - to separate flow data by device group/device type or object group, depending on the resource you select. This option only appears when you select Device Groups or Object Groups in the Resources section.
-
Interfaces - to separate flow data into individual interfaces.
-
Nothing - to combine all results from the same direction across the same interface in order to allow for greater detail in the result set.
-
-
Click the Network Segment drop-down and select a network segment. The subnets for the segment you select are listed below it. This enables you to resolve IP addresses into segments and to roll up results from the same segment into a single result.
Clicking on the Network Segment link will take you to the Network Segment Manager. For information on managing network segments and subnets, see the Network Segment Manager section.
-
Click the Graph Other drop-down and select one of the following options.
-
Yes - to display the flow for the top <n> results individually in the pie chart and the stacked line graph. This also displays a Remaining Traffic graph item that groups the flow for the remaining flow sources that meet the filter criteria. You'll define the <n> results in the next step.
-
No - to display only the top <n> results in the in the pie chart and the stacked line graph. Remaining Traffic will still display in the table.
-
-
In the Results Limit field, enter the number of individual results to display in the table. The display includes the first 200 results to optimize browser performance. Export the report to a .csv format or to a .pdf format to view the full result set of more than 200 results. Filters enable you to narrow the scope of the request . You can also modify the Current Resources list (in the Resources section above) to limit the number of resources.
Advanced Report Settings
-
Click Advanced Report Settings to expand the section.
-
In the Data Columns field, select the check box for each data column to include in the report table. You'll need to select the check box for at least one data column. See the Table Columns section for a description of all columns.
-
Click the Sort Column drop-down and select the data column on which to sort the table in the FlowFalcon report. This drop-down list displays the data columns you select in the previous step. The data column you select in this step determines the data to display in the pie chart and the stacked line graph in the FlowFalcon report.
-
Click the Sort Order drop-down and select to sort data in either Ascending or Descending order.
Resolution Settings
-
Click Resolution Settings to expand the section.

-
Click the DNS drop-down and select one of the following options.
-
Display IP - to display raw IP addresses.
-
Display DNS - to display resolved domain names when possible.
-
Display Both - to display IP addresses and resolved domain names.
-
-
Click the Protocols drop-down and select one of the following:
-
Display Number - to display raw protocol numbers.
-
Display Name - to display resolved protocol names.
-
Display Both - to display both numbers and resolved names.
-
-
Click the Ports drop-down and select one of the following options.
-
Display Number - to display raw port numbers.
-
Display Name - to display resolved port names.
-
Display Both - to display both numbers and resolved names.
-
-
Click the DSCP drop-down and select one of the following options.
-
Display Number - to display DSCP port numbers.
-
Display Name - to display DSCP port names.
-
Display Both - to display both numbers and resolved names.
-
-
Click the AS drop-down and select one of the following options.
-
Display Number - to display AS port numbers.
-
Display AS - to display AS port names.
-
Display Both - to display both numbers and resolved names.
-
Display Settings
-
Click Display Settings to expand the section.

-
Click the Granularity drop-down and select one of the following options to specify the interval between data points in the results:
SevOne NMS is optimized to receive flows every one minute. If you configure the router to send flows at a different interval, this setting enables you to view the report at the granularity that matches the router flow timeout setting. Again, we recommend against using anything other than one minute for the router flow cache timeout.
-
Auto - to use the highest applicable granularity for the best display and fastest load time based on the time span you select in the Report Settings section.
-
A predefined interval - to select one of the predefined intervals, such as 1 minute, 5 minutes, 10 minutes, etc.
-
Custom - to specify a custom granularity. There's no limit as to what you enter here. However, if the granularity is too small for the time span, SevOne NMS will adjust the granularity.
-
-
Click the Preferred Units drop-down and select either Bits for network-oriented data or Bytes for server-oriented data.
-
Click the Display as Rates drop-down and select one of the following options:
-
Yes - to display the results as bits or bytes per second.
-
No - to display the total number of bits or bytes.
-
Filters
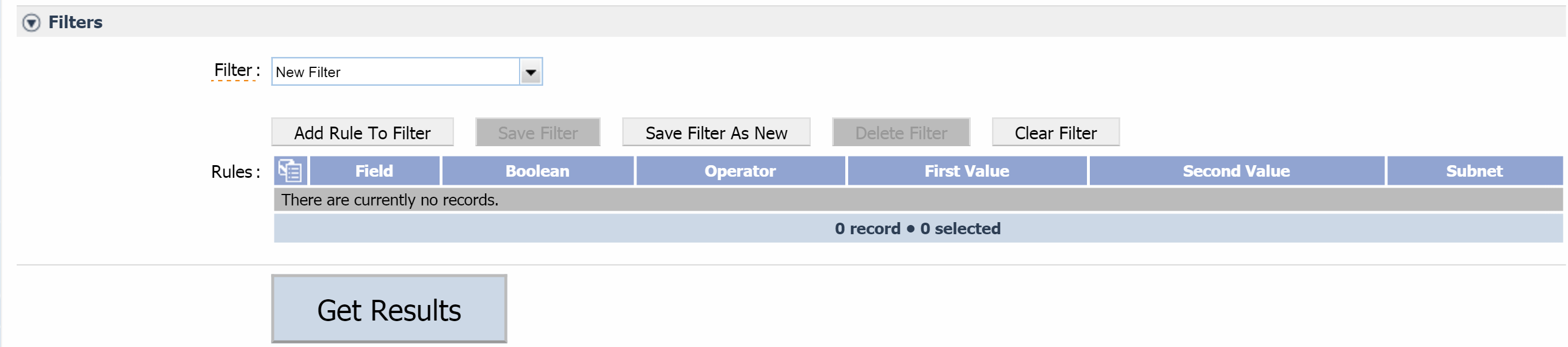
-
Click the Filter drop-down and select a filter to copy. To create a new filter, select New Filter.
-
Just below that, click Add Rule to Filter to display the Add a new rule to the filter pop-up. Perform the following actions to configure the rule.
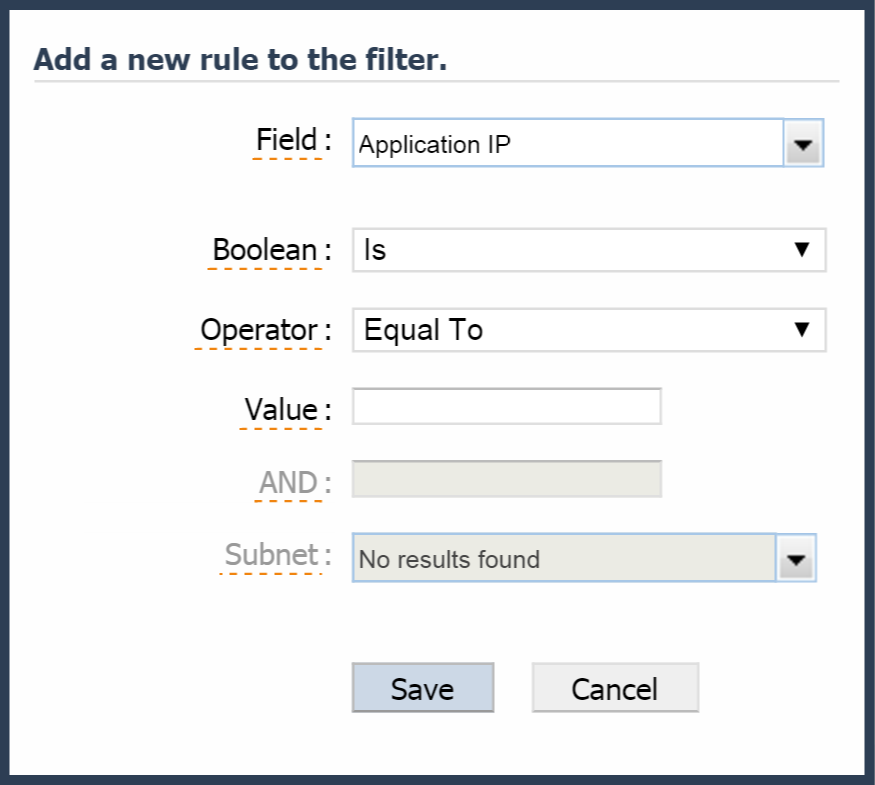
-
Click the Field drop-down and select the field to apply the rule to. The fields from the view you select (under Report Settings) appear first in the list, followed by every known field from the flow data.
-
Click the Boolean drop-down and select Is to define the rule with an Is Boolean operator or select Is Not to define the rule with an Is Not Boolean operator.
-
Click the Operator drop-down and select a comparison operator.
Depending on the field you selected for Field, the Operator options may include Mask and Subnet (in addition to Equal To, Greater Than, Less Than, and Between). Select Mask to report on flow data that needs to match in the manner of IP address subnet masking. Select Subnet to report on flow data that needs to be from the subnet you select from the Network Segment drop-down. The Network Segment drop-down becomes available when you select Subnet as the operator. For information about defining network segments, please see the section Network Segment Manager.
-
In the Value field, enter the value to filter data data on.
-
In the AND field, enter the second value in a value range if applicable.
-
If applicable, click the Subnet drop-down and select a subnet.
-
Click Save to save the rule.
-
-
Perform one of the following actions:
-
Click Save to save changes to an existing filter.
-
Click Save Filter as New to save a new filter. A pop-up will prompt you to name the new filter. After providing a filter name, click Save on the pop-up.
-
The FlowFalcon Report - Getting Results
Once you have configured settings for each setting of the FlowFalcon Reports page, click Get Results to view the FlowFalcon report.
FlowFalcon Reports: Report Interactions
In this section, we're going to look at the FlowFalcon report that you created in the last section, using the FlowFalcon Reports page. The FlowFalcon report displays a pie chart, a stacked line graph, and a table. The pie chart and the stacked line graph display up to 16 colors to represent the top 16 results for the data you select as the Sort Column in the Advanced Report Settings section on the FlowFalcon Reports page. The table displays up to 200 results. You can detach the report to a .csv format or .pdf format to display more than 200 results.
The following subsections provide instructions for manipulating and navigating the report from the FlowFalcon Reports page to display the exact data you need.
Flow Direction Explanation
Depending on the view that you select, you may see  and
and  in the report table. These appear if the selected view provides flow direction. The source port and the destination port are evaluated. The low port (non-zero) is considered the Application and the high port is considered the Client. The IP addresses follow the port numbers.
in the report table. These appear if the selected view provides flow direction. The source port and the destination port are evaluated. The low port (non-zero) is considered the Application and the high port is considered the Client. The IP addresses follow the port numbers.
For a flow: Source 1.1.1.1 port 34333 to destination 2.2.2.2 port 80.
When you create a report that uses the source and destination, the traffic for both directions of a conversation pair displays the hosts in both columns. In this case, you need to add up the total bandwidth in your head.
|
Source IP |
Source Port |
Destination IP |
Destination Port |
Bandwidth |
|
1.1.1.1 |
34333 |
2.2.2.2 |
80 |
500 MB |
|
2.2.2.2 |
80 |
1.1.1.1 |
34333 |
70 MB |
When you create a report that uses the Application field and the Client field, the host appears in a single column, which enables better aggregations of conversations. 80 becomes the Application port because it's the lower port number, and 34333 becomes the Client port. With the Application field and the Client field, the same report appears as follows. Here, the total bandwidth appears.
|
Application IP |
Application Port |
Client IP |
Client Port |
Bandwidth |
|
2.2.2.2 |
80 |
1.1.1.1 |
34333 |
570 MB |
You can also add the Application Direction field to display each direction of the conversation.
|
Application IP |
Application Port |
Application Direction |
Client IP |
Client Port |
Bandwidth |
|
2.2.2.2 |
80 |
|
1.1.1.1 |
34333 |
500 MB |
|
2.2.2.2 |
80 |
|
1.1.1.1 |
34333 |
70 MB |
Detach FlowFalcon Reports
When you create a report, the FlowFalcon Reports title bar at the top of the page displays four icons. By clicking on any of these icons, you can export a FlowFalcon report.

The following are options for exporting a FlowFalcon report.
-
 - exports all granular data points in the graph to a .csv format.
- exports all granular data points in the graph to a .csv format. -
 - exports the data summary data from the table to a .csv format.
- exports the data summary data from the table to a .csv format. -
 - exports the report to a .pdf format.
- exports the report to a .pdf format. -
 - adds the FlowFalcon report as an attachment in a report on a new browser tab. You can modify reports to add other attachments and you can save reports to the Report Manager.
- adds the FlowFalcon report as an attachment in a report on a new browser tab. You can modify reports to add other attachments and you can save reports to the Report Manager.
Remaining Traffic, Total Traffic, and FlowFalcon Flow Calculation
Remaining Traffic and Total Traffic
At the bottom of the the FlowFalcon report table, you'll see the rows for Remaining Traffic and Total Traffic.
-
The Remaining Traffic row displays the total of all interfaces that aren't part of the top <n> results (where <n> is the number you enter in the Results Limit field in the Report Settings section). If there are fewer results than the number you enter in the Report Settings section, the Remaining Traffic row won't appear.
-
The Total Traffic row displays the total of all interfaces in the report, regardless of whether the sources appear listed individually.
The Graph Other setting in the Report Settings section enables you to include the remaining traffic in the pie chart and stacked line graph. Click the Graph Other drop-down and select Yes to display a grey slice in the pie graph and a grey line in the stacked line chart to represent remaining traffic.
Run a FlowFalcon report that contains 100 results. In the Report Settings section, Graph Other is set to No and Results Limit is set to 100. The report displays the first ten results in the pie chart and the stacked line graph and the first 100 results in the table. The table contains a row for Remaining Traffic after the 100th result. Change the Graph Other setting to Yes and click Get Results. The graph updates to display the same data as before but now with a new dark grey pie slice and a stack graph row to represent the 90 unselected rows and the remaining traffic.
Working with v5 NetFlow
FlowFalcon reports depict the total rate of flows for each device/interface/direction after duplicating flows that lack directional information. NetFlow v5 only exports information about the incoming interface, so SevOne NMS duplicates the flow statistics for v5 NetFlow to enable you to run reports for outgoing flows on devices that use v5 NetFlow. If your network only uses v5 NetFlow, the FlowFalcon report flow rate should be double the actual rate of flows that arrive at the collector. Cluster Manager > Cluster Settings enable you to simulate missing egress and missing ingress flows for other flow technologies. The flow rate in FlowFalcon reports is different from the flow rate that displays on the Flow Interface Manager that uses a different calculation for flow data.
Table Columns
When you select Nothing for the Split field (in the Report Settings section), some column definitions change. The following table provides a rundown of those changes.
|
Data Columns |
||
|
Column Name |
Split Interfaces/Split Groups |
Split Nothing |
|
Average Link Utilization |
Bandwidth divided by the total bandwidth available for that record (same as "% of Available"). |
Bandwidth used divided by the number of records rolled up into that record. |
|
Bandwidth |
Total amount of traffic. |
Total amount of traffic. |
|
Bandwidth (% of Available) |
Bandwidth divided by the total bandwidth available for that record. |
Bandwidth divided by the total bandwidth available for all records rolled up into that record. |
|
Bandwidth (% of Total Available) |
Bandwidth divided by the total bandwidth available for all records with the same unique field set. |
Bandwidth divided by the total bandwidth available for all records rolled up into that record. (When rolled up, this statistic is the same as "% of Available" rolled up.) |
|
Bandwidth (% of Total Used) |
Bandwidth divided by the total bandwidth used for all records with the same unique field set. |
Bandwidth divided by the total bandwidth used in the entire report. |
|
Flows |
Total number of flows. |
Total number of flows. |
|
Flows (% of Total) |
Flows divided by the total number of flows in the report. |
Flows divided by the total number of flows in the entire report. |
|
Multicast Average Link Utilization |
Bandwidth divided by the total bandwidth available for that record (Same as "% of Available"). |
Bandwidth used divided by the number of records rolled up into that record. |
|
Multicast Bandwidth |
Total amount of traffic. |
Total amount of traffic. |
|
Multicast Bandwidth (% of Available) |
Bandwidth divided by the total bandwidth available for that record. |
Bandwidth divided by the total bandwidth available for all records rolled up into that record. |
|
Multicast Bandwidth (% of Total Available) |
Bandwidth divided by the total bandwidth available for all records with the same unique field set. |
Bandwidth divided by the total bandwidth available for all records rolled up. (When rolled up, same as "% of Available" rolled up.) |
|
Multicast Bandwidth (% of Total Used) |
Bandwidth divided by the total bandwidth used for all records with the same unique field set. |
Bandwidth divided by the total bandwidth used in the entire report. |
|
Multicast Packets |
Total number of packets. |
Total number of packets. |
|
Multicast Packets (% of Total) |
Packets divided by the total number of packets in the entire report. |
Packets divided by the total number of packets in the entire report. |
|
Packets |
Total number of packets. |
Total number of packets. |
|
Packets (% of Total) |
Packets divided by the total number of packets in the entire report. |
Packets divided by the total number of packets in the entire report. |
FlowFalcon Report Views
SevOne NMS comes with a list of FlowFalcon report views so that you can run common flow reports right out of the box. The default view is Top Talkers. There are two categories of FlowFalcon report views:
-
Aggregation Disabled views use raw flow data to allow for more specificity in the resu lt set at the trade off of longer report execution times and less historical data availability. You can choose to run each aggregated view in the granular mode.
-
Aggregation Enabled views use aggregated flow data to present the most relevant flow data for faster report creation. Your SevOne appliance hardware determines the maximum number of aggregated views
The following table provides a list of the FlowFalcon views included with SevOne NMS along with descriptions.
|
FlowFalcon View Name |
Included Flow Template Fields |
|
AGGREGATION DISABLED |
|
|
Application Reports |
|
|
Top Applications (Total Delay, Application Delay, Network Delay) |
Total Delay, Application Delay, Network Delay, Bandwidth, Packets, Application Port |
|
Top Clients with Applications |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Client IP, Protocol, Application Port |
|
Top Clients with Client Applications |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Client IP, Protocol, Client Port |
|
Top Conversations with Application |
Total Delay, Application Delay, Network Delay, Bandwidth, Packets, Application IP, Client IP, Application Port |
|
Top Conversations with Application and Direction |
Total Delay, Application Delay, Network Delay, Bandwidth, Packets, Application IP, Application Direction, Client IP, Application Port |
|
Top Flows |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Client IP, Protocol, Application Port, Client Port |
|
Top Flows and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Direction, Client IP, Protocol, Application Port, Client Port |
|
Top Flows with Next Hop |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Client IP, Next Hop IP, Protocol, Application Port, Client Port |
|
Top Flows with Next Hop and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Direction, Client IP, Next Hop IP, Protocol, Application Port, Client Port |
|
Top Next Hops with Applications |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Next Hop IP, Protocol, Application Port |
|
Top Next Hops with Client Applications |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Next Hop IP, Protocol, Client Port |
|
Top Talkers with Protocol and Applications |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Protocol, Application Port |
|
Top Talkers with Protocol and Client Applications |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Protocol, Client Port |
|
IP Reports |
|
|
Top Clients (Bandwidth, Packets, Flows) |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Client IP |
|
Top Clients (Total Delay, Application Delay, Network Delay) |
Total Delay, Application Delay, Network Delay, Bandwidth, Packets, Client IP |
|
Top Clients with Next Hop |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Client IP, Next Hop IP |
|
Top Conversations (Bandwidth, Packets, Flows) |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Client IP |
|
Top Conversations (Total Delay, Application Delay, Network Delay) |
Total Delay, Application Delay, Network Delay, Bandwidth, Packets, Application IP, Client IP |
|
Top Conversations and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Direction, Client IP |
|
Top Conversations with Direction |
Total Delay, Application Delay, Network Delay, Bandwidth, Packets, Application IP, Application Direction, Client IP |
|
Top Conversations with Next Hop |
Bandwidth, Packets, Flows, Multicast Packets, Multicast, Bandwidth, Application IP, Client IP, Next Hop IP |
|
Top Conversations with Next Hop and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast, Bandwidth, Application IP, Application Direction, Client IP, Next Hop IP |
|
Top Next Hops |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Next Hop IP |
|
Top Talkers (Bandwidth, Packets, Flows) |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP |
|
Top Talkers (Total Delay, Application Delay, Network Delay) |
Total Delay, Application Delay, Network Delay, Bandwidth, Packets, Application Port |
|
Top Talkers with Applications |
Total Delay, Application Delay, Network Delay, Bandwidth, Packets, Application IP, Application Port |
|
Top Talkers with Next Hop |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Next Hop IP |
|
Medianet |
|
|
Top Media Destinations |
Bandwidth, Packets, Packet Loss, Interarrival Jitter, Round Trip Time, Destination IP, Destination Port |
|
Top Media Flows |
Bandwidth, Packets, Packet Loss, Interarrival Jitter, Round Trip Time, Source IP, Source Port, SSRC, Destination IP, Destination Port, DSCP |
|
Top Media Sources |
Bandwidth, Packets, Packet Loss, Interarrival Jitter, Round Trip Time, Source IP, Source Port |
|
Network Reports |
|
|
Top Destination AS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, BGP Destination AS Number |
|
Top Destination Mask |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Destination Prefix |
|
Top Source AS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, BGP Source AS Number |
|
Top Source Mask |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Source Prefix |
|
Top Talkers AS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, BGP Source AS Number, BGP Destination AS Number |
|
Protocol Reports |
|
|
Top Applications (Bandwidth, Packets, Flows) |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application Port |
|
Top Applications (Bi-directional) |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Protocol, Application Port, Client Port |
|
Top Applications with Protocol |
Flows, Bandwidth, Packets, Multicast Packets, Multicast Bandwidth, Application Port, Protocol |
|
Top Client Applications |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Protocol, Client Port |
|
Top Protocols |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Protocol |
|
QoS Reports |
|
|
Top Applications with Next Hop and ToS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application Port, Next Hop IP, ToS |
|
Top Applications with ToS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Protocol, Application Port, ToS |
|
Top Client Applications with ToS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Protocol, Client Port, ToS |
|
Top Conversations with Application and ToS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Client IP, Application Port, ToS |
|
Top Conversations with Application and ToS and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Direction, Client IP, Application Port, ToS |
|
Top Flows with Next Hop and ToS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Client IP, Next Hop IP, Protocol, Application Port, Client Port, ToS |
|
Top Flows with Next Hop and ToS and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Direction, Client IP, Next Hop IP, Protocol, Application Port, Client Port, ToS |
|
Top Flows with ToS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Client IP, Protocol, Application Port, Client Port, ToS |
|
Top Flows with ToS and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Direction, Client IP, Protocol, Application Port, Client Port, ToS |
|
Top Talkers with Application and ToS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Protocol, Application Port, ToS |
|
Top Talkers with Client Application and ToS |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Protocol, Client Port, ToS |
|
Top Types of Service |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, ToS |
|
AGGREGATION ENABLED |
|
|
IP Reports |
|
|
Top Clients (Bandwidth, Packets, Flows) |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Client IP |
|
Top Conversations and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Direction, Client IP |
|
Top Talkers (Bandwidth, Packets, Flows) |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP |
|
Top Talkers with Applications |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Port |
|
Protocol Reports |
|
|
Top Applications (Bandwidth, Packets, Flows) |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application Port |
|
Top Applications with Protocol |
Flows, Bandwidth, Packets, Multicast Packets, Multicast Bandwidth, Application Port, Protocol |
|
QoS Reports |
|
|
Top Conversations with Application and ToS and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Direction, Client IP, Application Port, ToS |
|
Top Flows with Next Hop and ToS and Direction |
Bandwidth, Packets, Flows, Multicast Packets, Multicast Bandwidth, Application IP, Application Direction, Client IP, Next Hop IP, Protocol, Application Port, Client Port, ToS |
Flow Alerting
Network Operations teams are under increasing pressure to keep the network performing at its best. They need to leverage capabilities at their disposal to be able to reduce MTTR and solve performance problems faster. Flow alerting takes advantage of the performance information being collected from network routers, switches, firewalls, wireless LAN controllers, etc. via flow. As flow data is being processed, SevOne users will now be able to be notified based on flow alerting policies put in place by the SevOne administrator. They will be presented with threshold violations based on aggregated NetFlow tuples representing protocol, host, and conversation information that is seen traversing the network. With this information, they can monitor for conditions that warrant investigation, such as backup traffic occurring during business hours, multicast traffic rates that drop below the required bit rate, etc.
How It Works
Flow alerting takes advantage of the data aggregation process that occurs every minute by NetFlowd to look for threshold violations and trigger alerts. When the per-minute data aggregation occurs, all tuples are available to be used when looking for threshold violations–not just the top 100 in the view.
Looking at the diagram below, each minute, all raw flows are gathered to calculate the top 100 aggregation per interface per direction. At this time, we have all raw flow data available to us. As view aggregation occurs, we get a list of all tuples that align with that aggregation. The tuples are examined based on the flow alerting policies and thresholds defined by the SevOne admin. FlowFalcon filters can be applied to the policies and thresholds in order to further reduce and focus the data set on the desired set of tuples. Once the tuples have been filtered, trigger and clear conditions can be applied, along with a duration from 1 to 60 minutes. If a match occurs, then an alert is triggered and interested parties can be notified via SevOne Alerts dashboard, email, or SNMP Trap.
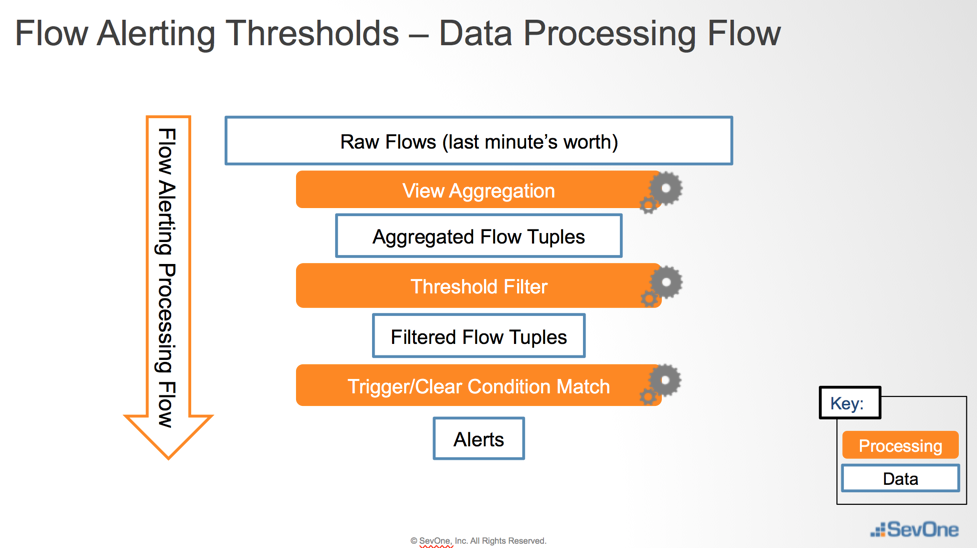
Benefits
Some of the benefits of flow alerting include:
-
You can configure alerting policies on flow data using any of the Aggregated View templates.
-
You can be alerted proactively based on information gleaned from flow data.
-
It doesn't require RTAGx or any additional object licenses.
Use Case
A network operations engineer wants to be alerted if backup traffic is seen during working hours (9 a.m. - 5 p.m., M-F) because this can cause network congestion when the network is needed most.
Required Information
Application port(s) that network backup systems use.
For our example, we let's say that our application port is 2222.
Alerting Strategy
-
Create a FlowFalcon filter using the legacy FlowFalcon interface that identifies the information you're interested in.
-
Create a flow alerting policy for all interfaces/directions.
-
Define your general settings.
-
Select device or object group containing your flow interfaces.
-
Select Aggregated View that contains application port information, such as Top Applications or Top Applications with Protocol.
-
Select the FlowFalcon filter you created earlier (for example, Backup Traffic).
-
Select Direction = Any (this will create thresholds for both Ingress and Egress traffic on the interface).
-
Configure Schedule to only include Business Hours, Monday - Friday.
-
-
Define your alert conditions.
-
Raise an alert when average Network Backup application port traffic is greater than 1 MB for a duration of 1 minute.
-
Clear an alert when average Network Backup application port traffic is less than 1 MB for a duration of 5 minutes.
-
-
Step-By-Step Instructions
-
Create a FlowFalcon filter using the legacy FlowFalcon interface that identifies the information you're interested in (Applications -> FlowFalcon Reports -> Filters section).
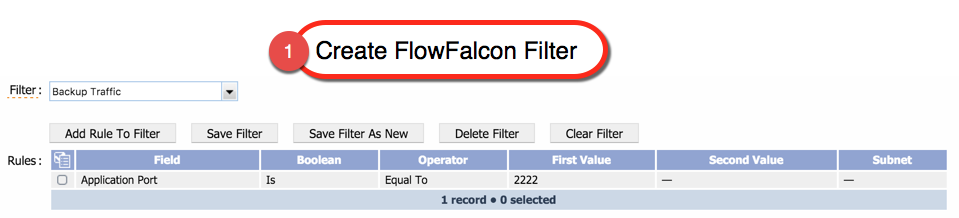
-
Create a flow alerting policy for all interfaces/directions, as described above.
-
Define your general settings.
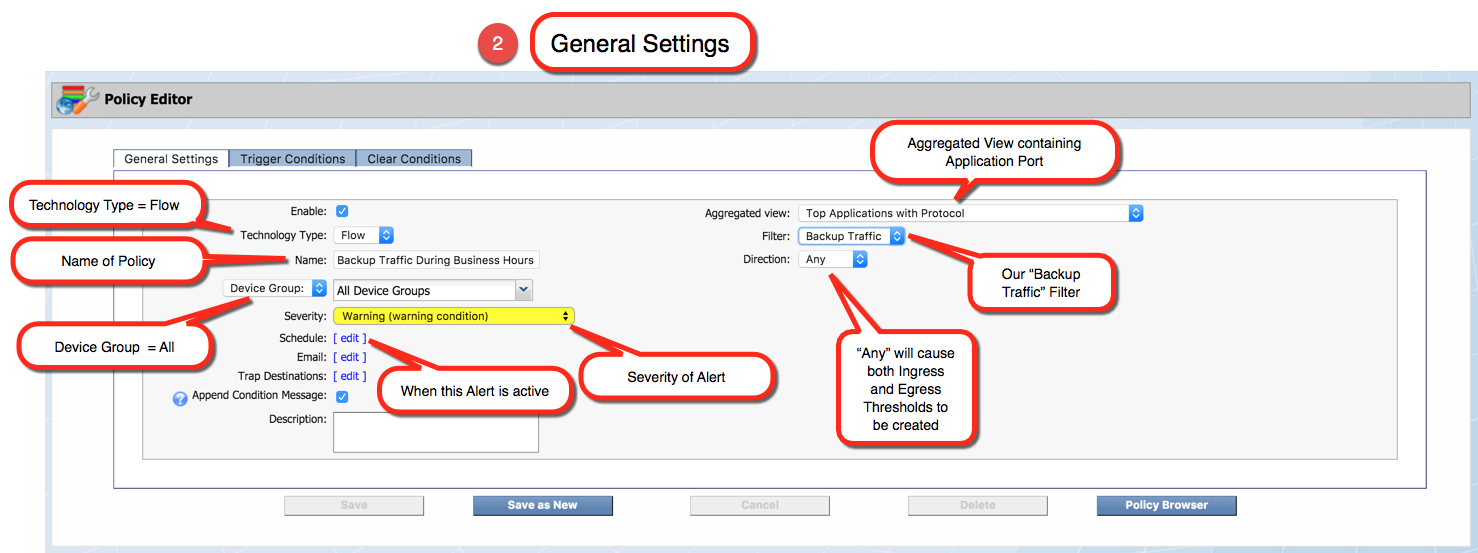
-
Configure Schedule to only include the hours of 9 to 5 (09:00 to 17:00), Monday - Friday.
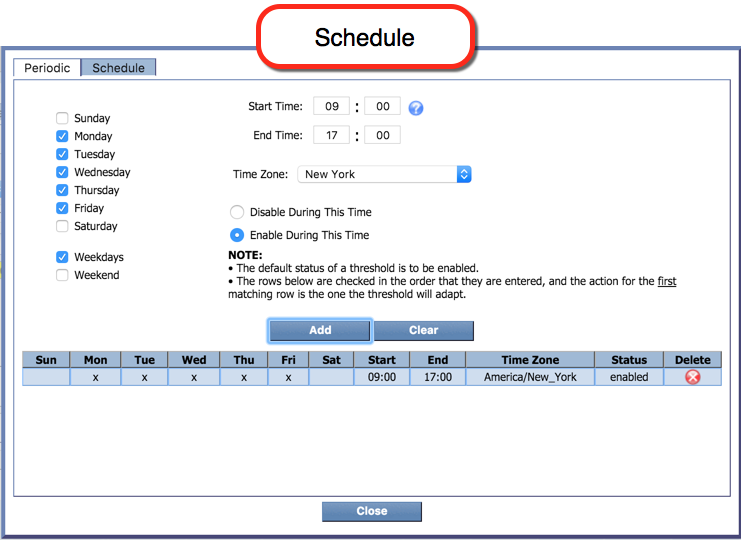
-
-
Define your alert conditions.
-
Raise an alert when average network backup application port traffic is greater than 1 MB for a duration of 1 minute.
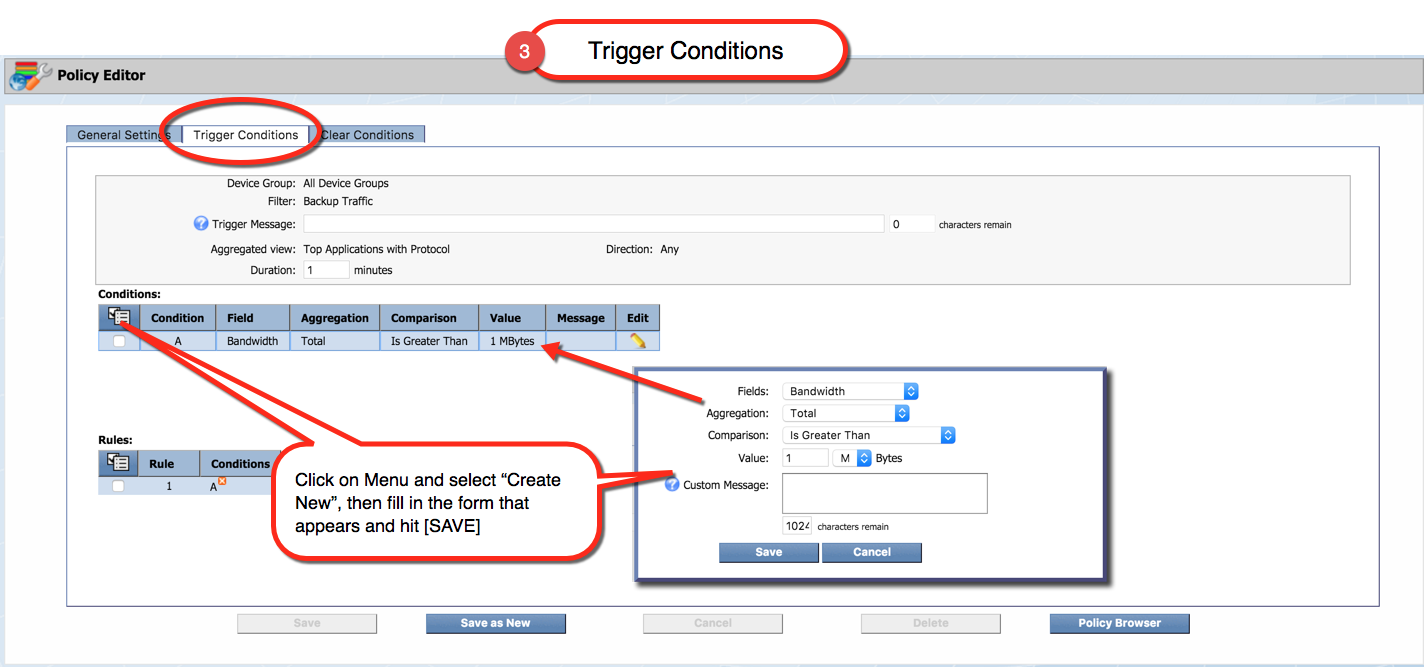
-
Clear an alert when average Network Backup application port traffic is less than 1 MB for a duration of 5 minutes.
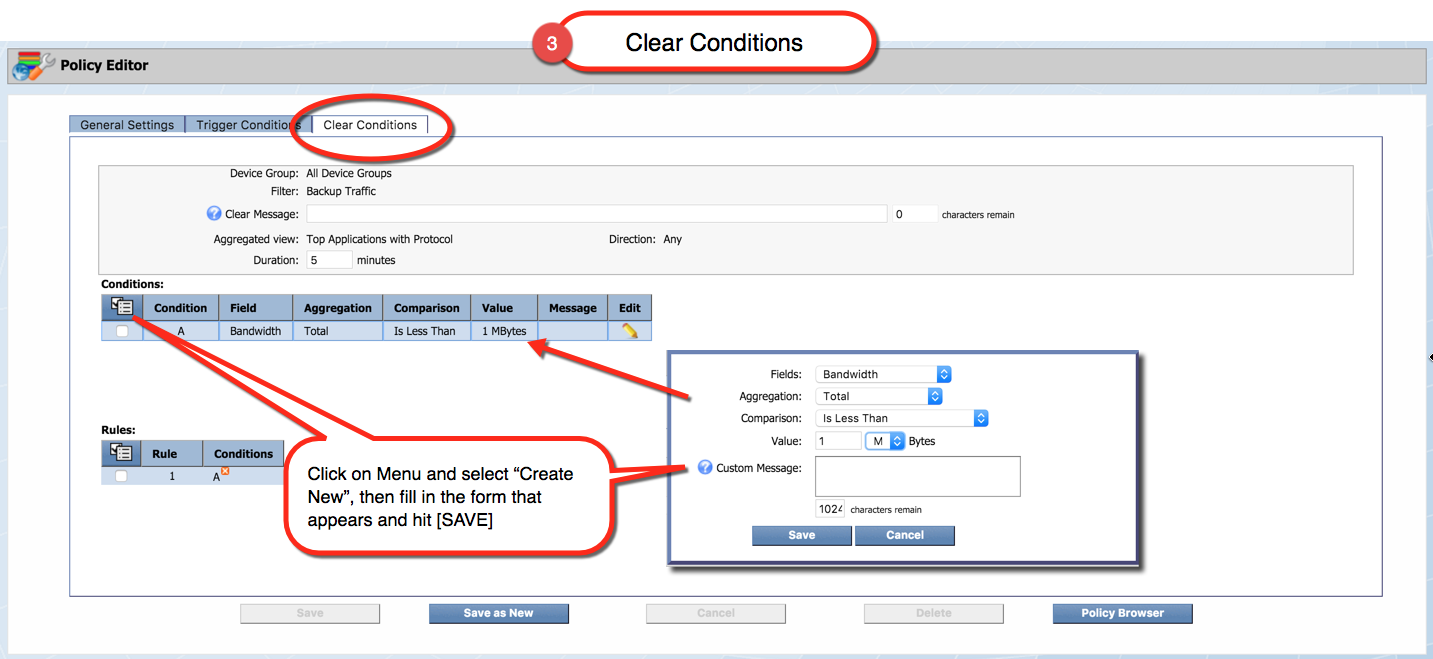
-
Click Save As New to save your policy.
-
-
Go to Events -> Alerts and check to see if you have an alert.
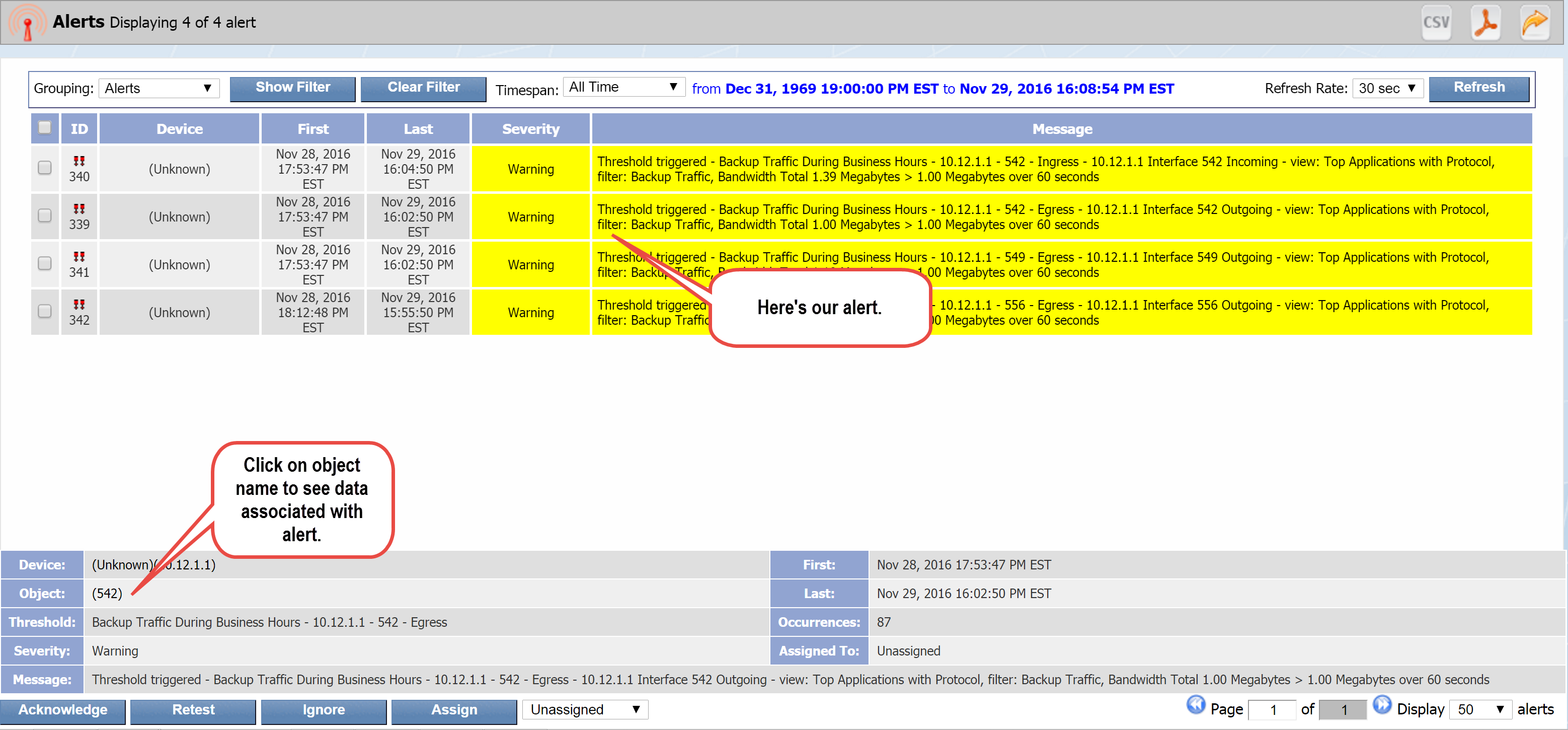
-
When you click on the object, it will bring provide the context of FlowFalcon interface to show you the data that caused your alert to trigger.
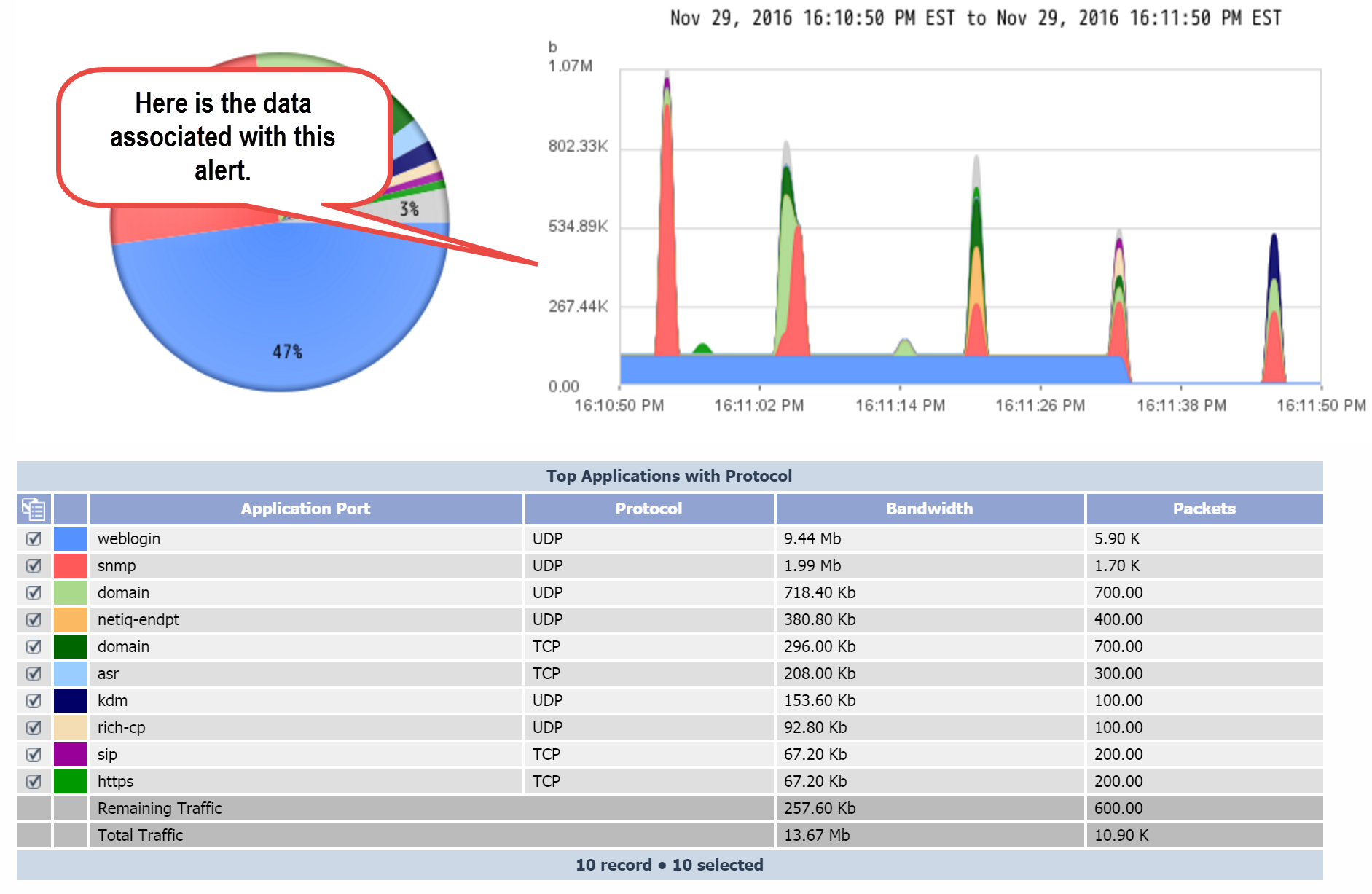
FlowDB
In the course of troubleshooting performance issues, sometimes network engineers and troubleshooters need to have visibility into all of the flow tuples related to the situation at hand. While aggregated views are great for showing you the top "things" for a particular view, their reports typically have a large "Other" area, which are the tuples that didn't make it into the Top 100 for the time period being analyzed. By utilizing raw flow data, the user has access to all tuples of interest–not just the Top 100.
Systems normally only have 10 aggregated views available. So what happens if the user needs to be presented with a different set of views that are not included in the 10 aggregated views? The user is able to create any number of non-aggregated raw views, allowing them to view the data and generate reports to meet any use case.
Creating non-aggregated views sounds great! What's the catch? While non-aggregated views afford the user great flexibility, the trade-off is in performance with regard to the amount of time it takes to generate a report using raw data vs. aggregated. Raw flows are massive in quantity, requiring the system to analyze a lot of data before it can generate the results in the form of a FlowFalcon report. Unfortunately, this can take a long time.
Benefits
The following are some of the benefits:
-
FlowDB enhances SevOne's ability to process large amounts of raw flow records via the introduction of a columnar LMDB "Lightning" database. It has shown to generate raw non-aggregated reports from 6x - 20x faster than in previous releases (results vary depending on number of interfaces, timespan, and filtering applied).
-
FlowDB changes the underlying data storage and retrieval method. The front-end workflow and options when running non-aggregated flow reports haven't changed. It will visually look the same to the user. However, the non-aggregated raw data reports will complete faster than before.
-
FlowDB uses LZ4 compression. It's always on and can't be turned off. This type of compression is high performing and reduces the storage requirement of raw data by two thirds. This means that you can store three times as much raw data as you were previously able to using the same amount of disk!
Use Case
A network analyst needs to see all flows originating from a particular host IP address during the last 15 minutes.
Step-By-Step Instructions
-
Run an aggregated view report using the view Top Talkers (Bandwidth, Packets, Flows) to identify hosts of interest. Then select one of the hosts.
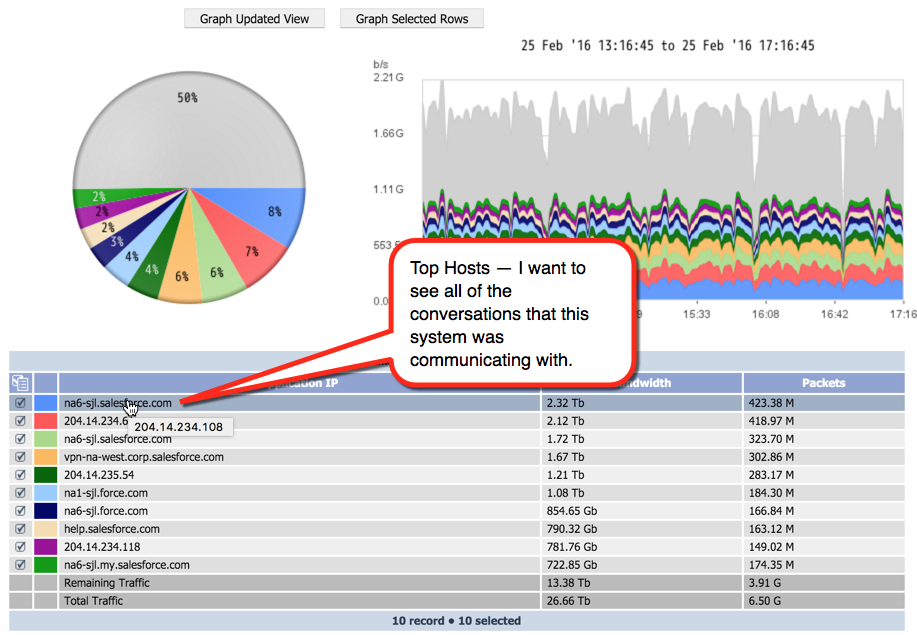
2. Run a non-aggregated view report using the view Top Conversations with Application and ToS and Direction. Use the following settings:
-
Aggregated Data = No
-
View = Top Conversations with Application and ToS and Direction
-
Time Span = Custom. Then configure the time span to show you the last 15 minutes.
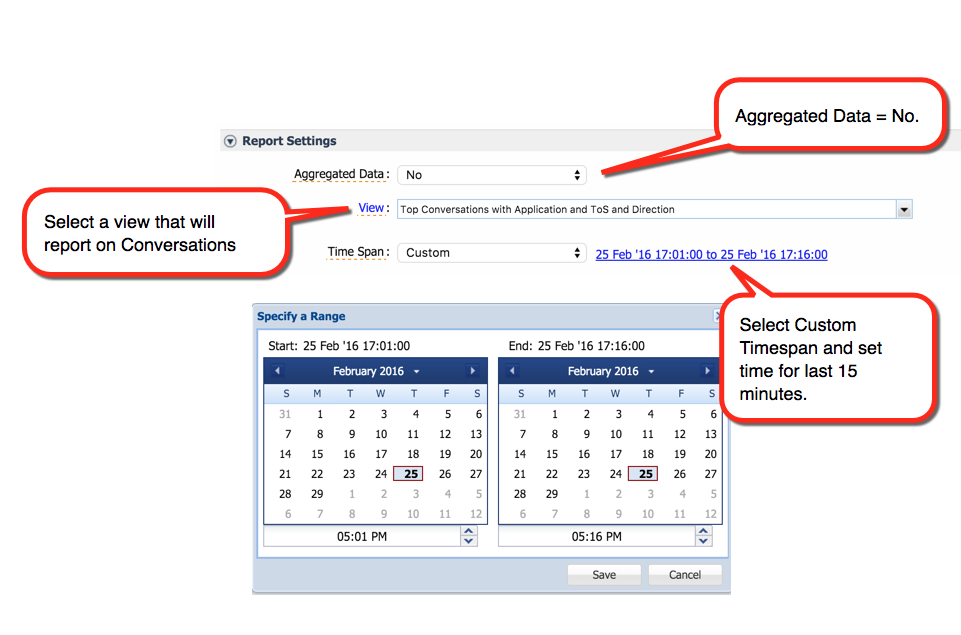
-
Create a filter with the Application IP configured to your host IP from the Top Hosts report that you ran in step 1.
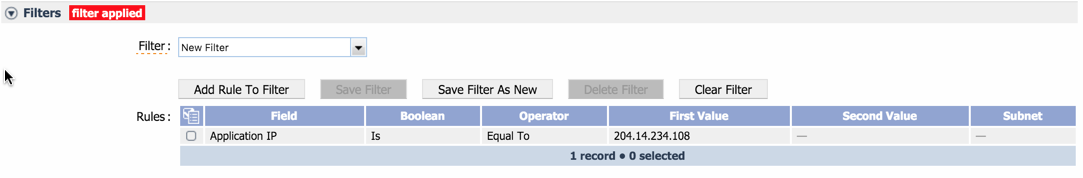
-
Click Get Results to run the report.
-
-
The screenshot below shows the resulting report. It contains conversations that occurred with our host. This report displays the top 10, but we can configure the system to display all results in the table.
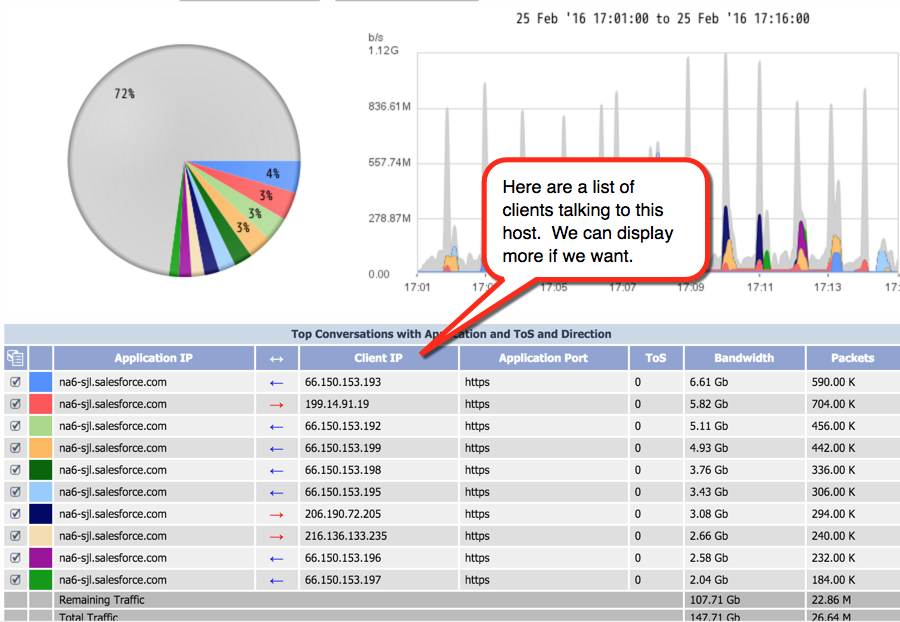
Troubleshooting
Flow data isn't displaying for my device
If flow data doesn't display for a device, you may need to check for traffic. Perform the following actions to confirm that SevOne NMS actually receives the data via tcpdump.
Log in to the box and run one of the following commands.
To show all incoming flow traffic to SevOne NMS:
tcpdump -i eth0 port 9996To show only flow traffic from a specific IP address.
tcpdump -i eth0 port 9996 | grep '<ip address in question>'If data comes into SevOne NMS, you should eventually see a message similar to the following example:
17:55:47.934113 IP <ip address question>.49359 > \ <SevOne>.9996: UDP, length 1464
If no data comes in from the IP address, there may be a routing issue.
Flow data is coming in, but nothing displays
If flow data comes in, but nothing displays, the version may be wrong.
Enter the following command to dump the first portions of the packets to the page.
tcpdump -XX -i eth0 port 9996Something similar to the following should display.
Example:
19:55:26.326485 IP <source>.52292 > <destination>.9996: UDP, length 1416
0x0000: 0030 482d 9e1b 0011 5d24 aec0 0800 4500 .0H-....]$....E.
0x0010: 05a4 f187 0000 fb11 ce64 0aff ff0c cc1b .........d......
0x0020: 2435 cc44 270c 0590 2b9f 0005 001d cada $5.Dâ...+.......
0x0030: 5584 45a3 f32e 0cd7 dd44 8682 7d8d 0001 U.E......D..}...
0x0040: 0000 aa94 ....
19:55:26.326609 IP <source>.58101 > <destination>.9996: UDP, length 1428
0x0000: 0030 482d 9e1b 0011 5d24 aec0 0800 4500 .0H-....]$....E.
0x0010: 05b0 b449 0000 f611 810a 0a00 8f98 cc1b ...I............
0x0020: 2435 e2f5 270c 059c fa38 0007 001b cdb8 $5..â....8......
0x0030: 2bdc 45a3 f32e 11a3 844e 29a1 03b4 0000 +.E......N).....
0x0040: 0000 0a33
In the above example, the first traffic is v5 and the second is v7, as indicated in the third row's sixth column. The last two digits in the column are the version.
The following is a visual aid to help find the version as indicated by the XX.
Example:
-::.----- IP <source>.----- > <destination>.9996: UDP, length ----
0x0000: ---- ---- ---- ---- ---- ---- ---- ---- ----------------
0x0010: ---- ---- ---- ---- ---- ---- ---- ---- ----------------
0x0020: ---- ---- ---- ---- ---- --XX ---- ---- ----------------
0x0030: ---- ---- ---- ---- ---- ---- ---- ---- ----------------
0x0040: ---- ----
Terms
|
Flow |
A series of packets that have the same source and destination IP address, source and destination port, transport protocol, etc. |
|
Flow Record |
A collection of information about a flow, including protocol, source and destination IP address, source and destination port, amount of data transmitted, date and time of transmission, etc. |


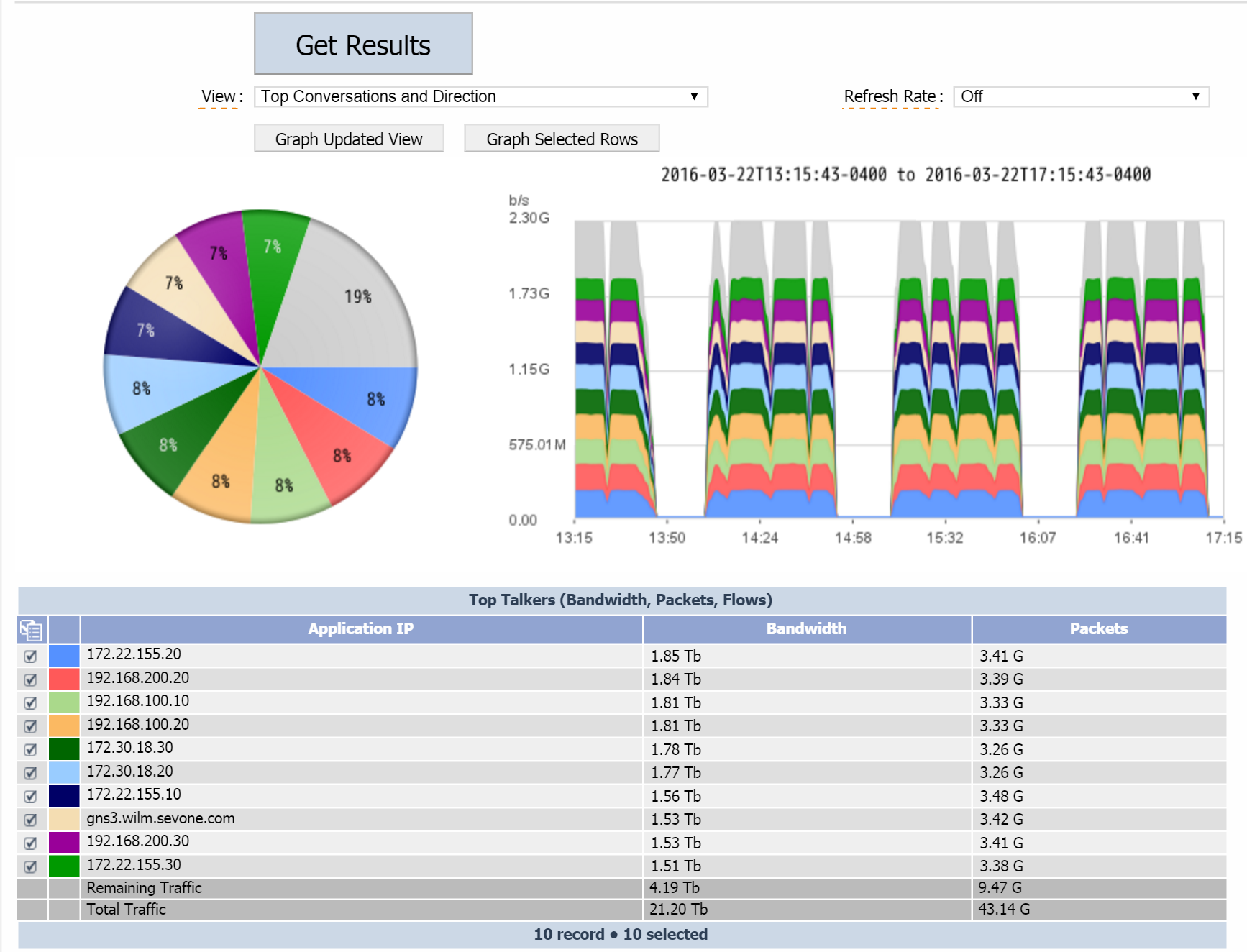
 and select Select None to clear the check boxes for all rows in the table.
and select Select None to clear the check boxes for all rows in the table.