
Table of Contents (Start)
- Topics
- Introducing SevOne
- Login
- Startup Wizard
- Dashboard
- Global Search - Advanced Search
- Report Manager
- Report Attachment Wizard
- Report Properties
- Report Interactions
- Instant Graphs
- TopN Reports
- Alerts
- Alert Archives
- Alert Summary
- Instant Status
- Status Map Manager
- Edit Maps
- View Maps
- FlowFalcon Reports
- NBAR Reports
- Logged Traps
- Unknown Traps
- Trap Event Editor
- Trap Destinations
- Trap Destination Associations
- Policy Browser
- Create and Edit Policies
- Threshold Browser
- Create and Edit Thresholds
- Probe Manager
- Discovery Manager
- Device Manager
- New Device
- Edit Device
- Object Manager
- High Frequency Poller
- Device Summary
- Device Mover
- Device Groups
- Object Groups
- Object Summary
- Object Rules
- VMware Browser
- Calculation Plugin
- Cisco ACI Plugin
- Database Manager
- Deferred Data Plugin
- DNS Plugin
- HTTP Plugin
- ICMP Plugin
- IP SLA Plugin
- JMX Plugin
- NAM
- NBAR Plugin
- Portshaker Plugin
- Process Plugin
- Proxy Ping Plugin
- SNMP Plugin
- VMware Plugin
- Web Status Plugin
- WMI Plugin
- xStats Plugin
- Indicator Type Maps
- Device Types
- Object Types
- Object Subtype Manager
- Calculation Editor
- xStats Source Manager
- User Role Manager
- User Manager
- Session Manager
- Authentication Settings
- Preferences
- Cluster Manager
- Maintenance Windows
- Processes and Logs
- Metadata Schema
- Baseline Manager
- FlowFalcon View Editor
- Map Flow Objects
- FlowFalcon Views
- Flow Rules
- Flow Interface Manager
- MPLS Flow Mapping
- Network Segment Manager
- Flow Protocols and Services
- xStats Log Viewer
- SNMP Walk
- SNMP OID Browser
- MIB Manager
- Work Hours
- Administrative Messages
- Enable Flow Technologies
- Enable JMX
- Enable NBAR
- Enable SNMP
- Enable Web Status
- Enable WMI
- IP SLA
- SNMP
- SevOne Data Bus
- Quality of Service
- Perl Regular Expressions
- Trap Revisions
- Integrate SevOne NMS With Other Applications
- Email Tips and Tricks
- SevOne NMS PHP Statistics
- SevOne NMS Usage Statistics
- Glossary and Concepts
- Map Flow Devices
- Trap v3 Receiver
- Guides
- SevOne Implementation Guide
- SevOne Best Practices Guide - Cluster, Peer, and HSA
- SevOne Installation Guide - Virtual Appliance
- SevOne NMS Installation Guide
- SevOne SAML Single Sign-On Setup Guide
- Access Control Quick Start Guide - SevOne NMS 5.7
- Data Miner Quick Start Guide - SevOne NMS 5.7
- Flow Quick Start Guide - SevOne NMS 5.7
- Group Aggregated Indicators Quick Start Guide - SevOne NMS 5.7
- IP SLA Quick Start Guide - SevOne NMS 5.7
- JMX Quick Start Guide - SevOne NMS 5.7
- LDAP Quick Start Guide - SevOne NMS 5.7
- Metadata Quick Start Guide - SevOne NMS 5.7
- RESTful API Quick Start Guide - SevOne NMS 5.7
- Self-monitoring Quick Start Guide - SevOne NMS 5.7
- SevOne NMS Admin Notifications Quick Start Guide - SevOne NMS 5.7
- SNMP Quick Start Guide - SevOne NMS 5.7
- Synthetic Indicator Types Quick Start Guide - SevOne NMS 5.7
- Topology Quick Start Guide - SevOne NMS 5.7
- VMware Quick Start Guide - SevOne NMS 5.7
- Web Status Quick Start Guide - SevOne NMS 5.7
- WMI Quick Start Guide - SevOne NMS 5.7
- xStats Quick Start Guide - SevOne NMS 5.7
LDAP Quick Start Guide - SevOne NMS 5.7
SevOne Documentation
All SevOne user documentation is available online from the SevOne Support customer portal.
Copyright © 2005-2020 SevOne Inc. All rights reserved worldwide.
All right, title, and interest in and to the software and documentation are and shall remain the exclusive property of SevOne and its respective licensors. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of SevOne.
In no event shall SevOne, its suppliers, nor its licensors be liable for any damages, whether arising in tort, contract, or any other legal theory even if SevOne has been advised of the possibility of such damages, and SevOne disclaims all warranties, conditions, or other terms, express or implied, statutory or otherwise, on software and documentation furnished hereunder including without limitation the warranties of design, merchantability, or fitness for a particular purpose, and noninfringement.
All SevOne marks identified or used on the SevOne website, as updated by SevOne from time to time, may be, or are, registered with the U.S. Patent and Trademark Office and may be registered or pending registration in other countries. All other trademarks or registered trademarks contained and/or mentioned herein are used for identification purposes only and may be trademarks or registered trademarks of their respective companies.
What's this LDAP I keep hearing about?
If you've attended any cocktail parties, you've probably heard the term LDAP tossed around. And if you're not already familiar with LDAP, you've likely wondered what all the buzz is about.
LDAP refers to the Lightweight Directory Access Protocol. It's a standards-based protocol used to query and modify directory services. This way, organizations can maintain centralized directories of users. Not only that, distributed applications can authenticate against those directories.
LDAP directories use a tree structure for storing information. This structure is known as a Directory Information Tree (DIT). The directory tree contains three main components:
-
Trunk
-
Branches
-
Leaves
The trunk is the directory root. It'll likely be named after your domain. For example, if your domain is hobgoblins.org, the root of your directory would be named dc=hobgoblins, dc=org. The branches of the trunk are organizational units. If your organization has multiple sites, you might have an organizational unit, or ou, for each site. For example, you could have one ou for California, another for Texas, and one more for Pennsylvania.
Just as an individual branch can have its own branches, an ou can have, or contain, its own ous. The ous mentioned above might each contain three subordinate ous: a Users ou, a Groups ou, and a Machines ou. These ous can also contain ous, but they don't have to. The Users ou, for instance, might just contain the users for that location. The actual user entries would be considered leaves because they can't contain any subordinate entries.
A few benefits of the tree structure are:
-
Increased ease of administration and maintenance
-
Flexible application of security policies and access controls
-
Scalability
-
Simplified resource sharing
Common systems that provide implementations of LDAP include Microsoft's ActiveDirectory, the open source OpenLDAP project, and the Oracle Internet Directory product line.
Will LDAP make me a better person?
No, but it's still pretty useful. A lot of organizations have standardized on LDAP-based directory platforms and would like to apply the user and group structures maintained in that directory within SevOne NMS. There are two main reasons for this integration:
-
Synchronization - You can incorporate existing user group or user role information into SevOne NMS with the Group Synchronization option. When you synchronize a group into SevOne NMS, the members of that group are automatically added to SevOne NMS. This saves you the trouble of manually adding users who already exist in your directory.
A user group in LDAP creates a user role in SevOne NMS. However, manually adding a user to that role may result in automatically removing the added user from that role and/or deleting it from SevOne NMS.
-
Authentication - You can set up SevOne NMS to accept authentication using existing passwords stored in your central directory.
So, by configuring LDAP in SevOne NMS, you're just managing user access and credentials in your LDAP instance without having to do it in SevOne NMS, too. What's more, with LDAP group synchronization, you can sync up an LDAP group into SevOne NMS as a user group or user role (user roles are included in SevOne NMS version 5.3 and higher). This automatically adds the LDAP group and all its users into SevOne NMS and eliminates the need to maintain user access.
This is closely related to a nifty concept known as single sign-on, which we'll talk about shortly.
A note on terminology.
LDAP likes to use the term User Groups. SevOne, on the other hand, prefers to say User Roles. This lines up with our implementation of Role-based Access Control in NMS version 5.3 and higher. Basically, these two concepts become the same thing after synchronization.
What should I expect to see with LDAP?
By configuring LDAP authentication, you enable single sign-on (also known as SSO). Single sign-on permits a user's network password to be shared between multiple resources. This means that users don't have to enter a separate set of credentials each time they log into an application, website, etc. that they're authorized to use.
One of the great selling points of single sign-on is efficiency. It eliminates the need for users to have multiple passwords. This, in turn, lessens the risk of users forgetting passwords or using wrong passwords. Users are happy because they spend less time reentering passwords, and IT folks are happy because they spend less time resetting passwords.
Is there anything I need before I get started?
For starters, you'll need to have an LDAP server up and running. Your LDAP administrator may want to create a specific group for SevOne NMS users. For example, the administrator might create a group called SevOne Users, which would contain existing users who will be working with SevOne NMS on a regular basis. You'll also need to have a few bits of information handy. Your LDAP administrator should be able provide you with any information you don't have already. Below is the breakdown of what you'll need.
LDAP Server
This can be either the host name or the IP address of the LDAP server. For example, imagine that you work for a company that sells okra-frying appliances. Your LDAP server might be at ldap.okrafryers.com, which has the IP address of 192.168.10.22. You could either use the host name ldap.okrafryers.com or the IP address 192.168.10.22.
Port
Which network port is your LDAP server on? The default port for LDAP traffic is port 389, but make sure to check with your LDAP administrator in case a different port is used. The LDAP server generally accepts clear text connections on port 389. For LDAP connections over SSL (LDAPS), you would typically use port 636.
Bind DN
The bind distinguished name, or bind DN, is the user name for authenticating to the LDAP server. The bind DN's authorizations also allow SevOne NMS to search the directory tree. A couple of examples of bind DNs are cn=guest and cn=users.
Bind Password
This is the password for the bind DN that you entered in the previous step. A password isn't required in LDAP version 3 (LDAPv3).
Base DN
The base distinguished name, or base DN, refers to the top level of the directory tree. This is the starting point for searches. For an Active Directory system, the format of the base DN is generally dc=example, dc=com. Imagine, for example, that you own a chain of stores where customers get made over to look like clowns. You've named your company Clown Makeovers, Inc., and you have a website at www.clownmakeovers.com, where customers can locate stores and schedule makeovers. Your base DN would be dc=clownmakeovers, dc=com.
User Attribute
This is the attribute that SevOne NMS will check to find user names. Active Directory generally uses sAMAccountName while other directories might use uid or cn.
Encryption
There are two options for securing the connection to your LDAP server: SSL and StartTLS.
Security Sockets Layer (SSL) is a security protocol used for establishing an encrypted connection between a client and server. Sometimes the term SSL is used interchangeably with TLS, which stands for Transport Layer Security. TLS is the successor of SSL. After SSL version 3 (SSLv3.0), the protocol became known as TLS, with the first version being TLS version 1 (TLSv1.0). SSL generally uses port 636. The use of SSL has been deprecated, with StartTLS being the preferred standard.
StartTLS isn't actually a protocol but rather a protocol command. As you might have guessed, the TLS in StartTLS refers to Transport Layer Security. When enabled, StartTLS sends a command to upgrade an existing plain text connection to an encrypted connection using SSL/TLS. StartTLS normally runs on port 389 and doesn't require using a separate port for SSL/TLS. This is because SSL/TLS is applied after the connection is made.
Your LDAP administrator should be able to tell you which option to use.
SSL/TLS Certificates
During LDAP configuration, you'll have the option to upload and ignore certificates.
-
Uploading Certificates. If your LDAP server's SSL/TLS certificates are signed by an unknown CA, you'll need to upload the certificates. This will enable SevOne NMS to authenticate to your LDAP server. Certificates need to be base64-encoded PEM files.
-
Ignoring Certificates. Ignoring certificates means that SevOne NMS will still allow the connection to your LDAP server but won't be able to validate the identity of the LDAP server. This is like standing behind your front door and saying, "I don't know if you are who you say you are, but come on in!"
If you change this setting, you must contact SevOne Support for it to properly take effect.
Configuration Steps
In this section, we'll cover the following topics.
-
Adding and editing LDAP servers
-
Testing LDAP server connections
-
Synchronizing directory groups
-
Adding a guest user
-
Specifying SSL/TLS certificate settings
-
Uploading a root certificate
LDAP User Authentication
On the User Authentication tab, you can add LDAP servers, synchronize groups, add a guest user, and configure certificate settings.
Any LDAP authenticated user who has the Must Change Password at Next Logon (or similar) setting on the LDAP server and has NOT changed said password will NOT be able to log on to SevOne NMS. Either disable this setting for the user on the LDAP server or ensure that LDAP users change their passwords elsewhere before attempting to log on SevOne NMS.
Add LDAP Server
Perform the following steps to add an LDAP server.
SevOne NMS maintains consistency between the remote LDAP server and the synced local users who have only an LDAP role. This means that when such a user is removed from the remote LDAP server, SevOne NMS also removes the corresponding local user.
-
From the navigation bar, click Administration and select Access Configuration, then Authentication Settings. On the left side of the page, the LDAP tab is selected by default.
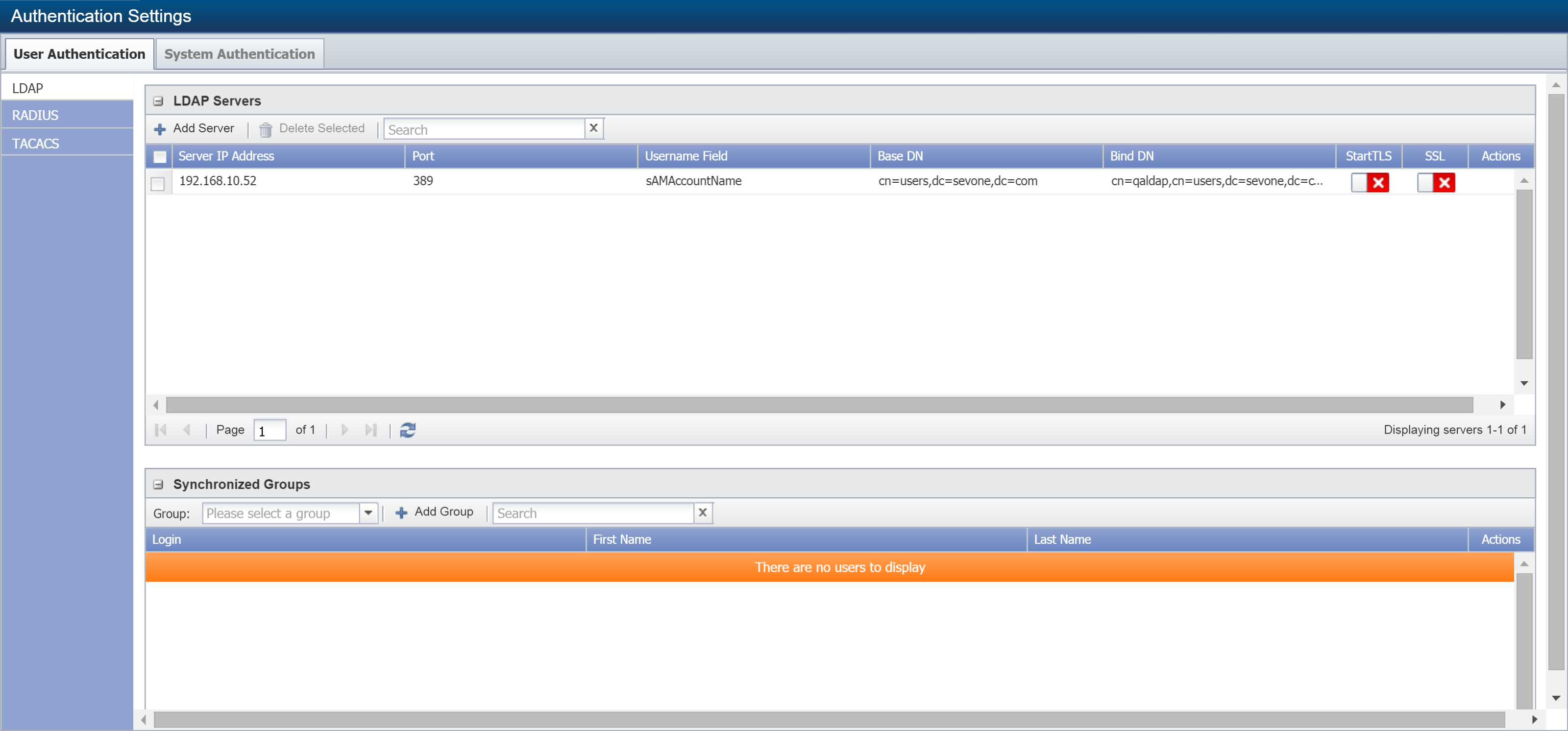
-
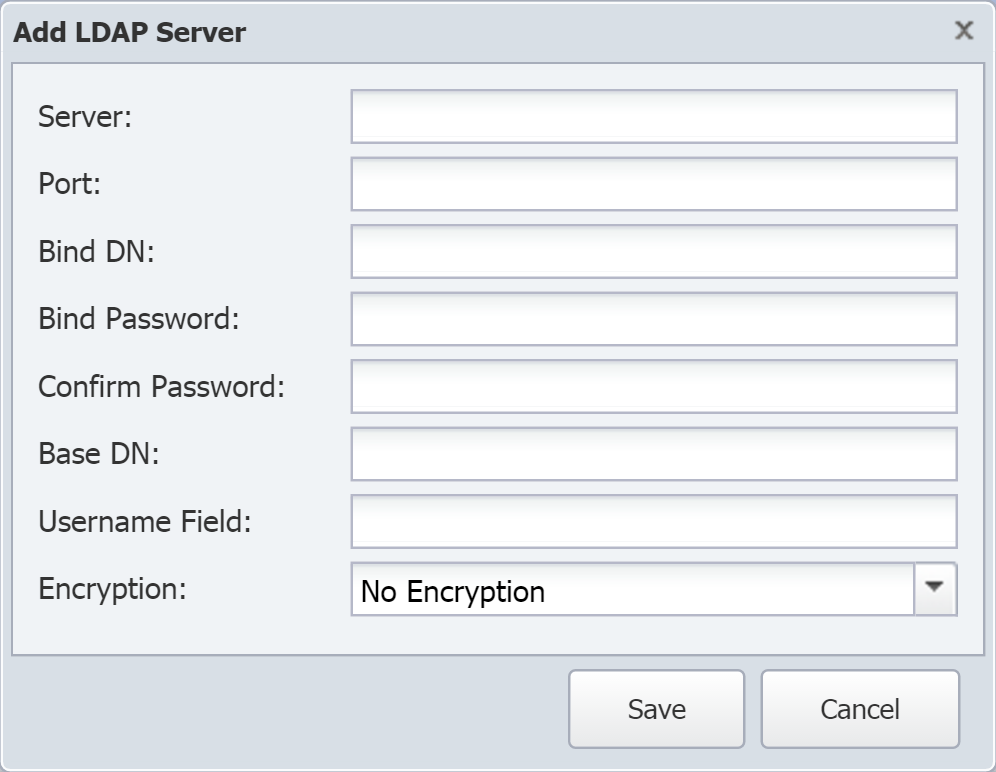
On the User Authentication tab, under LDAP Servers, click Add Server to display the Add LDAP Server pop-up. To edit settings for an existing server, select the server and click
 .
. 
-
In the Server field, enter the host name or IP address of the LDAP server.
-
In the Port field, enter the network port of the LDAP server.
-
In the Bind DN field, enter the user name that SevOne NMS needs to authenticate to the LDAP server.
-
In the Bind Password field, enter the password for the user name (Bind DN) you entered in the previous step. A bind password is not required in LDAP version 3 (LDAPv3), which is the current LDAP version.
-
In the Confirm Password field, reenter the bind password from the previous step.
-
In the Base DN field, enter the base distinguished name that points to the top level of your directory tree.
-
In the Username Field field, enter the user attribute that SevOne NMS should check to find user names (for example, sAMAccountName, uid, or cn).
-
In the Encryption drop-down, select No Encryption, StartTLS, or SSL (LDAPS, dep).
-
Click Save to save the LDAP server settings. Your newly added server should be listed in the LDAP Servers section.
Test Server Connection
Perform the following steps to test the connection to an LDAP server after adding (or editing) it.
-
Under LDAP Servers, select a server.
-
Under Actions, click
 to test the server connection.
to test the server connection.
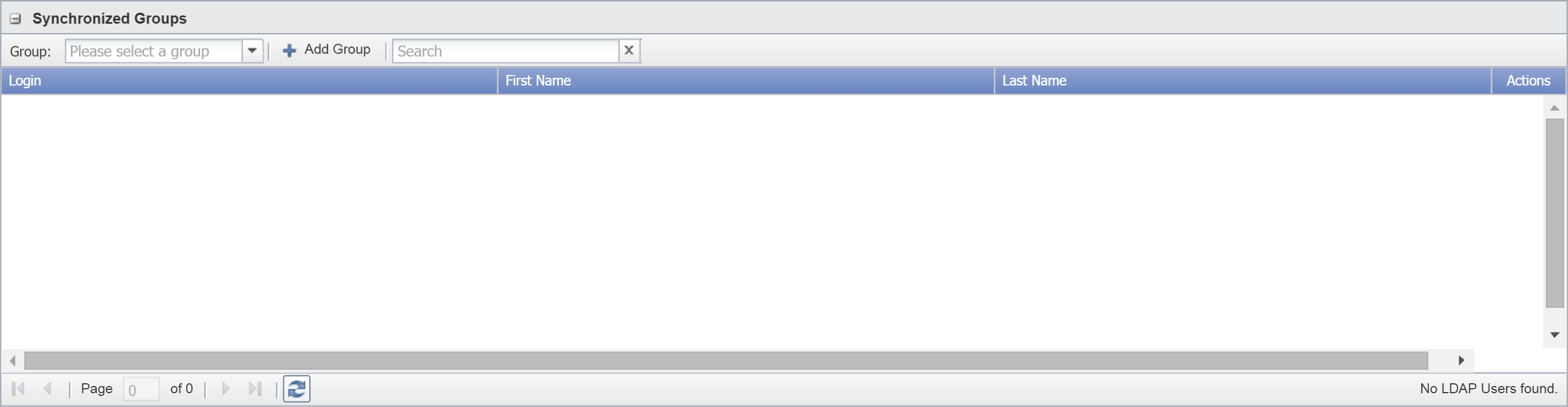
Synchronize Groups
The Synchronized Groups section lets you incorporate groups from your directory and edit users within those groups. LDAP groups are equivalent to SevOne NMS user roles. Perform the following steps to add groups.
-
Under Synchronized Groups, click the Group drop-down and select the server group that you want to associate a particular server to.
-
If you don't see the group you're looking for, click Add Group to display the Add Group pop-up. Then perform the following actions.
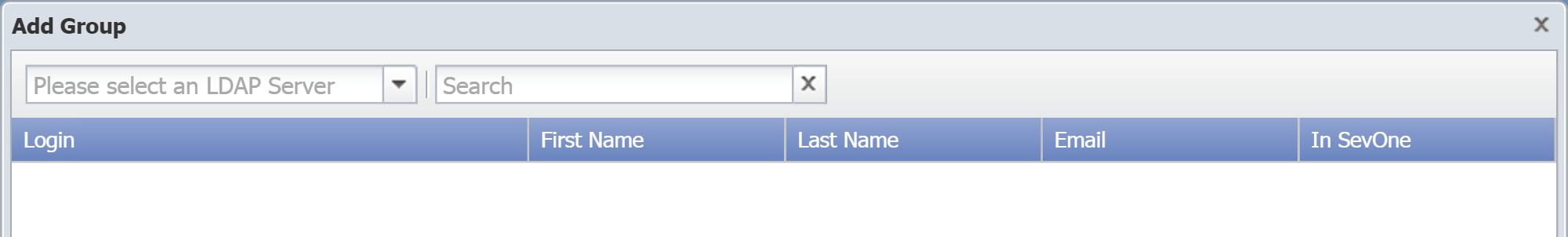
-
Click the drop-down (Please select an LDAP Server) and select a server.
-
In the Search field, enter at least one letter to filter the search results and press Enter. To narrow your search, enter three characters or more.
-
In the list of groups, click + next to the group name to display its members.
-
Select the check box for each group that you want to add.
-
Click Add.
-
-
Now when you click the Group drop-down, you should see the group that you just added. When you select the group, its members will appear in the list below it.
Settings
In the Settings section, you can add a guest user and specify how to treat SSL/TLS certificates. The guest user receives permissions to log in with a valid LDAP user ID, without having a SevOne NMS account.
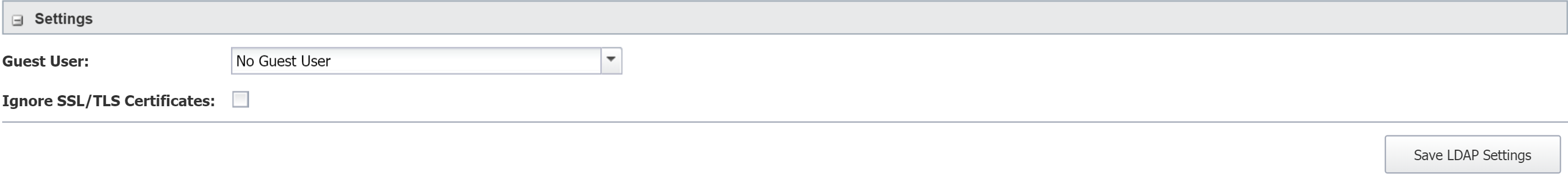
Perform the following steps to manage settings.
-
Click the Guest User drop-down and select a guest user.
-
To ignore certificates, select the Ignore SSL/TLS Certificates check box. We generally don't recommend ignoring certificates.
If you change this setting, you must contact SevOne Support for it to properly take effect.
-
On the lower right of the page, click Save LDAP Settings.
System Authentication
From the System Authentication tab, you can upload root certificates. You'll need to do this if your LDAP server has certificates signed by an unknown CA.
Certificates need to be base64-encoded PEM files.
Upload a Certificate
Perform the following steps to upload a certificate.
-
At the top of the page, select the System Authentication tab.
-
Click Add Certificate to display the Upload SSL/TLS Root Certificates pop-up.
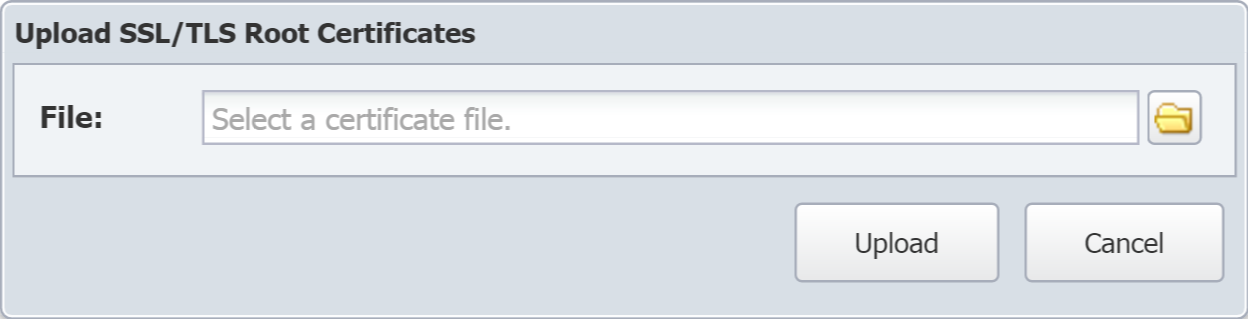
-
Click
 to navigate the file system and select your certificate.
to navigate the file system and select your certificate. -
After selecting the certificate, click Upload.
Certificate Information
The System Authentication tab provides the following information for certificates that have been uploaded.
-
Common Name - The hostname that the certificate is associated with.
-
Organization - The organization that the certificate is associated with.
-
ValidityFrom - The date and time from which the certificate is valid.
-
ValidityTo - The date and time at which the certificate stops being valid.
-
Version - The certificate version number.
-
SerialNumber - The certificate's serial number.
Troubleshooting
Check the basics.
It's a good idea to start with the basics. If you've added a server and the connection test has failed, double-check that all the basic settings are correct. Select the server in question and click  to display the Edit LDAP Server pop-up. Check line-by-line to confirm that the information in the fields is accurate. If you used a bind password, try reentering it to see if that fixes the problem.
to display the Edit LDAP Server pop-up. Check line-by-line to confirm that the information in the fields is accurate. If you used a bind password, try reentering it to see if that fixes the problem.
You uploaded a certificate, and the server connection test fails when using StartTLS or SSL.
There are a few possibilities here:
-
The newly uploaded certificate may not have taken effect yet. Just give it a few minutes and try again. If that doesn't work, proceed to the next step.
-
Something went wrong during the upload. Try uploading your certificate again and wait about five minutes for it to take effect. If that doesn't work, proceed to step 3.
-
There's a problem with your certificate. If there's a problem with the certificate itself, you may need to get another copy of the certificate file. Upload the new certificate file and wait about five minutes for it to take effect. If you're still having problems after that, the original certificate file may be corrupted. If it is, you'll need to get a good certificate file and upload that. Once again, give it about five minutes to take effect.
Terms
|
Authentication |
The process of verifying that someone is who they claim to be. |
|
Authorization |
The process of allowing someone access or information. |
|
Certificate |
A file used to verify that its owner (for example, a server) is who it says it is. |
|
Certificate Authority (CA) |
A trusted third party that issues digital certificates, which certify that the certificate owners are who they say they are. |
|
Encryption |
The process of converting data into a format that can only be read by authorized users. |